CompTIA
now browsing by category
CompTIA CAS-004 CASP+ Exam Solutions | Latest CAS-004 Dumps
Lead4Pass CAS-004 Dumps contains 406 latest exam questions and answers, covering more than 90% of CompTIA CAS-004 “CompTIA Advanced Security Practitioner (CASP+)” actual exam questions! For your best Exam Solutions.
Lead4Pass CAS-004 exam questions and answers are updated throughout the year! Guaranteed to be available anytime! Download CAS-004 Dumps: https://www.leads4pass.com/cas-004.html
One-time use 365 days free update! You can also choose the learning method that suits you according to your learning habits: PDF and VCE learning formats are provided to help you learn easily and pass CompTIA CAS-004 CASP+ Exam successfully.
Here you can always get more: Lead4Pass CAS-004 dumps page provides download free Demo for you to experience, you can also participate in the following online practice tests
Latest CompTIA CAS-004 dumps Exam Questions
| From | Number of exam questions | Associated certification | Last update | Online Download |
| Lead4Pass | 13 | CompTIA Advanced Security Practitioner | CAS-004 dumps | CAS-004 PDF |
NEW QUESTION 1:
A company is migrating from company-owned phones to a BYOD strategy for mobile devices. The pilot program will start with the executive management team and be rolled out to the rest of the staff in phases. The company\’s Chief Financial Officer loses a phone multiple times a year.
Which of the following will MOST likely secure the data on the lost device?
A. Require a VPN to be active to access company data.
B. Set up different profiles based on the person\’s risk.
C. Remotely wipe the device.
D. Require MFA to access company applications.
Correct Answer: C
NEW QUESTION 2:
A review of the past year\’s attack patterns shows that attackers stopped reconnaissance after finding a susceptible system to compromise.
The company would like to find a way to use this information to protect the environment while
still gaining valuable attack information.
Which of the following would be BEST for the company to implement?
A. A WAF
B. An IDS
C. A SIEM
D. A honeypot
Correct Answer: D
Reference: https://www.kaspersky.com/resource-center/threats/what-is-a-honeypot
NEW QUESTION 3:
Leveraging cryptographic solutions to protect data that is in use ensures the data is encrypted:
A. when it is passed across a local network.
B. in memory during processing
C. when it is written to a system\’s solid-state drive.
D. by an enterprise hardware security module.
Correct Answer: B
NEW QUESTION 4:
A security analyst receives an alert from the SIEM regarding unusual activity on an authorized public SSH jump server.
To further investigate, the analyst pulls the event logs directly from /var/log/auth.log: graphic.ssh_auth_log.
Which of the following actions would BEST address the potential risks of the activity in the logs?
A. Alerting the misconfigured service account password
B. Modifying the AllowUsers configuration directive
C. Restricting external port 22 access
D. Implementing host-key preferences
Correct Answer: B
NEW QUESTION 5:
An organization wants to perform a scan of all its systems against best-practice security configurations.
Which of the following SCAP standards, when combined, will enable the organization to view each of the configuration checks in a machine-readable checklist format for fill automation? (Choose two.)
A. ARF
B. XCCDF
C. CPE
D. CVE
E. CVSS
F. OVAL
Correct Answer: BF
Reference: https://www.govinfo.gov/content/pkg/GOVPUB-C13-9ecd8eae582935c93d7f410e955dabb6/pdf/GOVPUB-C139ecd8eae582935c93d7f410e955dabb6.pdf (p.12)
NEW QUESTION 6:
A software company is developing an application in which data must be encrypted with a cipher that requires the following:
1.
Initialization vector
2.
Low latency
3.
Suitable for streaming
Which of the following ciphers should the company use?
A. Cipher feedback
B. Cipher block chaining message authentication code
C. Cipher block chaining
D. Electronic codebook
Correct Answer: C
Reference: https://www.sciencedirect.com/topics/computer-science/symmetric-cipher
NEW QUESTION 7:
Ann. a user, brings her laptop to an analyst after noticing it has been operating very slowly. The security analyst examines the laptop and obtains the following output: Which of the following will the analyst most likely use NEXT?
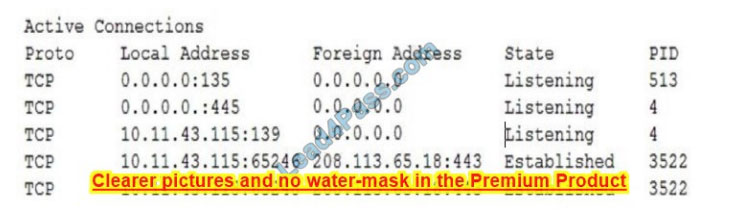
A. Process explorer
B. Vulnerability scanner
C. Antivirus
D. Network enumerator
Correct Answer: B
NEW QUESTION 8:
A company\’s product site recently had failed API calls, resulting in customers being unable to check out and purchase products. This type of failure could lead to the loss of customers and damage to the company\’s reputation in the market.
Which of the following should the company implement to address the risk of system unavailability?
A. User and entity behavior analytics
B. Redundant reporting systems
C. A self-healing system
D. Application controls
Correct Answer: D
NEW QUESTION 9:
A Chief Information Officer is considering migrating all company data to the cloud to save money on expensive SAN storage.
Which of the following is a security concern that will MOST likely need to be addressed during migration?
A. Latency
B. Data Exposure
C. Data loss
D. Data dispersion
Correct Answer: B
NEW QUESTION 10:
A company publishes several APIs for customers and is required to use keys to segregate customer data sets.
Which of the following would be the BEST to use to store customer keys?
A. A trusted platform module
B. A hardware security module
C. A localized key store
D. A public key infrastructure
Correct Answer: B
Reference: https://developer.android.com/studio/publish/app-signing
NEW QUESTION 11:
SIMULATION
A product development team has submitted code snippets for review prior to the release of INSTRUCTIONS.
Analyze the code snippets and then select one vulnerability and one fix for each code snippet If at any time you would like to bang back the initial state of the simulation, please click the Reset All button.
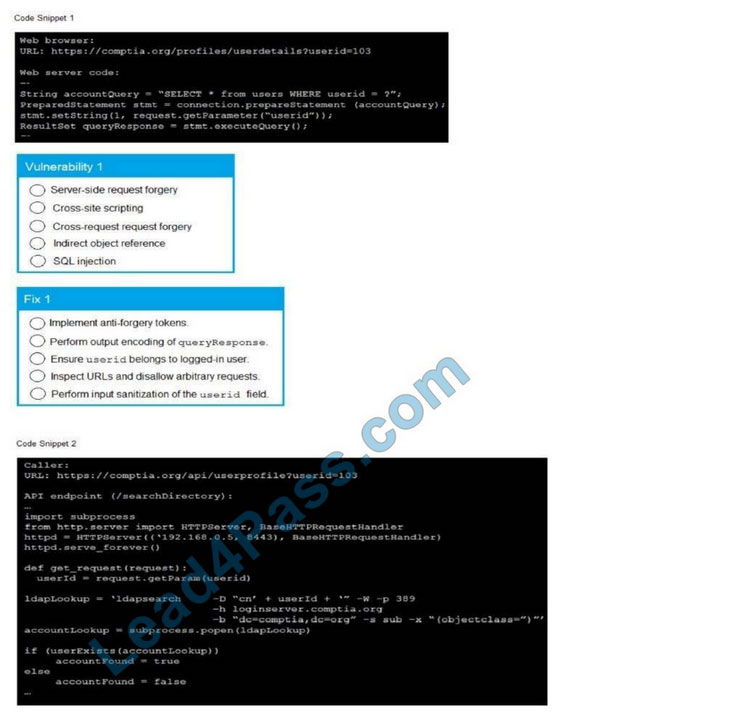

A. Check the answer in the explanation below.
Correct Answer: A
NEW QUESTION 12:
A security auditor needs to review the manner in which an entertainment streaming device operates The auditor is analyzing the output of a port scanning tool to determine the next steps in the security review. Given the following log output:
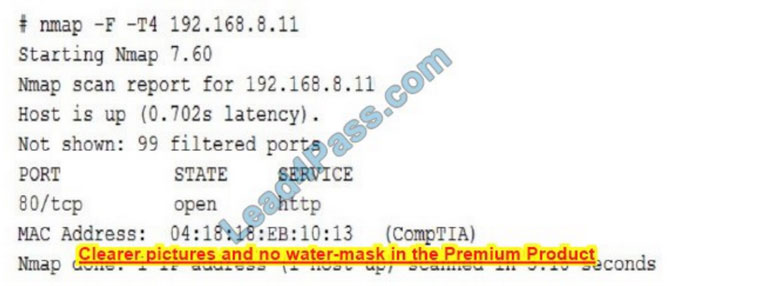
The best option for the auditor to use NEXT is:
A. a SCAP assessment
B. reverse engineering
C. fuzzing
D. network interception
Correct Answer: A
NEW QUESTION 13:
A company has decided to purchase a license for software that is used to operate a mission-critical process. The third-party developer is new to the industry but is delivering what the company needs at this time.
Which of the following BEST describes the reason why utilizing a source code escrow will reduce the operational risk to the company if the third party stops supporting the application?
