August, 2022
now browsing by month
CompTIA CAS-004 dumps: serves all CAS-004 CASP+ exam candidates
The newly updated CompTIA CAS-004 dumps contains 267 exam questions and answers that candidates can study using the CAS-004 dumps PDF and CAS-004 dumps VCE to help you successfully pass the CAS-004 CASP+ exam.
You are welcome to download the latest CompTIA CAS-004 dumps: https://www.leads4pass.com/cas-004.html, Lead4Pass CAS-004 dumps serve all candidates taking the CAS-004 CASP+ exam and guarantee you 100% Successfully passed the CAS-004 CASP+ exam.
Download the CompTIA CAS-004 PDF for free sharing online:
https://drive.google.com/file/d/1gPzIc5NxyzqTe5jbFzvmofpUGr5d4CUr/
https://drive.google.com/file/d/1IbvnTbTz7x2VbxDQ1GHCSEII5xMN55Pn/
Share the latest CompTIA CAS-004 dumps exam questions and answers for free
New Question 1:
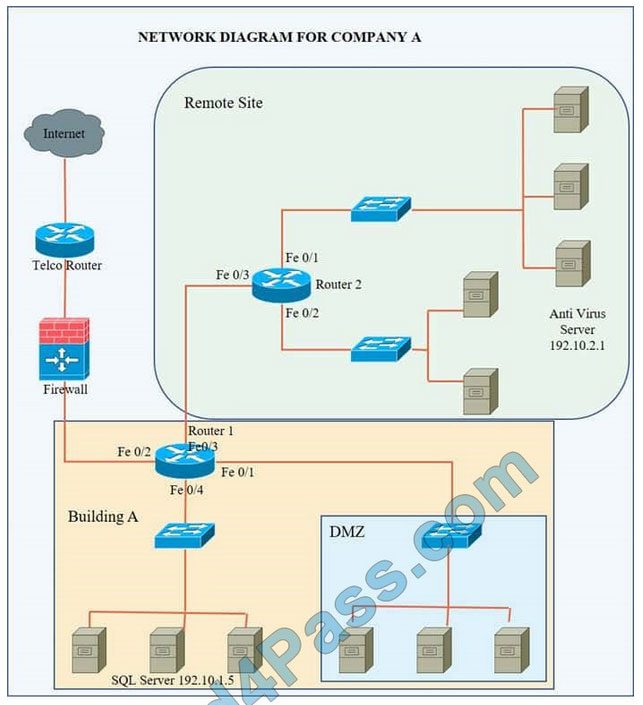
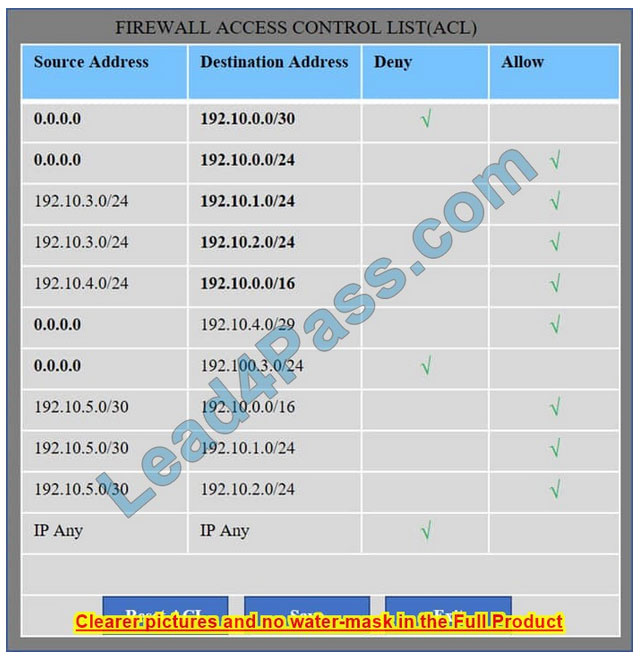
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address. The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and 192.10.2.0/24 for the remote
site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
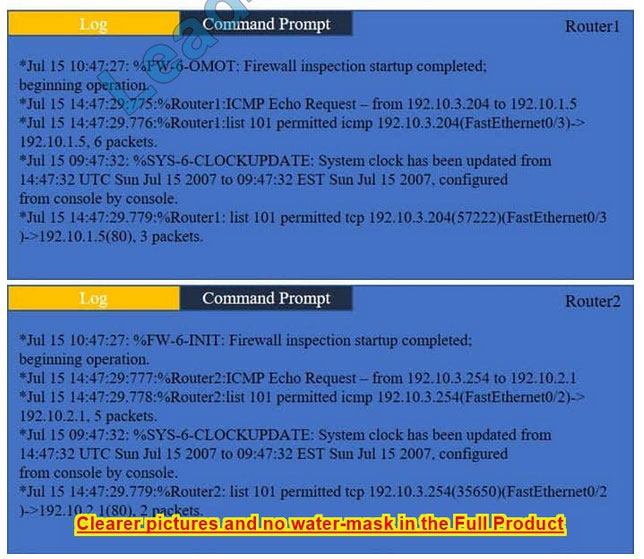
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
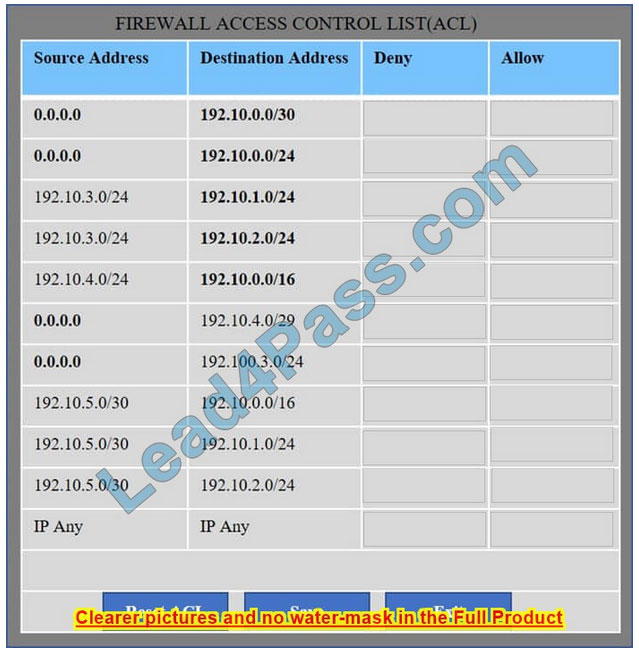
Hot Area:
Correct Answer:
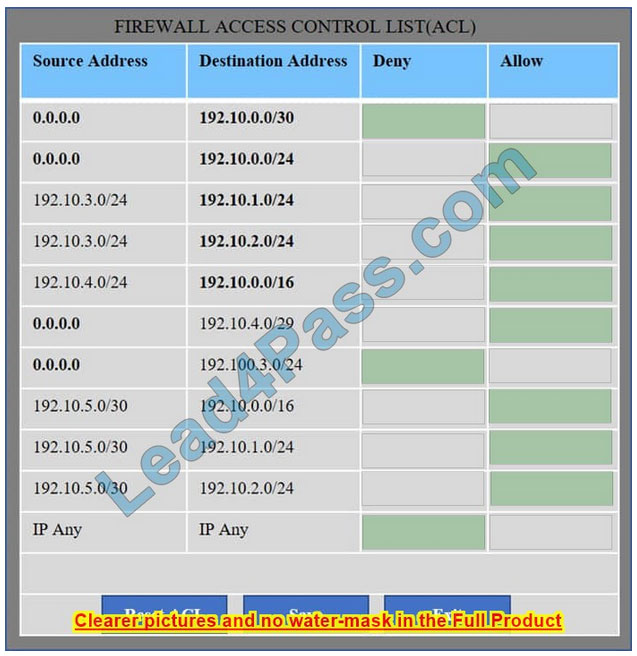
We have traffic coming from two rogue IP addresses: 192.10.3.204 and 192.10.3.254 (both in the 192.10.30.0/24 subnet) going to IPs in the corporate site subnet (192.10.1.0/24) and the remote site subnet (192.10.2.0/24). We need to Deny (block) this traffic at the firewall by ticking the following two checkboxes:
New Question 2:
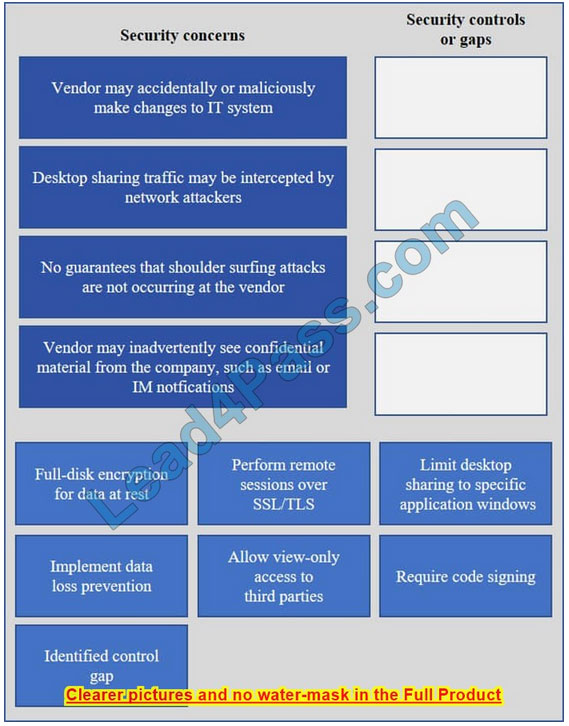
IT staff within a company often conduct remote desktop sharing sessions with vendors to troubleshoot vendor product-related issues. Drag and drop the following security controls to match the associated security concern. Options may be used once or not at all.