A. The company will have access to the latest version to continue development.
B. The company will be able to force the third-party developer to continue support.
C. The company will be able to manage the third-party developer\’s development process.
D. The company will be paid by the third-party developer to hire a new development team.
Correct Answer: A
…
Lead4Pass CAS-004 Dumps contains 406 latest exam questions and answers, one-time use enjoys free updates for 365 days! It also provides PDF and VCE multiple learning formats to assist you in easily learning and passing the CompTIA CAS-004 CASP+ Exam!
Use CompTIA CAS-004 CASP+ Exam Solutions: Download CAS-004 dumps with PDF and VCE: https://www.leads4pass.com/cas-004.html, to help you pass the exam 100% successfully.
CompTIA CAS-004 dumps: serves all CAS-004 CASP+ exam candidates
The newly updated CompTIA CAS-004 dumps contains 267 exam questions and answers that candidates can study using the CAS-004 dumps PDF and CAS-004 dumps VCE to help you successfully pass the CAS-004 CASP+ exam.
You are welcome to download the latest CompTIA CAS-004 dumps: https://www.leads4pass.com/cas-004.html, Lead4Pass CAS-004 dumps serve all candidates taking the CAS-004 CASP+ exam and guarantee you 100% Successfully passed the CAS-004 CASP+ exam.
Download the CompTIA CAS-004 PDF for free sharing online:
https://drive.google.com/file/d/1gPzIc5NxyzqTe5jbFzvmofpUGr5d4CUr/
https://drive.google.com/file/d/1IbvnTbTz7x2VbxDQ1GHCSEII5xMN55Pn/
Share the latest CompTIA CAS-004 dumps exam questions and answers for free
New Question 1:
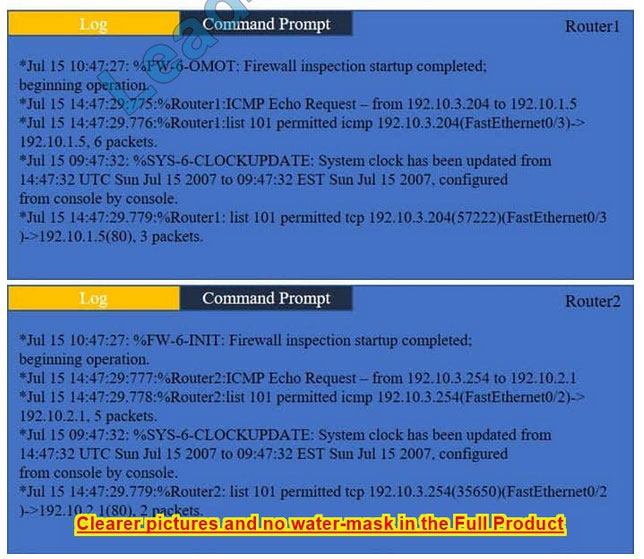
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address. The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and 192.10.2.0/24 for the remote
site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
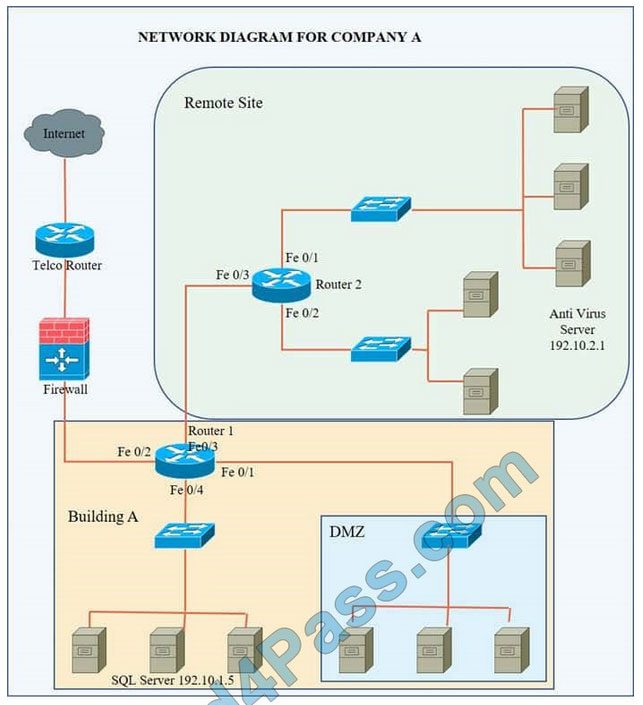
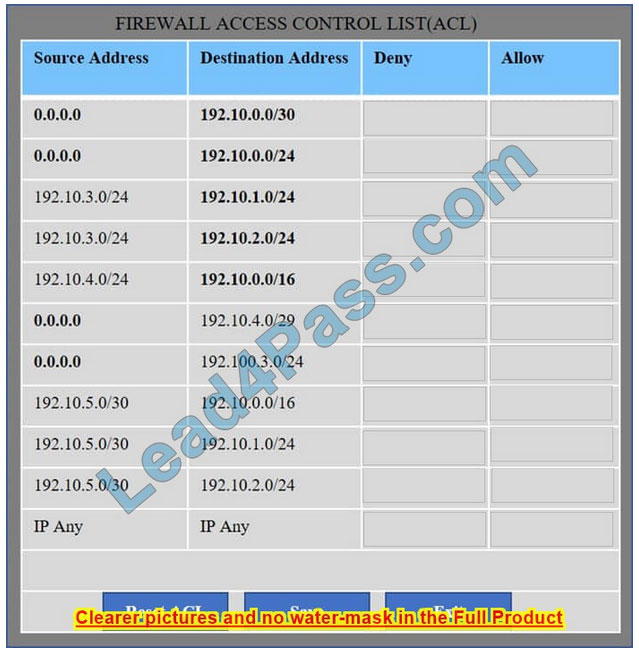
Hot Area:
Correct Answer:
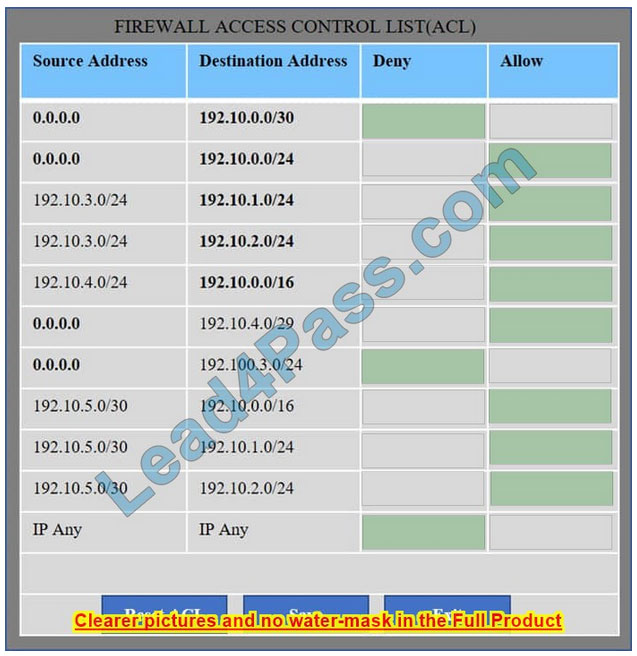
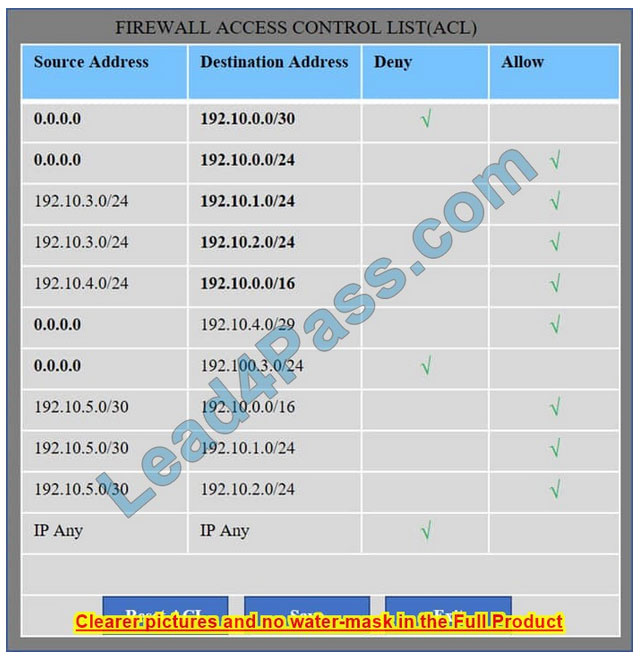
We have traffic coming from two rogue IP addresses: 192.10.3.204 and 192.10.3.254 (both in the 192.10.30.0/24 subnet) going to IPs in the corporate site subnet (192.10.1.0/24) and the remote site subnet (192.10.2.0/24). We need to Deny (block) this traffic at the firewall by ticking the following two checkboxes:
New Question 2:
IT staff within a company often conduct remote desktop sharing sessions with vendors to troubleshoot vendor product-related issues. Drag and drop the following security controls to match the associated security concern. Options may be used once or not at all.