Select and Place:
Correct Answer:
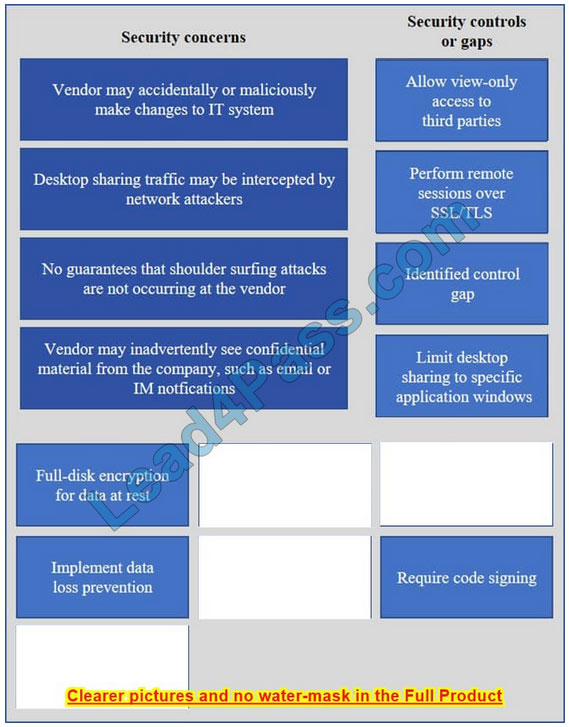
Vendor may accidentally or maliciously make changes to the IT system – Allow view-only access.
With view-only access, the third party can view the desktop but cannot interact with it. In other words, they cannot control the keyboard or mouse to make any changes.
Desktop sharing traffic may be intercepted by network attackers – Use SSL for remote sessions.
SSL (Secure Sockets Layer) encrypts data in transit between computers. If an attacker intercepted the traffic, the data would be encrypted and therefore unreadable to the attacker.
No guarantees that shoulder surfing attacks are not occurring at the vendor – Identified control gap.
Shoulder surfing is where someone else gains information by looking at your computer screen. This should be identified as a risk. A control gap occurs when there are either insufficient or no actions taken to avoid or mitigate a significant risk.
Vendor may inadvertently see confidential material from the company such as email and IMs – Limit desktop session to certain windows.
The easiest way to prevent a third party from viewing your emails and IMs is to close the email and IM application windows for the duration of the desktop sharing session.
New Question 3:
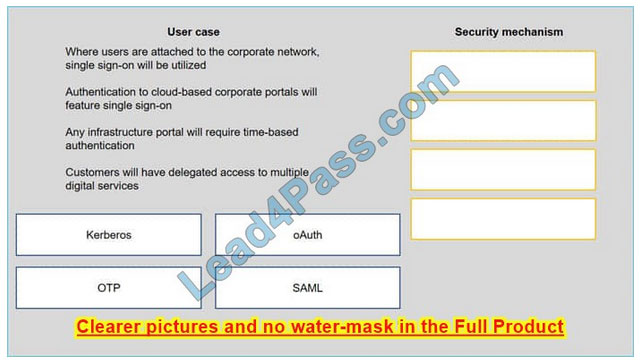
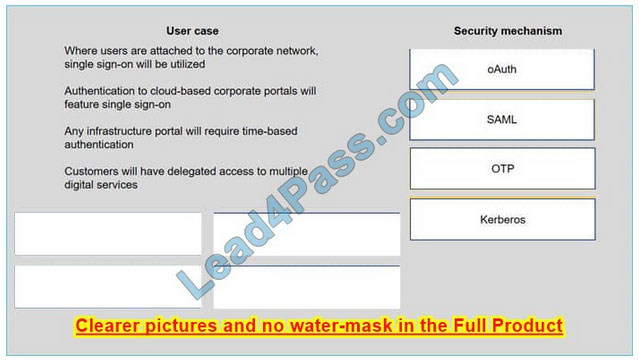
A security consultant is considering authentication options for a financial institution. The following authentication options are available security mechanism to the appropriate use case. Options may be used once.
Select and Place:
Correct Answer:
New Question 4:
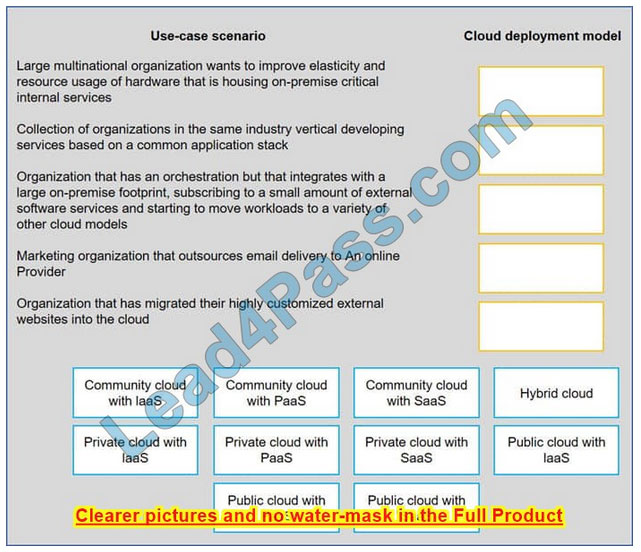
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.
Select and Place:
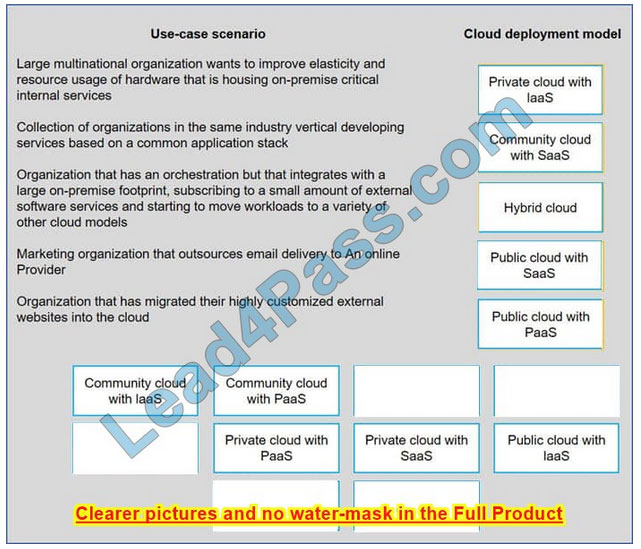
Correct Answer:
New Question 5:
A security administrator must configure the database server shown below the comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.

Select and Place:

Correct Answer:

New Question 6:
DRAG DROP
A vulnerability scan with the latest definitions was performed across Sites A and B.
INSTRUCTIONS
Match each relevant finding to the affected host.
After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:
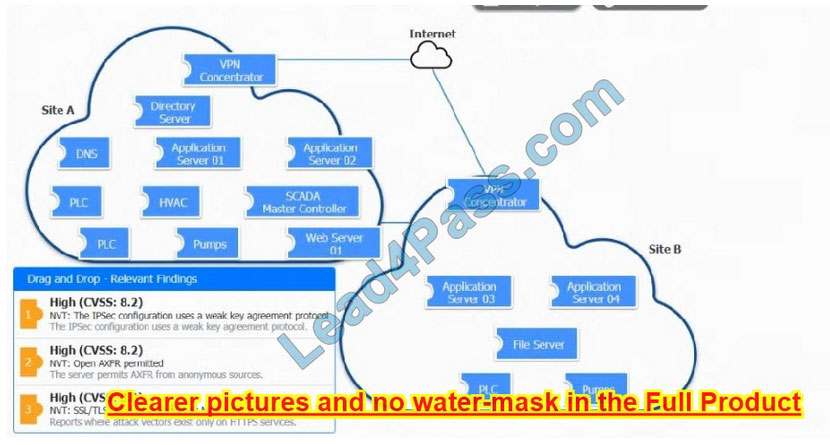
Correct Answer:
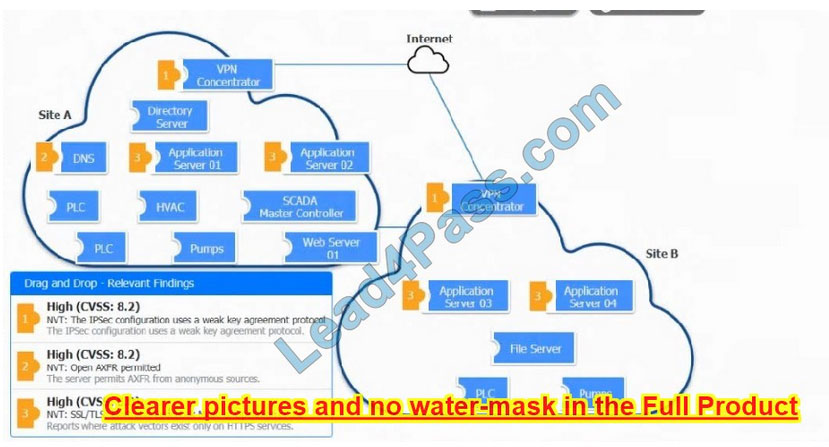
New Question 7:
DRAG DROP
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:
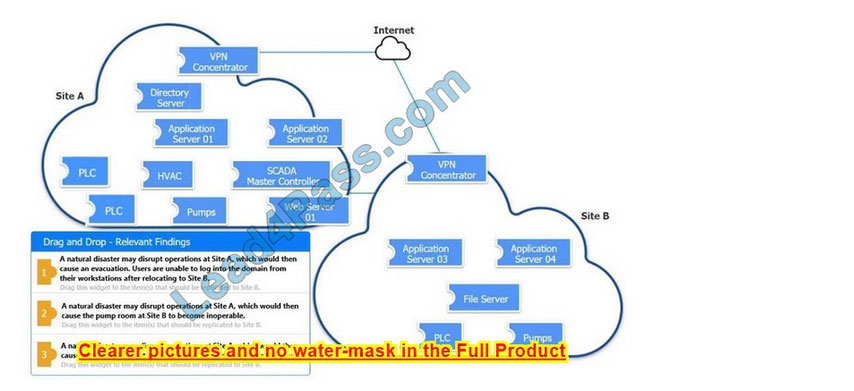
Correct Answer:
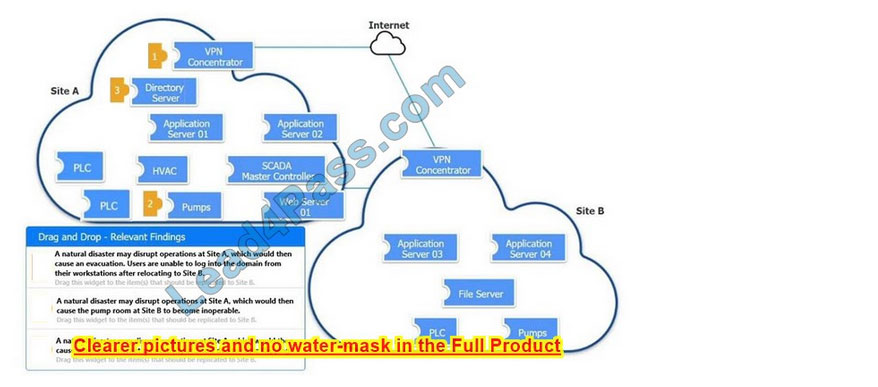
New Question 8:
SIMULATION
Compliance with company policy requires a quarterly review of firewall rules. A new administrator is asked to conduct this review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more
restrictive. Given the following information answer the questions below:
User Subnet: 192.168.1.0/24 Server Subnet: 192.168.2.0/24 Finance Subnet:192.168.3.0/24
Instructions: To perform the necessary tasks, please modify the DST port, Protocol, Action, and/or Rule Order columns. Firewall ACLs are read from the top down
Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.
Check the solution below.
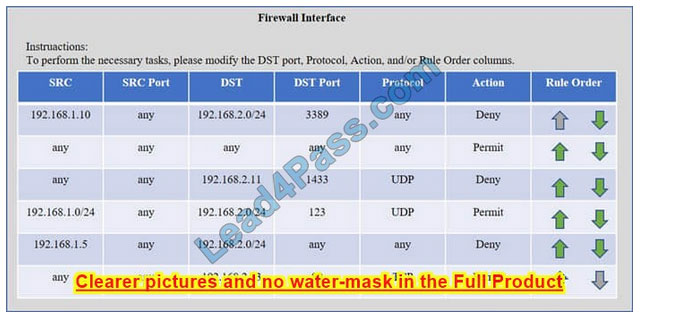
Check the answer below
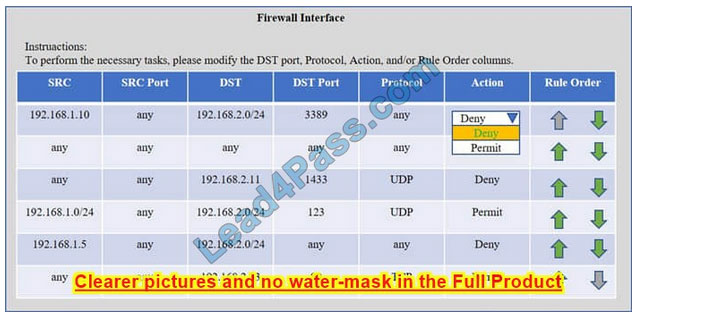
Correct Answer: Check the answer in explanation.
Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
The rule shown in the image below is the rule in question. It is not working because the action is set to Deny.
This needs to be set to Permit.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
The web servers rule is shown in the image below. Port 80 (HTTP) needs to be changed to port 443 for HTTPS (HTTP over SSL).
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
The SQL Server rule is shown in the image below. It is not working because the protocol is wrong. It should be TCP, not UDP.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.
The network time rule is shown in the image below.
However, this rule is not being used because the `any\’ rule shown below allows all traffic and the rule is placed above the network time rule. To block all other traffic, the `any\’ rule needs to be set to Deny, not Permit and the rule needs to be
placed below all the other rules (it needs to be placed at the bottom of the list to the rule is enumerated last).
New Question 9:
SIMULATION
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
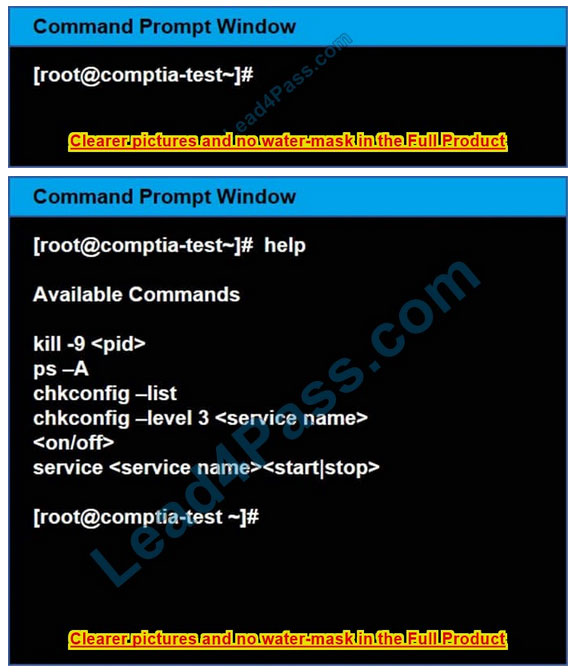
Correct Answer: Check the answer in explanation.
See the below In Order to deactivate web services, database services and print service, we can do following things 1) deactivate its services /etc/init.d/apache2 stop /etc/init.d/mysqld stop 2) close ports for these services Web Server
iptables -I INPUT -p tcp -m tcp –dport 443 -j REJECTservice iptables save Print Server iptables -I INPUT -p tcp -m tcp –dport 631 -j REJECTservice iptables save
Database Server iptables -I INPUT -p tcp -m tcp –dport <> -j REJECTservice iptables save 3) Kill the process any running for the same ps -aef|grep mysql kill -9 <>
New Question 10:
SIMULATION
Correct Answer: Check the answer in explanation.
Please see the below
Step 1: Verify that the certificate is valid or not. In case of any warning message, cancel the download.
Step 2: If certificate issue is not there then, download the file in your system.
Step 3: Calculate the hash value of the downloaded file.
Step 4: Match the hash value of the downloaded file with the one which you selected on the website.
Step 5: Install the file if the hash value matches.
New Question 11:
SIMULATION
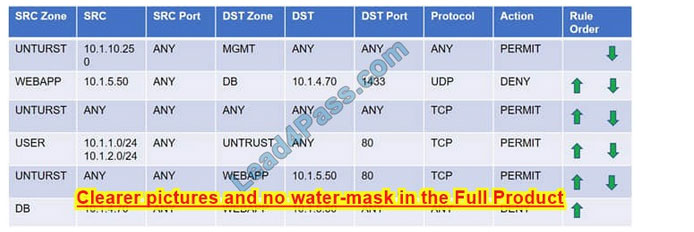
Compliance with company policy requires a quarterly review of firewall rules. You are asked to conduct a review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more secure. Given
the following information perform the tasks listed below:
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24 Web server: 10.1.5.50 MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250
Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation
requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Correct Answer: Check the answer in explanation.