Select and Place:
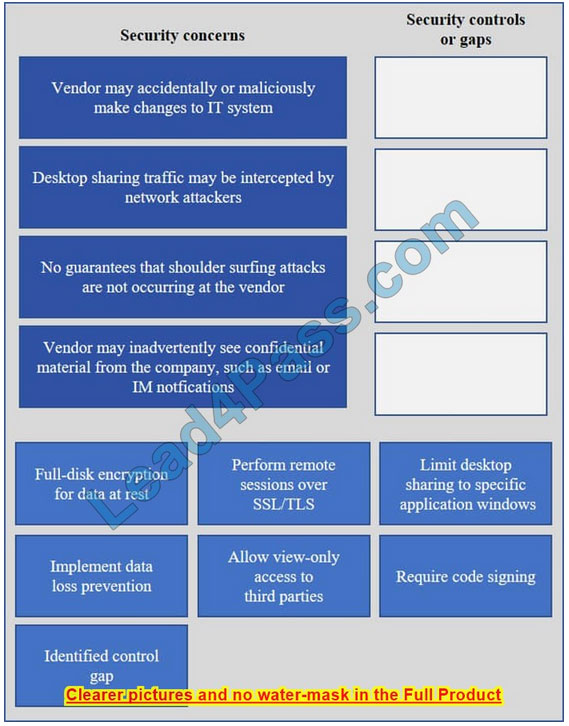
Correct Answer:
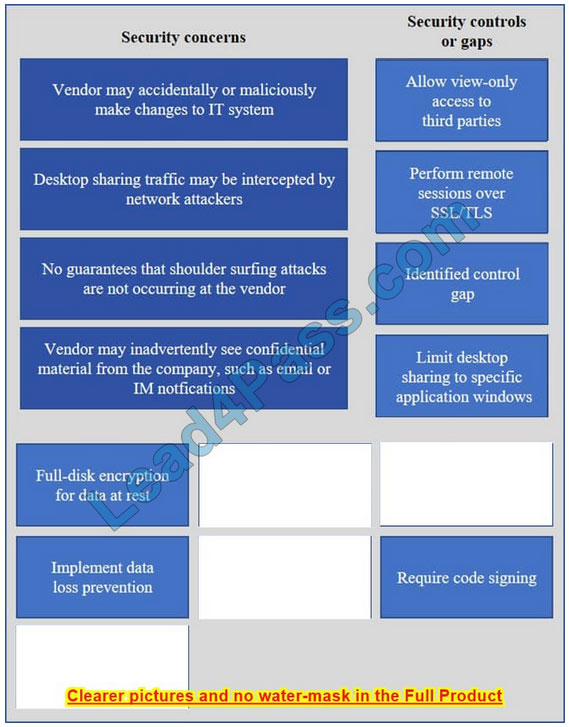
Vendor may accidentally or maliciously make changes to the IT system – Allow view-only access.
With view-only access, the third party can view the desktop but cannot interact with it. In other words, they cannot control the keyboard or mouse to make any changes.
Desktop sharing traffic may be intercepted by network attackers – Use SSL for remote sessions.
SSL (Secure Sockets Layer) encrypts data in transit between computers. If an attacker intercepted the traffic, the data would be encrypted and therefore unreadable to the attacker.
No guarantees that shoulder surfing attacks are not occurring at the vendor – Identified control gap.
Shoulder surfing is where someone else gains information by looking at your computer screen. This should be identified as a risk. A control gap occurs when there are either insufficient or no actions taken to avoid or mitigate a significant risk.
Vendor may inadvertently see confidential material from the company such as email and IMs – Limit desktop session to certain windows.
The easiest way to prevent a third party from viewing your emails and IMs is to close the email and IM application windows for the duration of the desktop sharing session.
New Question 3:
A security consultant is considering authentication options for a financial institution. The following authentication options are available security mechanism to the appropriate use case. Options may be used once.
Select and Place:
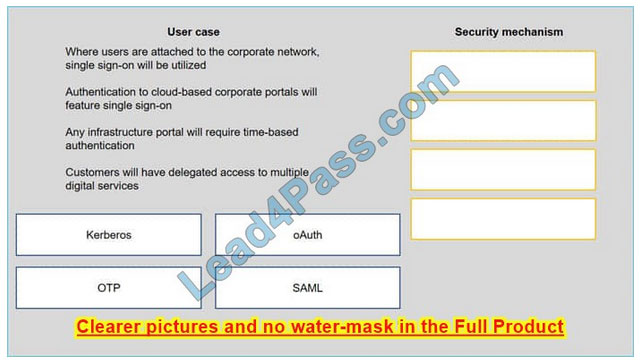
Correct Answer:
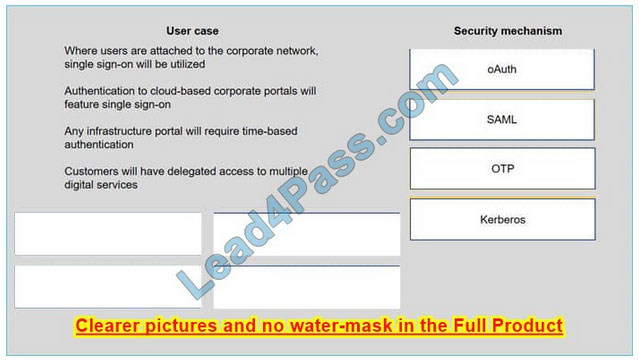
New Question 4:
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.
Select and Place:
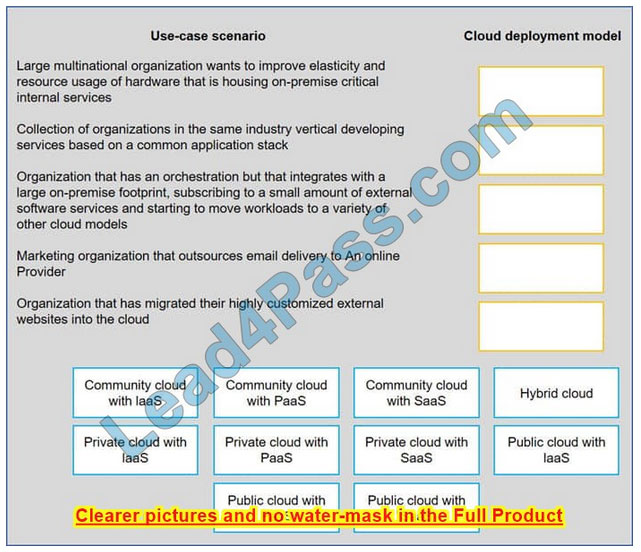
Correct Answer:
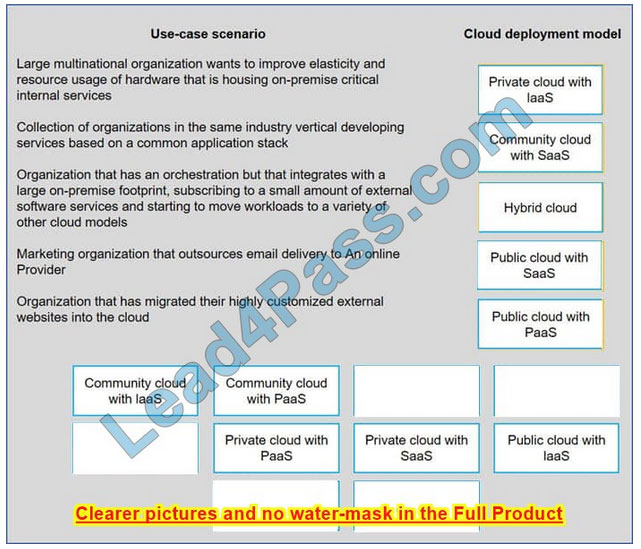
New Question 5:
A security administrator must configure the database server shown below the comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.

Select and Place:

Correct Answer:

New Question 6:
DRAG DROP
A vulnerability scan with the latest definitions was performed across Sites A and B.
INSTRUCTIONS
Match each relevant finding to the affected host.