Explanation:
Task 1: A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
In Rule no. 1 edit the Action to Deny to block internet access from the management platform.

Task 2: The firewall must be configured so that the SQL server can only receive requests from the web server. In Rule no. 6 from top, edit the Action to be Permit.

Task 3: The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network. In rule no. 5 from top, change the DST port to Any from 80 to allow all unencrypted traffic.
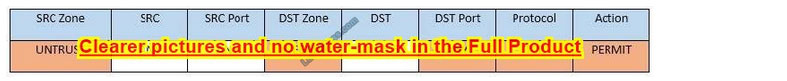
Task 4: Ensure the final rule is an explicit deny
Enter this at the bottom of the access list i.e. the line at the bottom of the rule:

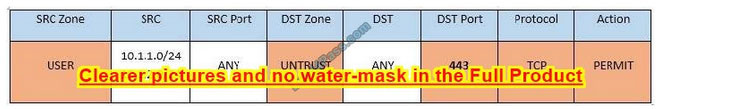
Task 5: Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only. In Rule number 4 from top, edit the DST port to 443 from 80
New Question 12:
SIMULATION
An administrator wants to install a patch to an application.
INSTRUCTIONS
Given the scenario, download, verify, and install the patch in the most secure manner.
The last install that is completed will be the final submission.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
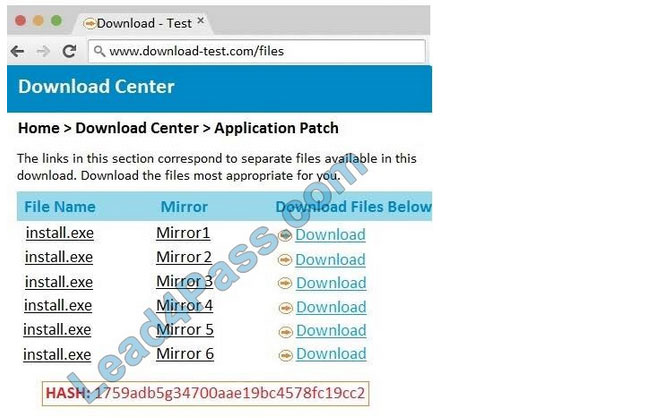
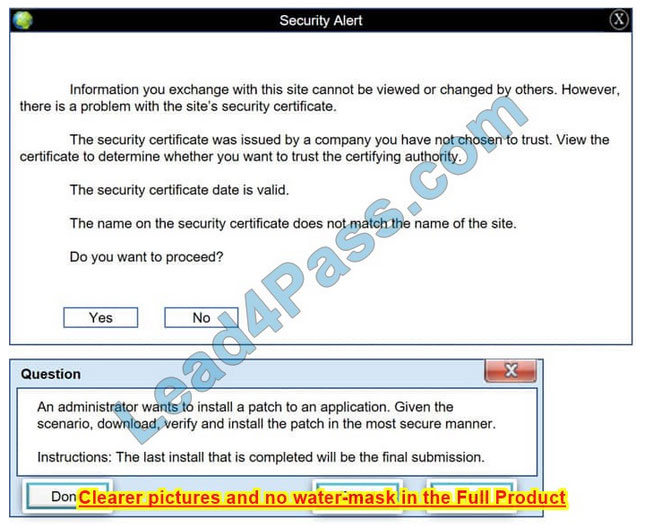
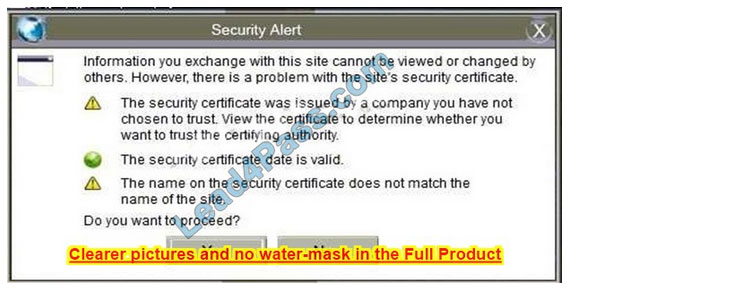
Correct Answer: See the below.
In this case the second link should be used (This may vary in actual exam). The first link showed the following error so it should not be used.
Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown:
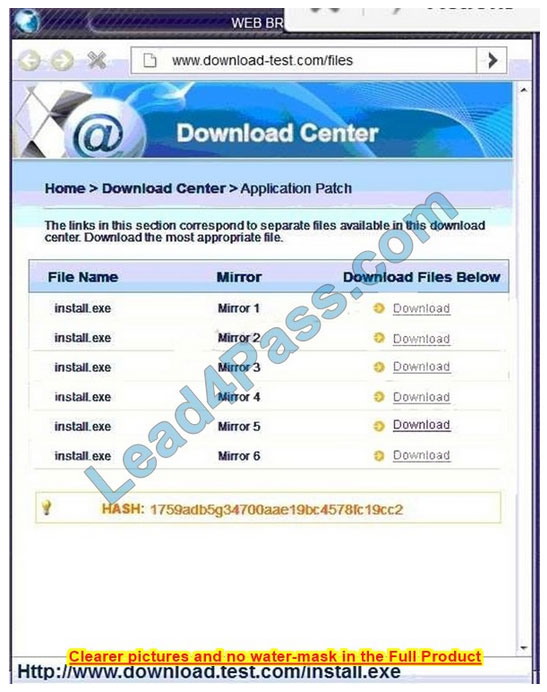
Since we need to do this in the most secure manner possible, they should not be used.
Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as shown. Make sure that the hash matches.
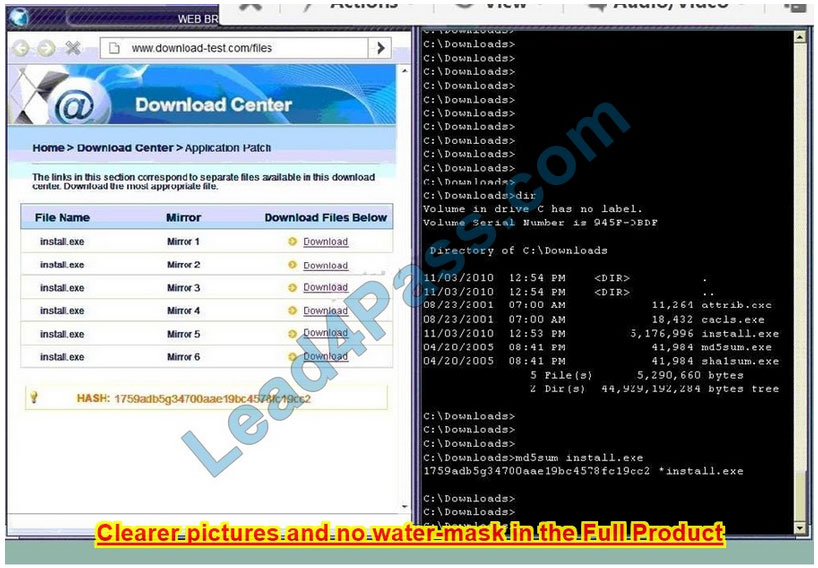
Finally, type in install.exe to install it and make sure there are no signature verification errors.
New Question 13:
SIMULATION
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Correct Answer: See the below.
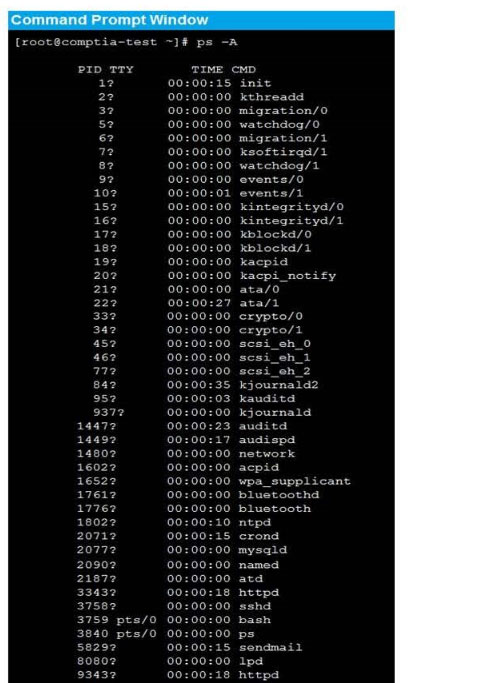
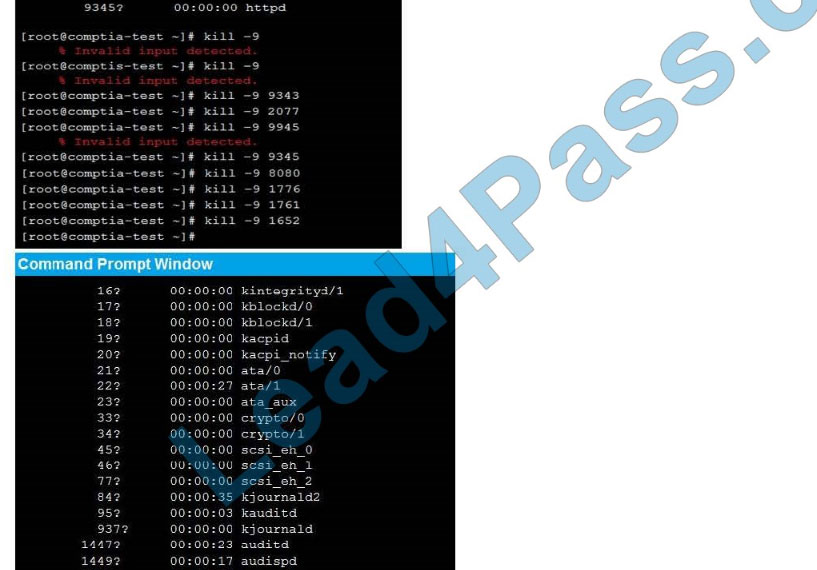
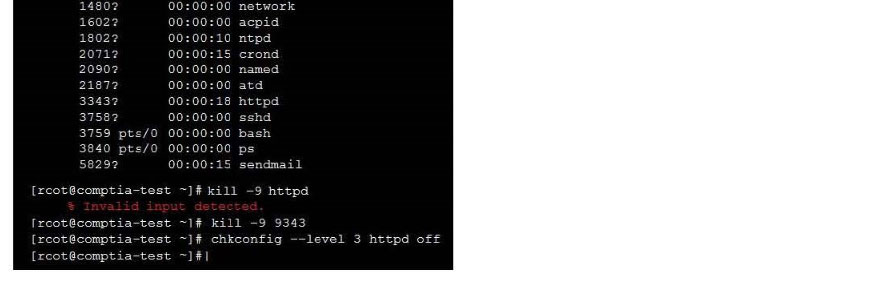

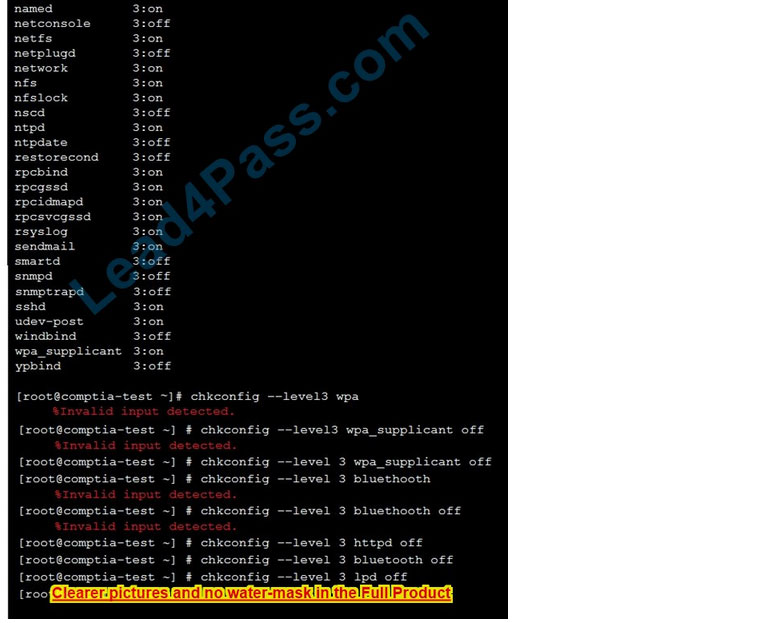
New Question 14:
SIMULATION
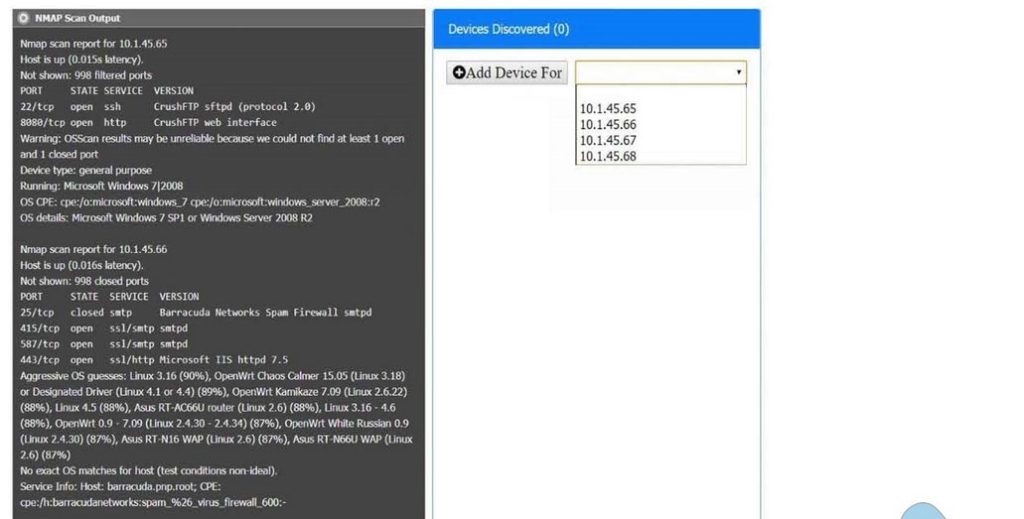
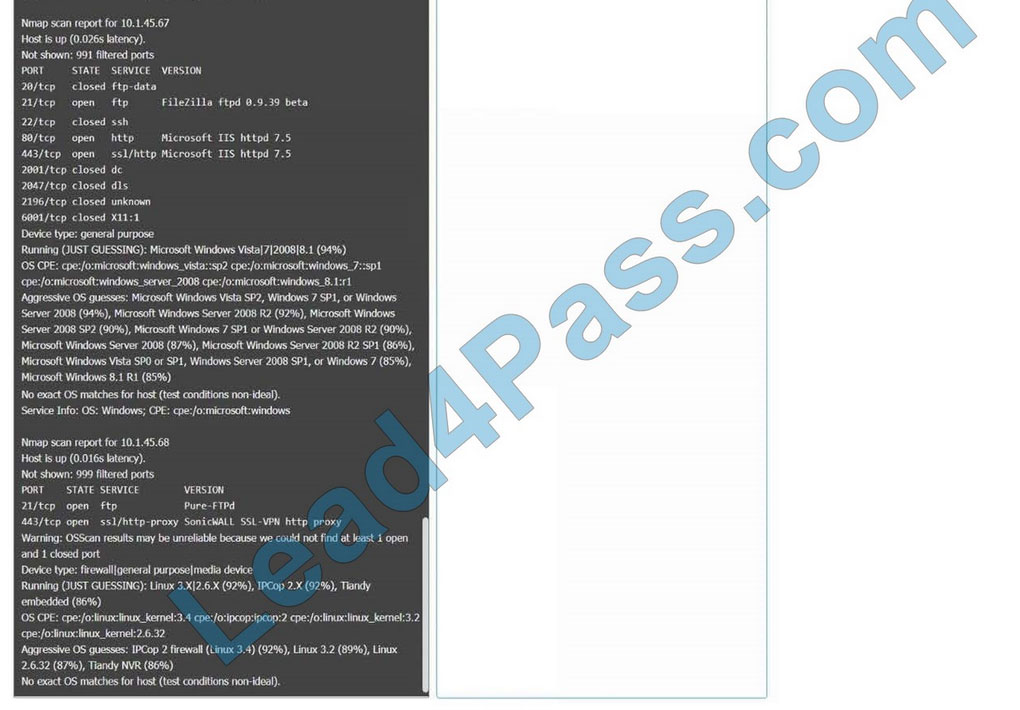
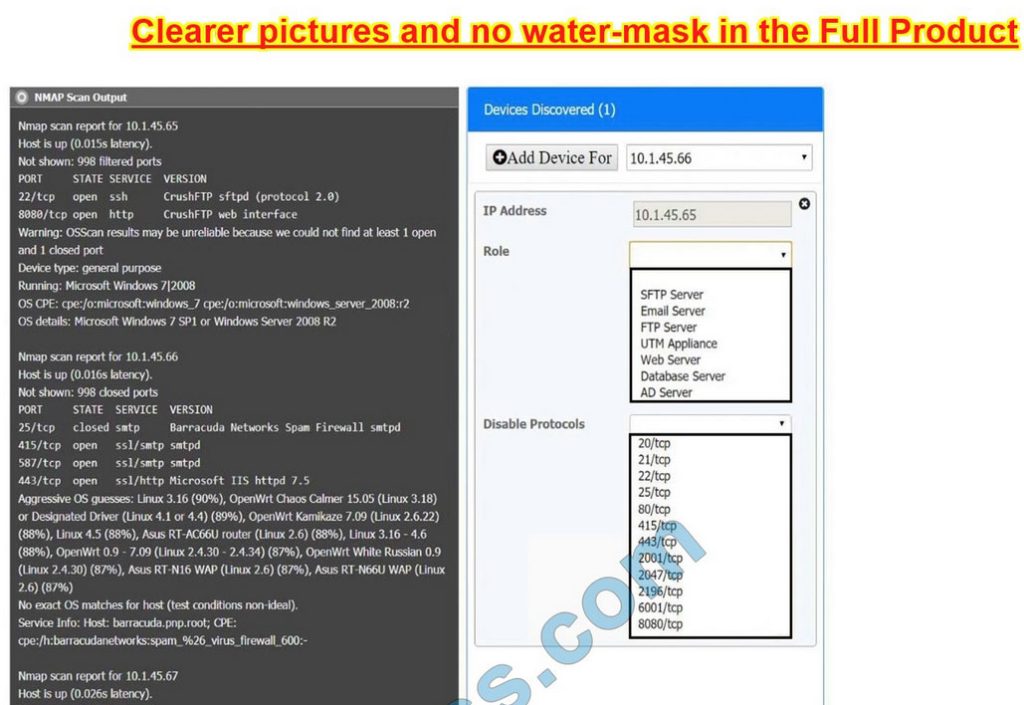
You are a security analyst tasked with interpreting an Nmap scan output from Company A\’s privileged network.