After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:
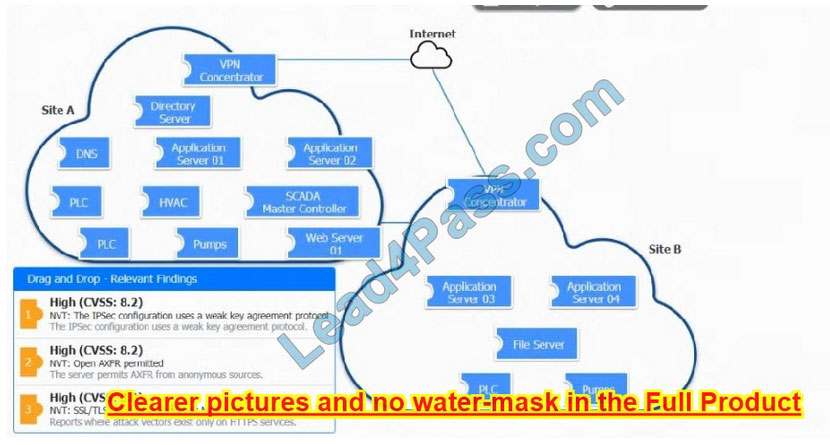
Correct Answer:
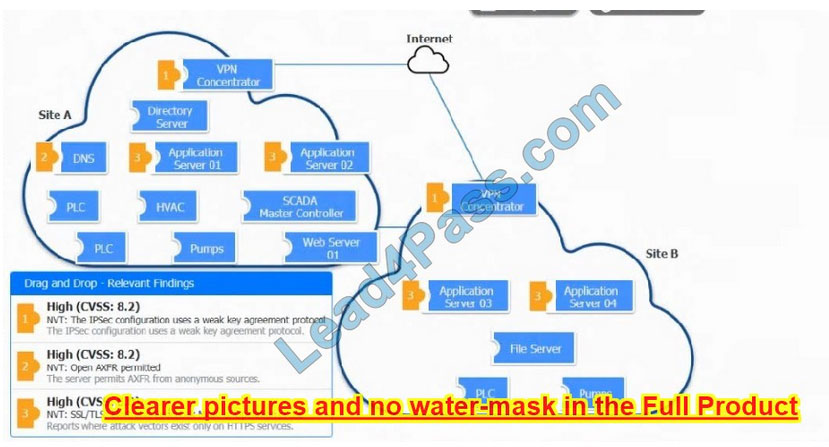
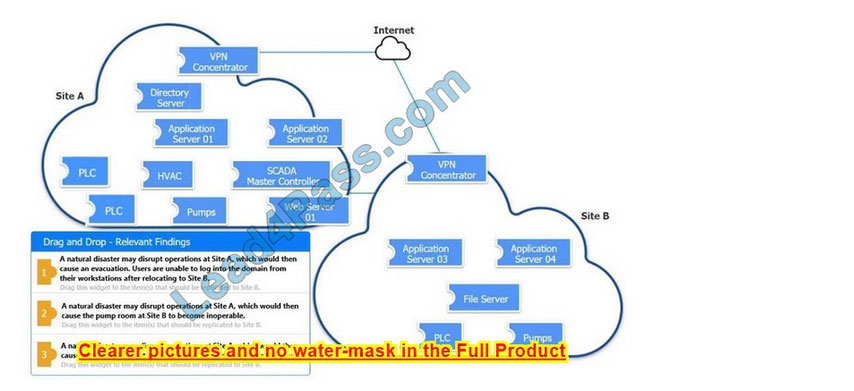
New Question 7:
DRAG DROP
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:
Correct Answer:
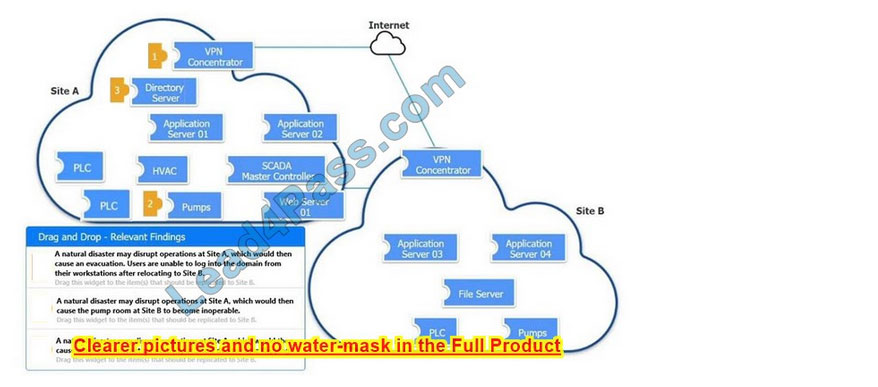
New Question 8:
SIMULATION
Compliance with company policy requires a quarterly review of firewall rules. A new administrator is asked to conduct this review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more
restrictive. Given the following information answer the questions below:
User Subnet: 192.168.1.0/24 Server Subnet: 192.168.2.0/24 Finance Subnet:192.168.3.0/24
Instructions: To perform the necessary tasks, please modify the DST port, Protocol, Action, and/or Rule Order columns. Firewall ACLs are read from the top down
Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.
Check the solution below.
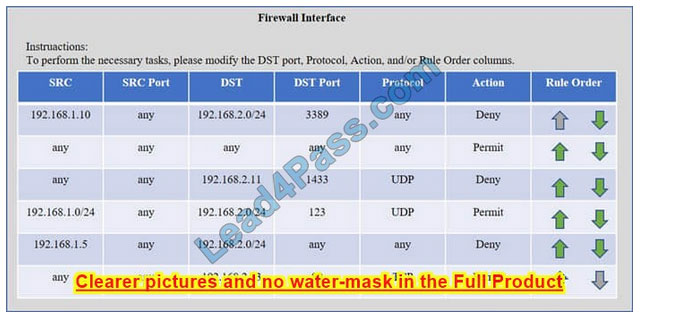
Check the answer below
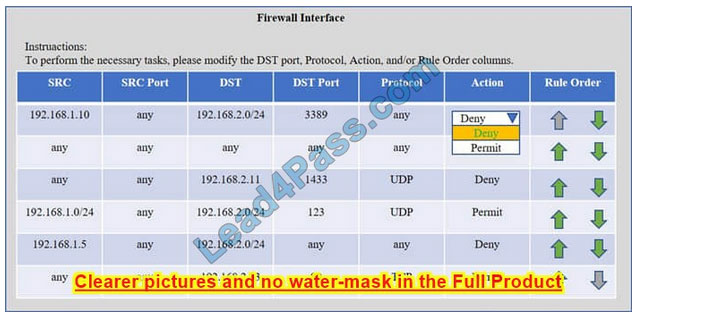
Correct Answer: Check the answer in explanation.
Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
The rule shown in the image below is the rule in question. It is not working because the action is set to Deny.
This needs to be set to Permit.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
The web servers rule is shown in the image below. Port 80 (HTTP) needs to be changed to port 443 for HTTPS (HTTP over SSL).
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
The SQL Server rule is shown in the image below. It is not working because the protocol is wrong. It should be TCP, not UDP.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.
The network time rule is shown in the image below.
However, this rule is not being used because the `any\’ rule shown below allows all traffic and the rule is placed above the network time rule. To block all other traffic, the `any\’ rule needs to be set to Deny, not Permit and the rule needs to be
placed below all the other rules (it needs to be placed at the bottom of the list to the rule is enumerated last).
New Question 9:
SIMULATION
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
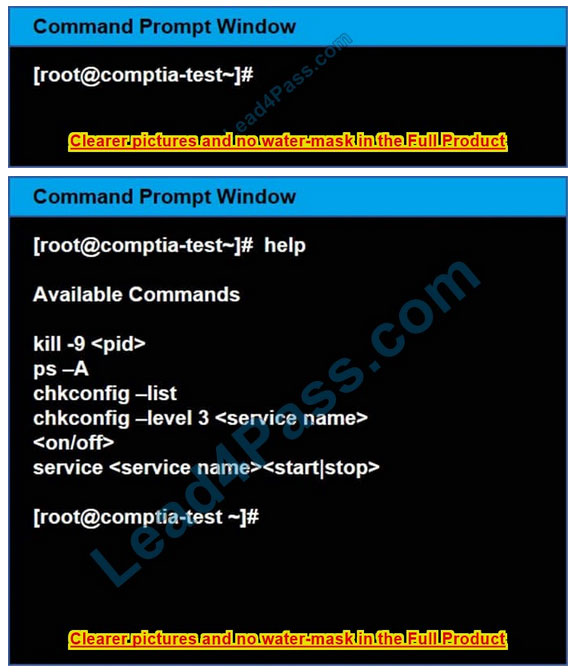
Correct Answer: Check the answer in explanation.
See the below In Order to deactivate web services, database services and print service, we can do following things 1) deactivate its services /etc/init.d/apache2 stop /etc/init.d/mysqld stop 2) close ports for these services Web Server
iptables -I INPUT -p tcp -m tcp –dport 443 -j REJECTservice iptables save Print Server iptables -I INPUT -p tcp -m tcp –dport 631 -j REJECTservice iptables save
Database Server iptables -I INPUT -p tcp -m tcp –dport <> -j REJECTservice iptables save 3) Kill the process any running for the same ps -aef|grep mysql kill -9 <>
New Question 10:
SIMULATION
Correct Answer: Check the answer in explanation.
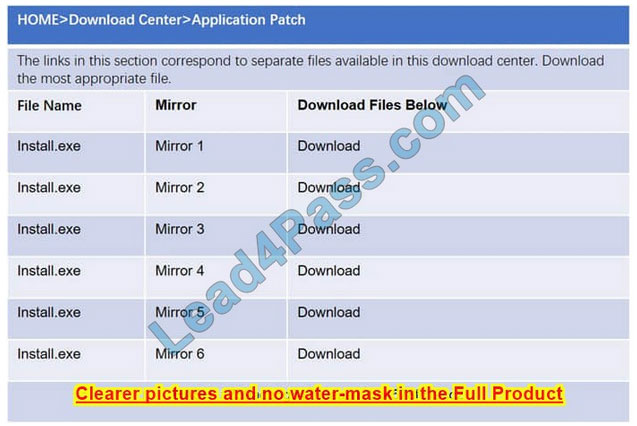
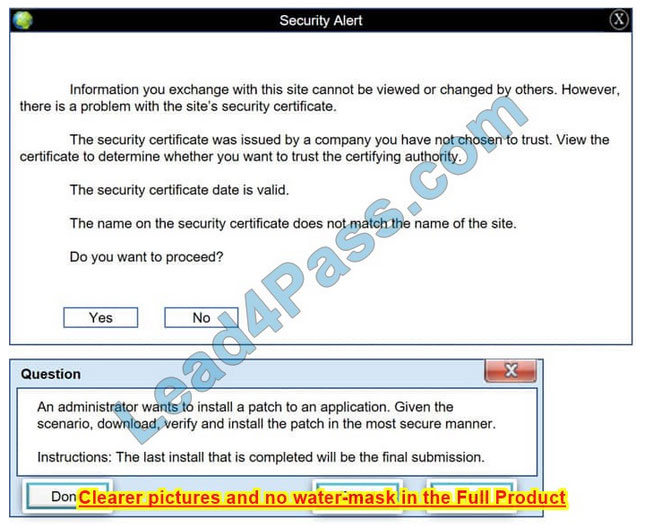
Please see the below
Step 1: Verify that the certificate is valid or not. In case of any warning message, cancel the download.
Step 2: If certificate issue is not there then, download the file in your system.
Step 3: Calculate the hash value of the downloaded file.
Step 4: Match the hash value of the downloaded file with the one which you selected on the website.
Step 5: Install the file if the hash value matches.
New Question 11:
SIMULATION
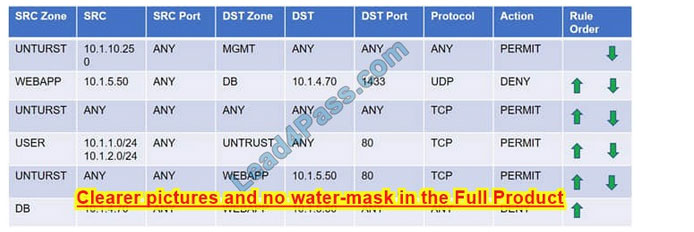
Compliance with company policy requires a quarterly review of firewall rules. You are asked to conduct a review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more secure. Given
the following information perform the tasks listed below:
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24 Web server: 10.1.5.50 MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250
Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation
requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Correct Answer: Check the answer in explanation.
Explanation:
Task 1: A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
In Rule no. 1 edit the Action to Deny to block internet access from the management platform.

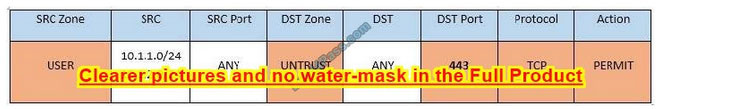
Task 2: The firewall must be configured so that the SQL server can only receive requests from the web server. In Rule no. 6 from top, edit the Action to be Permit.

Task 3: The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network. In rule no. 5 from top, change the DST port to Any from 80 to allow all unencrypted traffic.
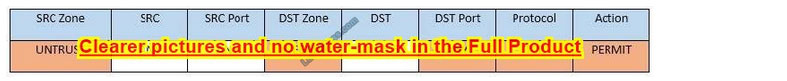
Task 4: Ensure the final rule is an explicit deny
Enter this at the bottom of the access list i.e. the line at the bottom of the rule:

Task 5: Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only. In Rule number 4 from top, edit the DST port to 443 from 80
New Question 12:
SIMULATION
An administrator wants to install a patch to an application.
INSTRUCTIONS
Given the scenario, download, verify, and install the patch in the most secure manner.
The last install that is completed will be the final submission.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
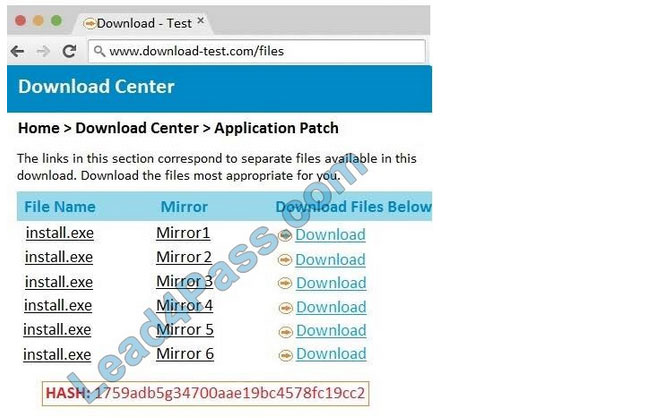
Correct Answer: See the below.
In this case the second link should be used (This may vary in actual exam). The first link showed the following error so it should not be used.
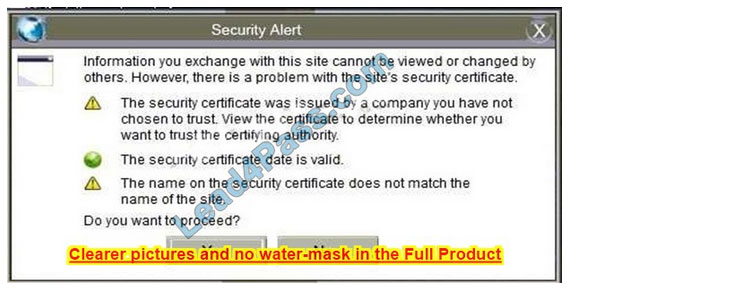
Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown:
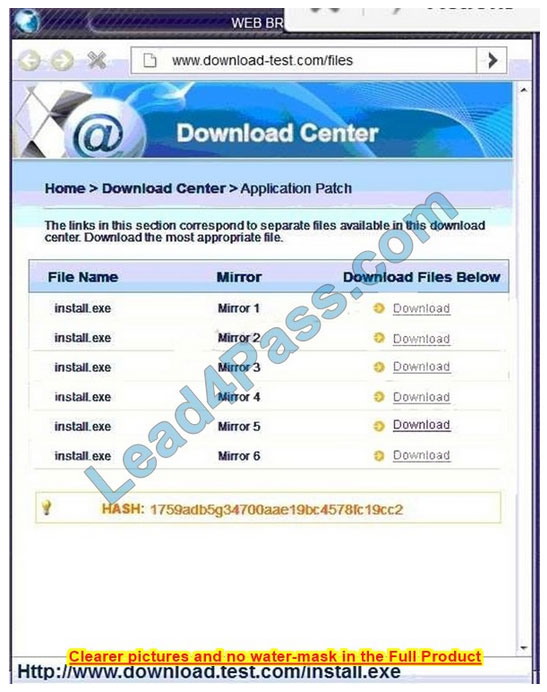
Since we need to do this in the most secure manner possible, they should not be used.
Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as shown. Make sure that the hash matches.
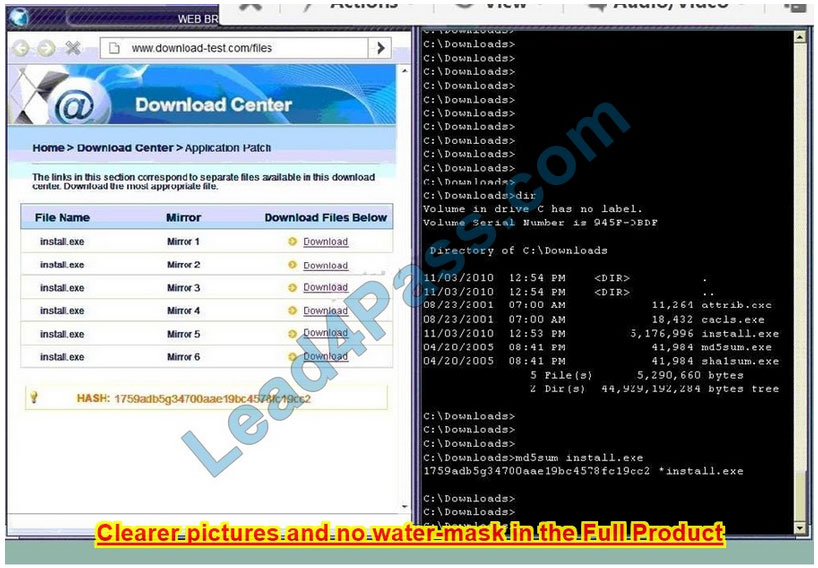
Finally, type in install.exe to install it and make sure there are no signature verification errors.
New Question 13:
SIMULATION
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Correct Answer: See the below.