The company\’s hardening guidelines indicate the following:
1.
There should be one primary server or service per device.
2.
Only default ports should be used.
3.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed. For each device found, add a device entry to the Devices Discovered list, with the following information:
1.
The IP address of the device
2.
The primary server or service of the device
3.
The protocol(s) that should be disabled based on the hardening guidelines
To select multiple protocols, use CTRL+CLICK.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
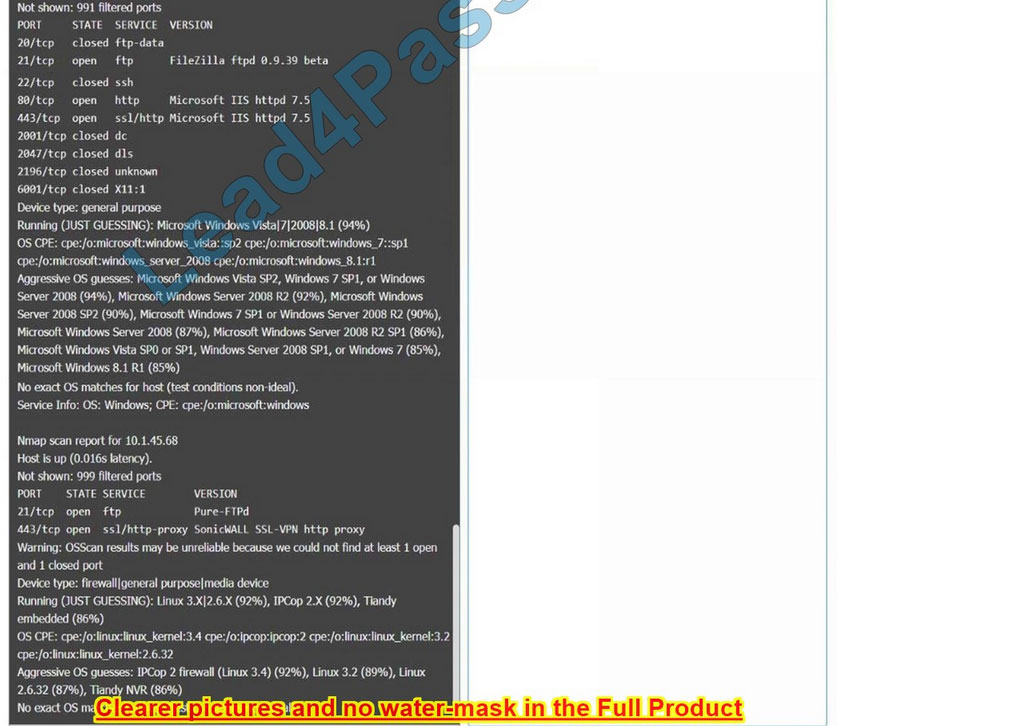
Correct Answer: Check the answer in explanation.
10.1.45.65 – FTP Server – Disable 8080
10.1.45.66 – Email Serve – Disable 25 and 415
10.1.45.67 – Web Server – Disable 21, 80
10.1.45.68 – UTM Appliance – Disable 21
New Question 15:
SIMULATION
A product development team has submitted code snippets for review pnor to release INSTRUCTIONS.
Analyze the code snippets and then select one vulnerability and one fix for each code snippet If at any time you would like to bang back the initial state of the simulation, please click the Reset All button.
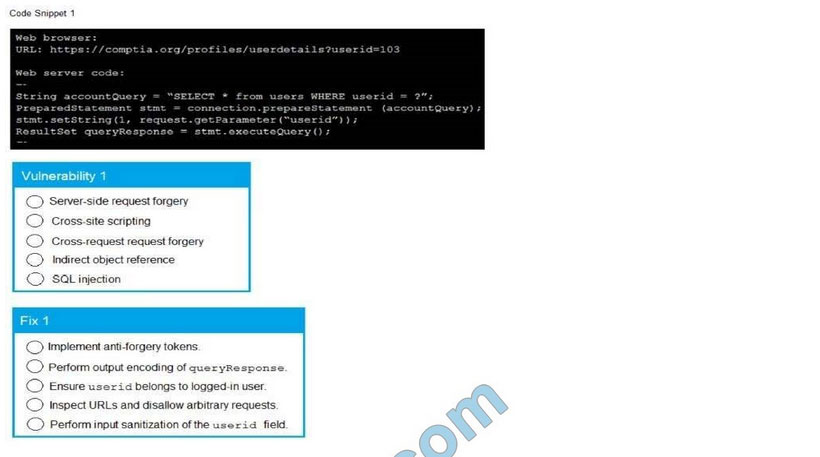
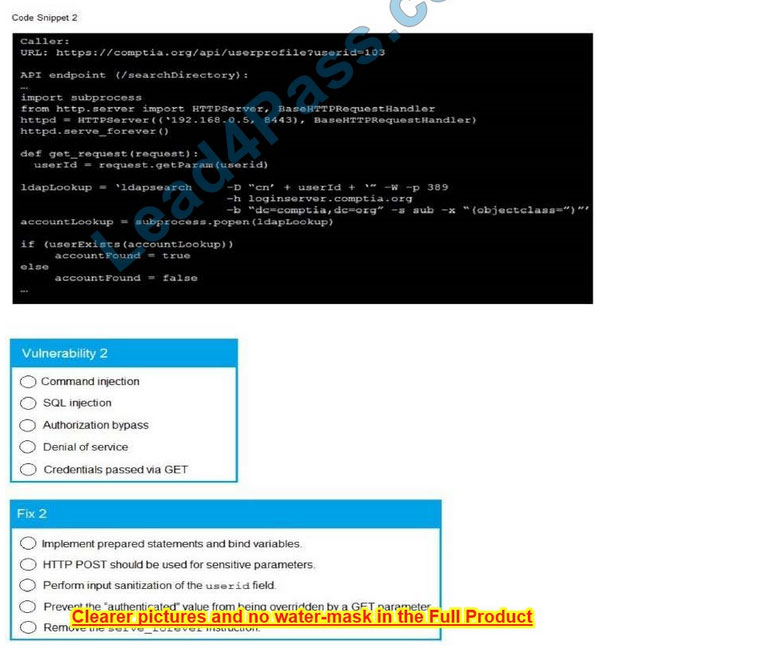
A. Check the answer in below.
Correct Answer: A
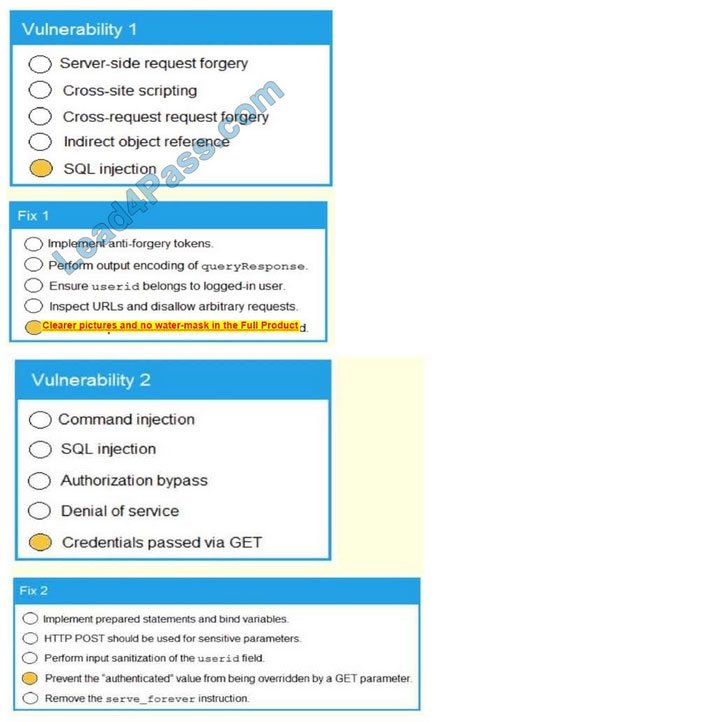
…
Download the CompTIA CAS-004 PDF for free sharing online:
https://drive.google.com/file/d/1gPzIc5NxyzqTe5jbFzvmofpUGr5d4CUr/
https://drive.google.com/file/d/1IbvnTbTz7x2VbxDQ1GHCSEII5xMN55Pn/
The above is only a part of CompTIA CAS-004 dumps exam questions and answers, you can use the above exam questions and answers to improve yourself, not only that, we welcome you to download the latest CompTIA CAS-004 dumps exam questions: https://www.leads4pass.com/cas-004.html (Total Questions: 267 Q&A), help you truly pass the CAS-004 CASP+ exam.