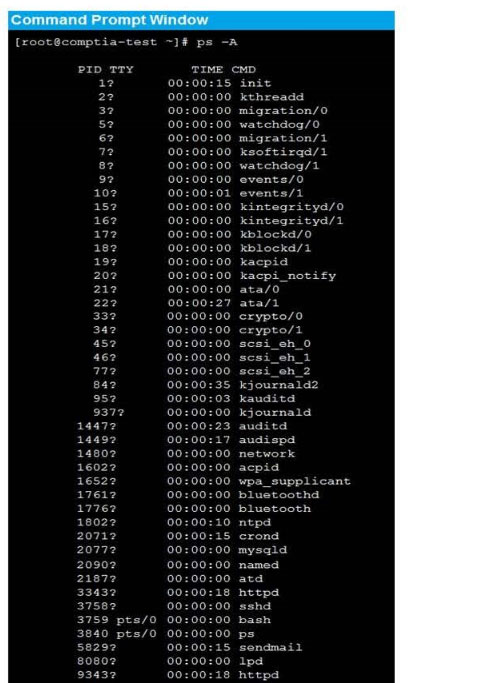
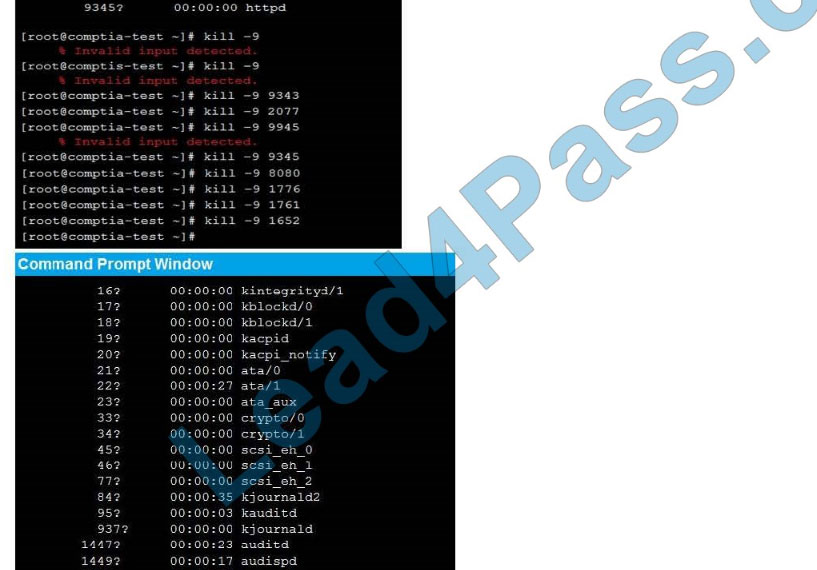
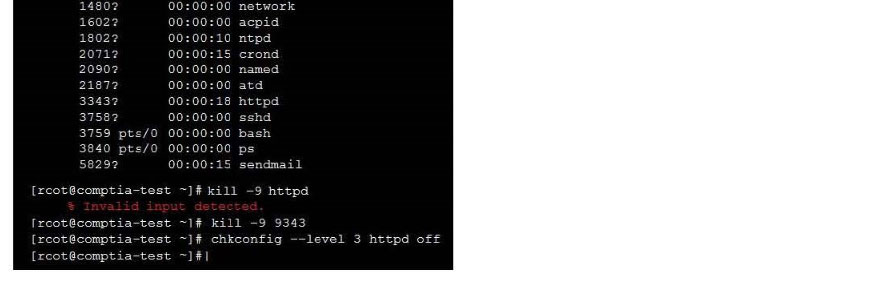

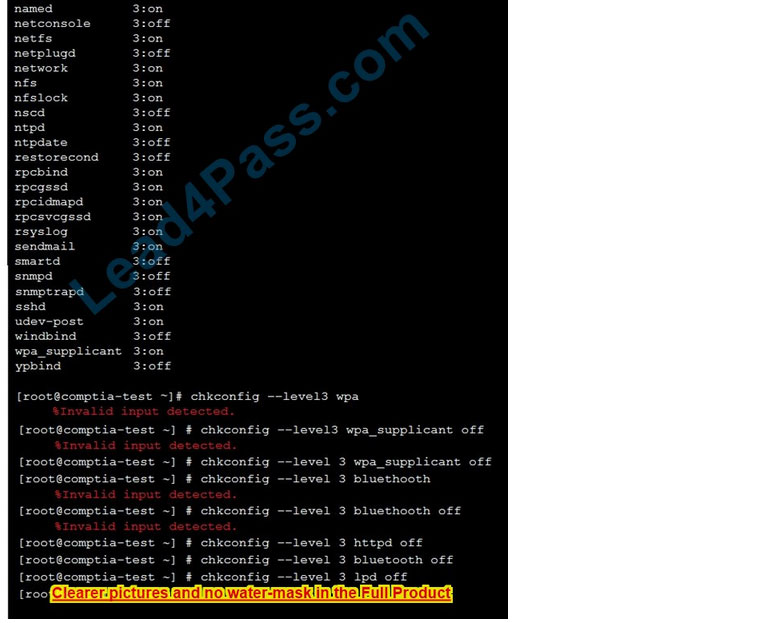
New Question 14:
SIMULATION
You are a security analyst tasked with interpreting an Nmap scan output from Company A\’s privileged network.
The company\’s hardening guidelines indicate the following:
1.
There should be one primary server or service per device.
2.
Only default ports should be used.
3.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed. For each device found, add a device entry to the Devices Discovered list, with the following information:
1.
The IP address of the device
2.
The primary server or service of the device
3.
The protocol(s) that should be disabled based on the hardening guidelines
To select multiple protocols, use CTRL+CLICK.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
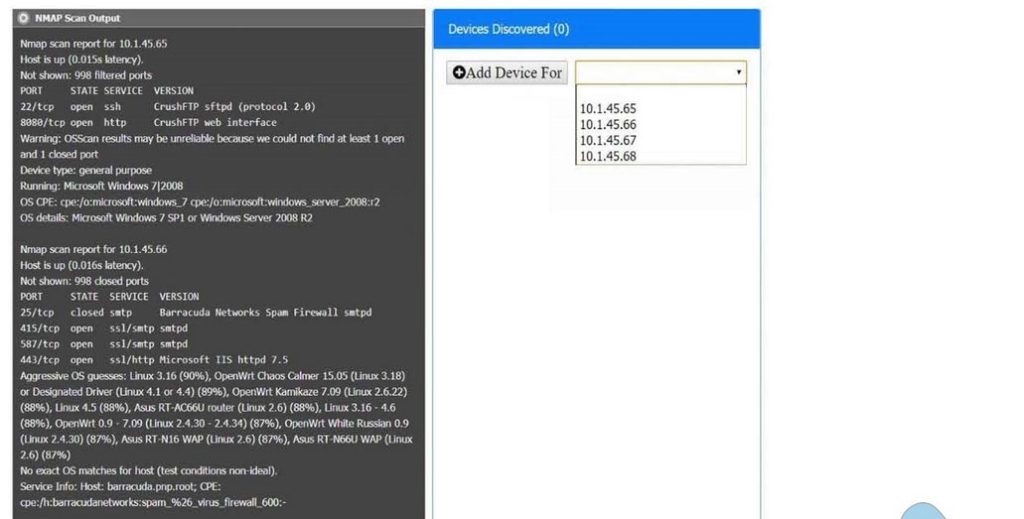
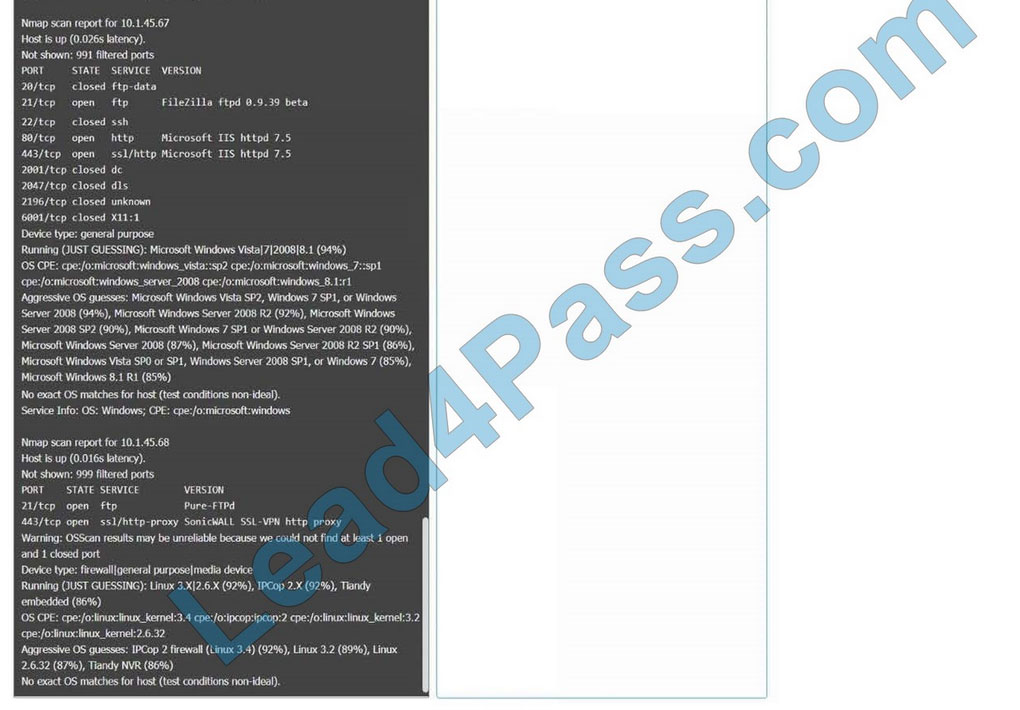
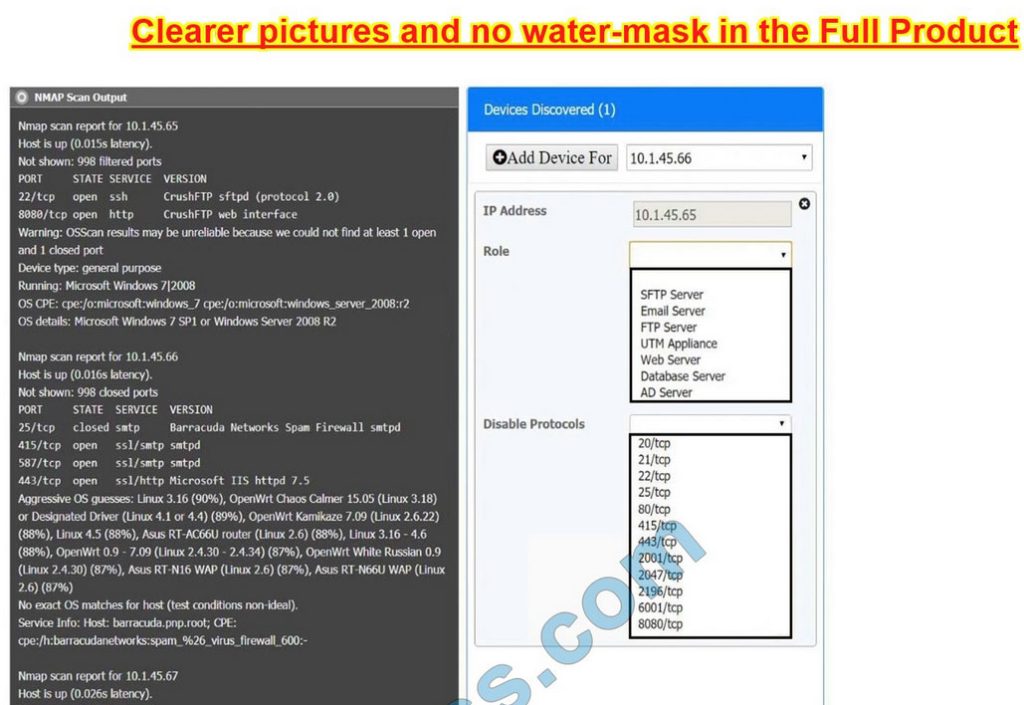
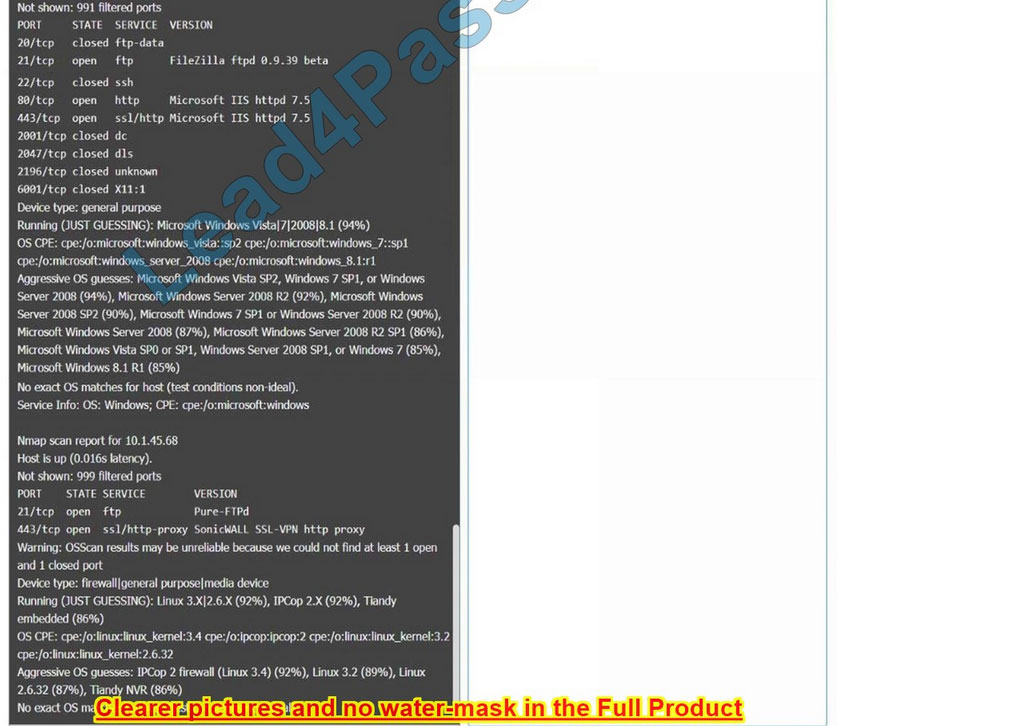
Correct Answer: Check the answer in explanation.
10.1.45.65 – FTP Server – Disable 8080