Cisco 300-435 ENAUTO Exam Plan: Using Cisco 300-435 Dumps
Use Cisco 300-435 Dumps for the best exam plan for you to successfully pass the Cisco 300-435 ENAUTO Exam.
Cisco 300-435 Dumps has PDF exam files, and VCE mock exam engine to help you complete the Cisco 300-435 ENAUTO exam plan.
Download Cisco 300-435 Dumps from Lead4Pass https://www.leads4pass.com/300-435.html, enjoy 365 days of free updates, help you save even more, and ultimately help you successfully pass the Cisco 300-435 ENAUTO Exam.
Try Cisco 300-435 Dumps exam questions for free:
Tips: The answer will be announced at the end of the article
Question 1:
What are two characteristics of RPC API calls? (Choose two.)
A. They can be used only on network devices.
B. They use only UDP for communications.
C. Parameters can be passed to the calls.
D. They must use SSL/TLS.
E. They call a single function or service.
Question 2:
Which two actions do Python virtual environments allow users to perform? (Choose two.)
A. Simplify the CI/CD pipeline when checking a project into a version control system, such as Git.
B. Efficiently port code between different languages, such as JavaScript and Python.
C. Run and simulate other operating systems within a development environment.
D. Quickly create any Python environment for testing and debugging purposes.
E. Quickly create an isolated Python environment with module dependencies.
Question 3:
What are two benefits of leveraging Ansible for automation of Cisco IOS XE Software? (Choose two.)
A. Ansible playbooks are packaged and installed on IOS XE devices for automatic execution when an IOS device reboots.
B. All IOS XE operating systems include Ansible playbooks for basic system administration tasks.
C. It is a device-independent method for automation and can be used with any type of device or operating system.
D. Ansible playbooks can be written from the IOS XE EXEC command line to configure the device itself.
E. It does not require any modules of the software except SSH to be loaded on the network device.
Question 4:
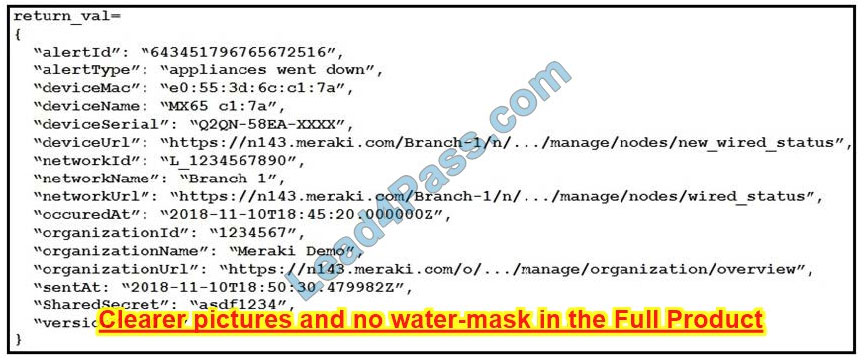
Refer to the exhibit. The task is to create a Python script to display an alert message when a Meraki MX Security Appliance goes down. The exhibit shows sample data that is received. Which Python snippet displays the device name and the time at which the switch went down?
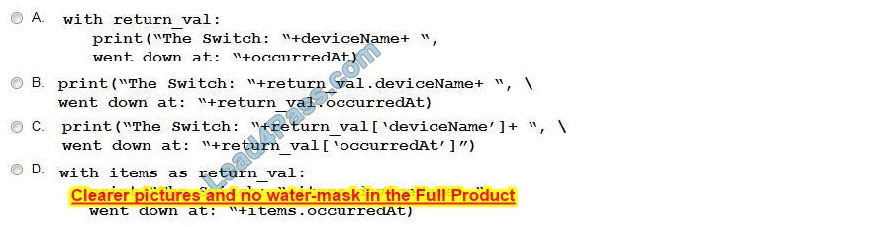
A. Option A
B. Option B
C. Option C
D. Option D
Question 5:

Refer to the exhibit. The goal is to write a Python script to automatically send a message to an external messaging application when a rogue AP is detected on the network.
The message should include the broadcast SSID that is in the alert.
A function called “send_to_application” is created, and this is the declaration:
send_to_application(message)
The exhibit also shows the data that is received by the application and stored in the variable return_val.
Which Python code completes the task?
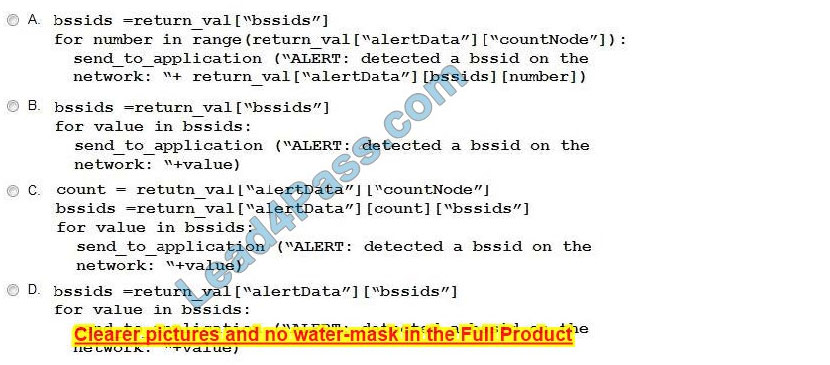
A. Option A
B. Option B
C. Option C
D. Option D
Question 6:
Which two features are foundations of a software-defined network instead of a traditional network? (Choose two.)
A. control plane and data plane are tightly coupled
B. build upon a robust software stack
C. requires device-by-device-level configurations
D. automated through expressed intent to a software controller
E. requires significant physical hardware resources
Question 7:
A new project called “device_status” must be stored in a central Git repository called “device_status” with the first file named “device_status.py”.
The Git repository is created using the account python_programmer. Which set of commands inserts the project into Git?

A. Option A
B. Option B
C. Option C
D. Option D
Question 8:
What are two characteristics of synchronous calls to APIs? (Choose two.)
A. They can be used only with certain programming languages.
B. They make your application less portable, so asynchronous calls are preferred.
C. They can add perceived latency to your application if data is not received.
D. They block until a response is returned from the servers.
E. They do not block while waiting for the API to be processed.
Question 9:

Refer to the exhibit. What is the result when running the Python scripts?
A. s1
B. s2
C. s1, s2, s3
D. s3
Question 10:
An engineer stores source code in a Git repository and is ready to develop a new feature. The production release is stored in the “master” branch.
Which commands create the new feature in a separate branch called “feature” and check out the new version?
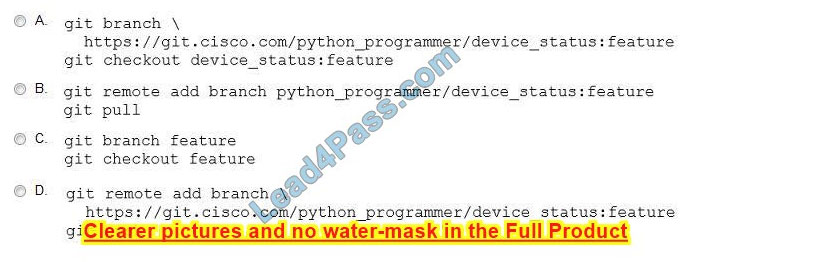
A. Option A
B. Option B
C. Option C
D. Option D
Question 11:

Refer to the exhibit. Which type of YANG container is described by the JSON instance provided?
A. interface-configurations
B. active
C. interface-name
D. description
Question 12:

Refer to the exhibit. Which NETCONF protocol operation is used to interact with the YANG model?
A.
B.
C.
D.
Question 13:

Refer to the exhibit. How many YANG models does the NETCONF operation interact with?
A. one
B. two
C. three
D. four
Question 14:
Which statement describe the difference between OpenConfig and native YANG data models?
A. Native models are designed to be independent of the underlying platform and are developed by vendors and standards bodies, such as the IETF.
B. Native models are developed by individual developers and designed to apply configurations on platforms.
C. OpenConfig models are developed by vendors and designed to integrate to features or configurations that are relevant only to that platform.
D. Native models are developed by vendors and designed to integrate to features or configurations that are relevant only to that platform.
Question 15:
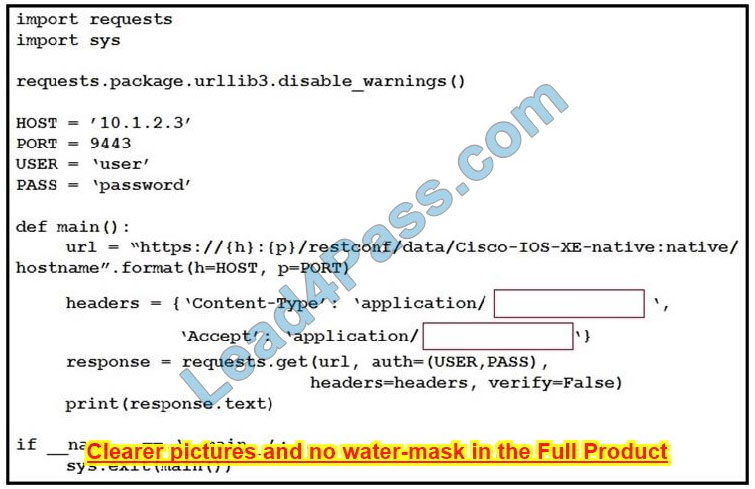
Refer to the exhibit. An engineer creates a Python script using RESTCONF to display hostname information. The code must be completed so that it can be tested. Which string completes the highlighted areas in the exhibit?
A. yang-data+json
B. yang +json
C. yang.data+json
D. JSON
Verify the answer:
| Numbers: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | AC | DE | AC | B | A | BD | A | CE | B | C | A | A | A | A | A |
Lead4Pass provides the perfect Cisco 300-435 ENAUTO exam plan, you just need to practice the complete Cisco 300-435 Exam Dumps https://www.leads4pass.com/300-435.html (122 Q&A), you are guaranteed 100% successful pass Cisco 300-435 ENAUTO exam.
Latest 2V0-71.21 dumps: Preparing for the Professional VMware Application Modernization exam
We confidently tell Exam Professional VMware Application Modernization candidates: that VMware 2V0-71.21 dumps have been updated to be the best material for you to take the Professional VMware Application Modernization exam and guarantee you 100% success in passing the exam.
Download the 2V0-71.21 dumps prepared by Lead4Pass for you https://www.leads4pass.com/2v0-71-21.html, then practice the 55 newly updated VMware 2V0-71.21 exam questions, then keep a good attitude to take the actual exam, Finally, you are sure to successfully pass the Professional VMware Application Modernization exam.
You can try the following VMware 2V0-71.21 exam questions online first:
Tips: The answer will be announced at the end of the article
QUESTION 1:
Which command is used to upgrade a Tanzu Kubernetes Grid Cluster (TKG) to a different kubernetes version?
A. tkg cluster upgrade –k8s-version
B. tkg upgrade cluster –kubernetes-version
C. tkg cluster upgrade –kubernetes-version
D. tkg upgrade cluster –version
QUESTION 2:
What is the command to find out the available node base operating system images?
A. kubectl get nodes
B. kubectl cluster-info
C. kubectl get virtualmachineclasses
D. kubectl get virtualmachineimages
QUESTION 3:
An architect is designing the infrastructure for multiple applications and needs to ensure isolation and control over resources and permissions assigned to each application team.
Which is the easiest and least expensive way to satisfy these requirements?
A. Use a dedicated Supervisor Cluster per application
B. Use dedicated vSphere Namespace per application
C. Use dedicated vSphere Pod per application
D. Use dedicated Kubernetes Deployments per each application
QUESTION 4:
Refer to the exhibit.
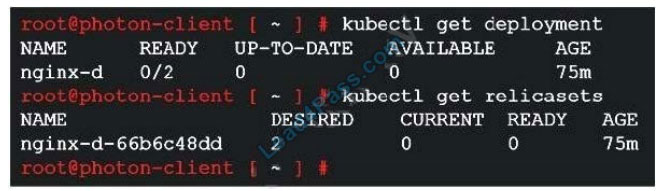
A developer deployed Nginx with 2 replicas on a new Tanzu Kubernetes Grid cluster, but the deployment did not move to a ready state.
What is the next step to troubleshoot?
A. kubectl describe pods
B. kubectl describe replicasets
C. kubectl get pods
D. kubectl get errors
QUESTION 5:
What are the pre-requisites for installing the Harbor registry in Tanzu Kubernetes Grid (TKG)?
A. Install Harbor helm from vCenter.
B. Deploy a management cluster, download and install the TKG extensions and Carvel tools.
C. Deploy a management cluster, launch the Harbor installation wizard.
D. Deploy a management cluster and install Tanzu Kubernetes Grid extensions.
QUESTION 6:
What is the MINIMUM required version of vSphere to install Tanzu Kubernetes Grid?
A. 6.0 Update 1
B. 6.5 Update 2
C. 6.7 Update 1
D. 6.7 Update 3
QUESTION 7:
Refer to the exhibit.
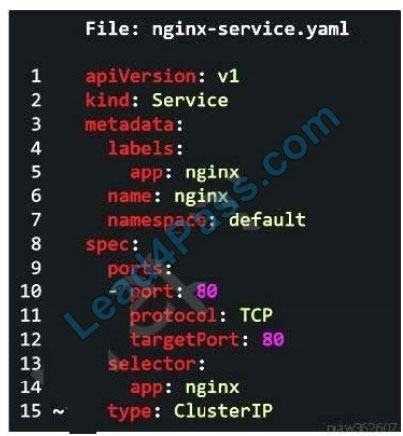
Which two options can be modified in order to expose Nginx app using Ingress Controller? (Choose two.)
A. Change type to IngressController
B. Change type to LoadBalancer
C. Change type to NodePort
D. Change type to HostPort
E. Change type to AntreaCni
QUESTION 8:
On VMware vSphere with Tanzu, which attribute identifies the etcd Leader node using the vSphere Client?
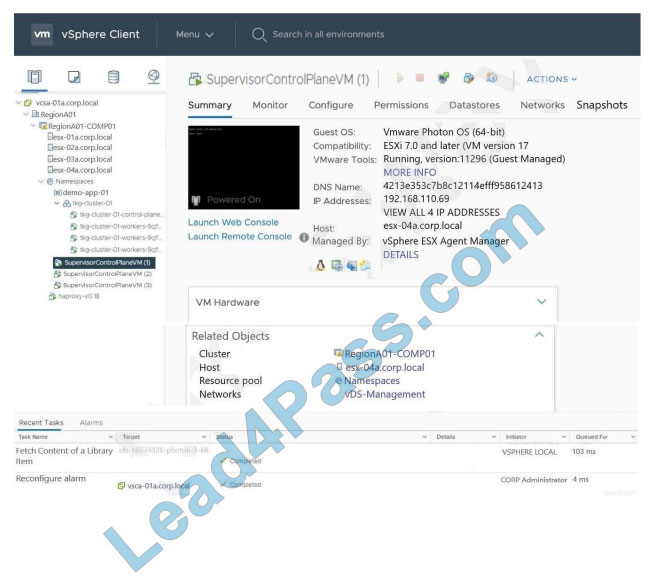
A. amount of memory resources
B. number of Networks
C. number of IP addresses
D. amount of compute resources
QUESTION 9:
What is the period of time to consider DISCONNECTED state for a cluster in Tanzu Mission Control?
A. 3 minutes
B. 1 minute
C. 2 minutes
D. 5 minutes
QUESTION 10:
Which upgrade method can be used for an ‘in-place’ Kubernetes update?
A. Run “kubectl patch” command against a Tanzu Kubernetes cluster
B. Change the VirtualMachineClass on a Tanzu Kubernetes cluster
C. Change the number of control plane nodes
D. Change the StorageClass on a Tanzu Kubernetes cluster
QUESTION 11:
How are Tanzu Kubernetes clusters upgraded?
A. Deploy a new cluster with upgraded Kubernetes release
B. Rolling upgrades
C. Clusters are only upgraded offline
D. In-place upgrade for each node
QUESTION 12:
Which two roles are required to attach clusters in Tanzu Mission Control? (Choose two.)
A. cluster.attach.admin
B. clustergroup.attach.admin
C. clustergroup.edit
D. clusters.admin
E. cluster.admin
QUESTION 13:
Which is the correct statement describing the characteristic of a pod?
A. Pod is the smallest entity managed by Docker.
B. Pod can contain only one container.
C. Containers in a pod start and stop together.
D. Pod is deployed directly on the virtual machine.
……
Verify the answer:
| Numbers: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| Answers: | B | A | B | A | B | D | AD | C | A | A | B | CE | C |
[Google Drive] You can also download VMware 2V0-71.21 exam questions and answers online: https://drive.google.com/file/d/1TNVykBrtbz0UysuhU3DRe6nN8LCQe1oa/
The above VMware 2V0-71.21 exam questions are only to help you warm up, then you should practice the latest and complete 2V0-71.21 exam questions: https://www.leads4pass.com/2v0-71-21.html (55 Q&A), guarantee you’re first trying Successfully passed the Professional VMware Application Modernization exam.