10.1.45.66 – Email Serve – Disable 25 and 415
10.1.45.67 – Web Server – Disable 21, 80
10.1.45.68 – UTM Appliance – Disable 21
New Question 15:
SIMULATION
A product development team has submitted code snippets for review pnor to release INSTRUCTIONS.
Analyze the code snippets and then select one vulnerability and one fix for each code snippet If at any time you would like to bang back the initial state of the simulation, please click the Reset All button.
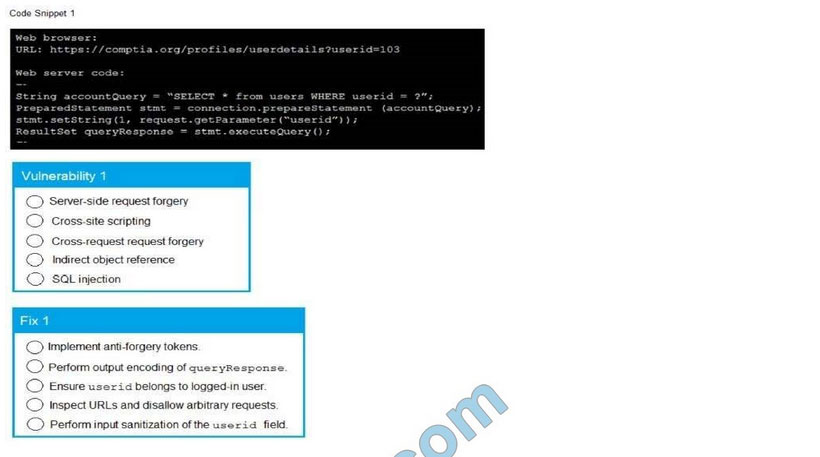
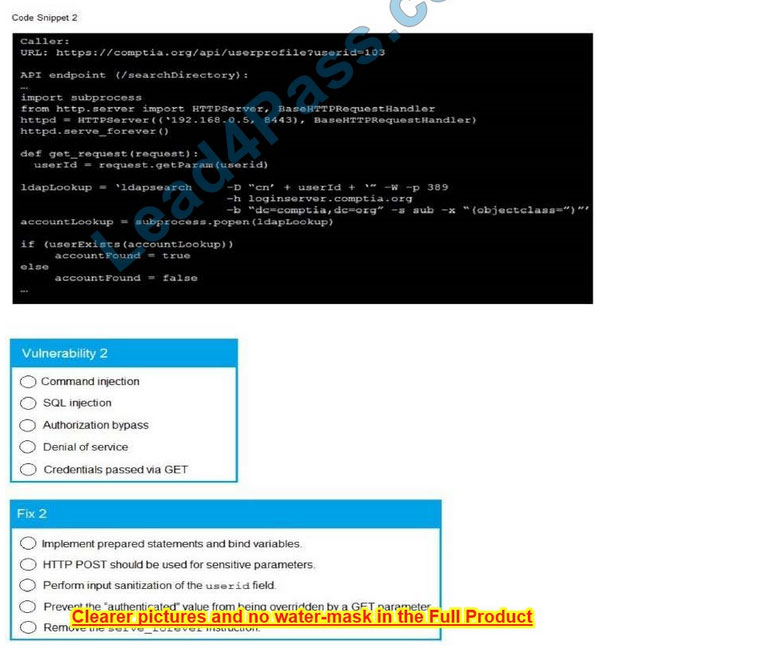
A. Check the answer in below.
Correct Answer: A
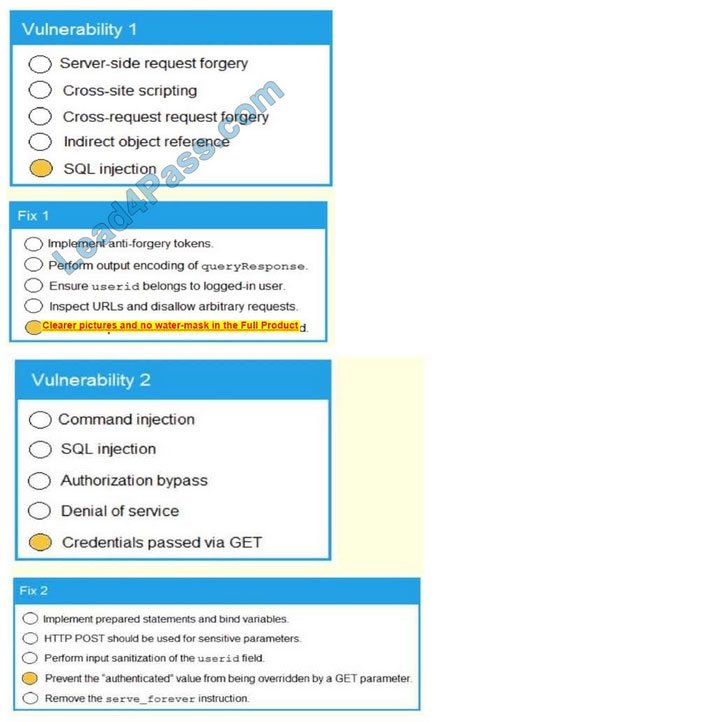
…
Download the CompTIA CAS-004 PDF for free sharing online:
https://drive.google.com/file/d/1gPzIc5NxyzqTe5jbFzvmofpUGr5d4CUr/
https://drive.google.com/file/d/1IbvnTbTz7x2VbxDQ1GHCSEII5xMN55Pn/
The above is only a part of CompTIA CAS-004 dumps exam questions and answers, you can use the above exam questions and answers to improve yourself, not only that, we welcome you to download the latest CompTIA CAS-004 dumps exam questions: https://www.leads4pass.com/cas-004.html (Total Questions: 267 Q&A), help you truly pass the CAS-004 CASP+ exam.
[New CompTIA Exam Dumps] CompTIA CASP CAS-002 Dumps Real Exam Questions And Youtube Free Shared
New CompTIA CASP CAS-002 dumps real exam questions and answers free download from lead4pass. High quality CompTIA CASP CAS-002 dumps pdf files and vce youtube demo update free shared. “CompTIA Advanced Security Practitioner Exam” is the name of CompTIA CASP https://www.leads4pass.com/cas-002.html exam dumps which covers all the knowledge points of the real CompTIA exam. Useful latest CompTIA CASP CAS-002 dumps pdf training materials and study guides free update, pass CompTIA CAS-002 exam test easily at first try.
Best CompTIA CAS-002 dumps pdf questions and answers: https://drive.google.com/open?id=0B_7qiYkH83VRVE55cV9qOGhpbG8
Best CompTIA CLO-001 dumps pdf questions and answers: https://drive.google.com/open?id=0B_7qiYkH83VRM1FyZGJiOUpoeVE
QUESTION 1
A company has issued a new mobile device policy permitting BYOD and company-issued devices. The company-issued device has a managed middleware client that restricts the applications allowed on company devices and provides those that are approved. The middleware client provides configuration standardization for both company owned and BYOD to secure data and communication to the device according to industry best practices. The policy states that, andquot;BYOD clients must meet the company\’s infrastructure requirements to permit a connection.andquot; The company also issues a memorandum separate from the policy, which provides instructions for the purchase, installation, and use of the middleware client on BYOD. Which of the following is being described?
A. Asset management
B. IT governance
C. Change management
D. Transference of risk
Correct Answer: B
QUESTION 2
An organization would like to allow employees to use their network username and password to access a third-party service. The company is using Active Directory Federated Services for their directory service. Which of the following should the company ensure is supported by the third-party? (Select TWO).
A. LDAP/S
B. SAML
C. NTLM
D. OAUTH
E. Kerberos
Correct Answer: BE
QUESTION 3
A sensitive database needs its cryptographic integrity upheld. Which of the following controls meets this goal? (Select TWO).
A. Data signing
B. Encryption
C. Perfect forward secrecy
D. Steganography
E. Data vaulting
F. RBAC
G. Lock and key
Correct Answer: AF
QUESTION 4
The risk manager is reviewing a report which identifies a requirement to keep a business critical legacy system operational for the next two years. The legacy system is out of support because the vendor and security patches are no longer released. Additionally, this is a proprietary embedded system and little is documented and known about it. Which of the following should the Information Technology department implement to reduce the security risk from a compromise of this system?
A. Virtualize the system and migrate it to a cloud provider.
B. Segment the device on its own secure network.
C. Install an antivirus and HIDS on the system.
D. Hire developers to reduce vulnerabilities in the code.
Correct Answer: B
QUESTION 5
A security code reviewer has been engaged to manually review a legacy application. A number of systemic issues have been uncovered relating to buffer overflows and format string vulnerabilities.
The reviewer has advised that future software projects utilize managed code platforms if at all possible.
Which of the following languages would suit this recommendation? (Select TWO).
A. C
B. C#
C. C++
D. Perl
E. Java
Correct Answer: BE
QUESTION 6
The lead systems architect on a software development project developed a design which is optimized for a distributed computing environment. The security architect assigned to the project has concerns about the integrity of the system, if it is deployed in a commercial cloud. Due to poor communication within the team, the security risks of the proposed design are not being given any attention. A network engineer on the project has a security background and is concerned about the overall success of the project. Which of the following is the BEST course of action for the network engineer to take?
A. Address the security concerns through the network design and security controls.
B. Implement mitigations to the security risks and address the poor communications on the team with the project manager.
C. Document mitigations to the security concerns and facilitate a meeting between the architects and the project manager.
D. Develop a proposal for an alternative architecture that does not leverage cloud computing and present it to the lead architect.
Correct Answer: C
QUESTION 7
A company has a single subnet in a small office. The administrator wants to limit non-web related traffic to the corporate intranet server as well as prevent abnormal HTTP requests and HTTP protocol anomalies from causing problems with the web server. Which of the following is the MOST likely solution?
A. Application firewall and NIPS
B. Edge firewall and HIDS
C. ACLs and anti-virus
D. Host firewall and WAF
Correct Answer: D
QUESTION 8
In order to reduce costs and improve employee satisfaction, a large corporation is creating a BYOD policy. It will allow access to email and remote connections to the corporate enterprise from personal devices; provided they are on an approved device list. Which of the following security measures would be MOST effective in securing the enterprise under the new policy? (Select TWO).
A. Provide free email software for personal devices.
B. Encrypt data in transit for remote access.
C. Require smart card authentication for all devices.
D. Implement NAC to limit insecure devices access.
E. Enable time of day restrictions for personal devices.
Correct Answer: BD
QUESTION 9
A large hospital has implemented BYOD to allow doctors and specialists the ability to access patient medical records on their tablets. The doctors and specialists access patient records over the hospital\’s guest WiFi network which is isolated from the internal network with appropriate security controls. The patient records management system can be accessed from the guest network and requires two factor authentication. Using a remote desktop type interface, the doctors and specialists can interact with the hospital\’s system. Cut and paste and printing functions are disabled to prevent the copying of data to BYOD devices. Which of the following are of MOST concern? (Select TWO).
A. Privacy could be compromised as patient records can be viewed in uncontrolled areas.
B. Device encryption has not been enabled and will result in a greater likelihood of data loss.
C. The guest WiFi may be exploited allowing non-authorized individuals access to confidential patient data.
D. Malware may be on BYOD devices which can extract data via key logging and screen scrapes.
E. Remote wiping of devices should be enabled to ensure any lost device is rendered inoperable.
Correct Answer: AD
QUESTION 10
When attending the latest security conference, an information security administrator noticed only a few people carrying a laptop around. Most other attendees only carried their smartphones.
Which of the following would impact the security of conference\’s resources?
A. Wireless network security may need to be increased to decrease access of mobile devices.
B. Physical security may need to be increased to deter or prevent theft of mobile devices.
C. Network security may need to be increased by reducing the number of available physical network jacks.
D. Wireless network security may need to be decreased to allow for increased access of mobile devices.
Correct Answer: C
QUESTION 11
Company A needs to export sensitive data from its financial system to company B\’s database, using company B\’s API in an automated manner. Company A\’s policy prohibits the use of any intermediary external systems to transfer or store its sensitive data, therefore the transfer must occur directly between company A\’s financial system and company B\’s destination server using the supplied API. Additionally, company A\’s legacy financial software does not support encryption, while company B\’s API supports encryption. Which of the following will provide end-to-end encryption for the data transfer while adhering to these requirements?
A. Company A must install an SSL tunneling software on the financial system.
B. Company A\’s security administrator should use an HTTPS capable browser to transfer the data.
C. Company A should use a dedicated MPLS circuit to transfer the sensitive data to company B.
D. Company A and B must create a site-to-site IPSec VPN on their respective firewalls.
Correct Answer: A
QUESTION 12
The security administrator has just installed an active\passive cluster of two firewalls for enterprise perimeter defense of the corporate network. Stateful firewall inspection is being used in the firewall implementation. There have been numerous reports of dropped connections with external clients.
Which of the following is MOST likely the cause of this problem?
A. TCP sessions are traversing one firewall and return traffic is being sent through the secondary firewall and sessions are being dropped.
B. TCP and UDP sessions are being balanced across both firewalls and connections are being dropped because the session IDs are not recognized by the secondary firewall.
C. Prioritize UDP traffic and associated stateful UDP session information is traversing the passive firewall causing the connections to be dropped.
D. The firewall administrator connected a dedicated communication cable between the firewalls in order to share a single state table across the cluster causing the sessions to be dropped.
Correct Answer: A
QUESTION 13
A security analyst has been asked to develop a quantitative risk analysis and risk assessment for the company\’s online shopping application. Based on heuristic information from the Security Operations Center (SOC), a Denial of Service Attack (DoS) has been successfully executed 5 times a year. The Business Operations department has determined the loss associated to each attack is $40,000. After implementing application caching, the number of DoS attacks was reduced to one time a year. The cost of the countermeasures was $100,000. Which of the following is the monetary value earned during the first year of operation?
A. $60,000
B. $100,000
C. $140,000
D. $200,000
Correct Answer: A
QUESTION 14
A bank now has a major initiative to virtualize as many servers as possible, due to power and rack space capacity at both data centers. The bank has prioritized by virtualizing older servers first as the hardware is nearing end-of-life.
The two initial migrations include:
Windows 2000 hosts: domain controllers and front-facing web servers RHEL3 hosts: front-facing web servers
Which of the following should the security consultant recommend based on best practices?
A. One data center should host virtualized web servers and the second data center should host the virtualized domain controllers.
B. One virtual environment should be present at each data center, each housing a combination of the converted Windows 2000 and RHEL3 virtual machines.
C. Each data center should contain one virtual environment for the web servers and another virtual environment for the domain controllers.
D. Each data center should contain one virtual environment housing converted Windows 2000 virtual machines and converted RHEL3 virtual machines.
Correct Answer: C
QUESTION 15
A large bank deployed a DLP solution to detect and block customer and credit card data from leaving the organization via email. A disgruntled employee was able to successfully exfiltrate data through the corporate email gateway by embedding a word processing document containing sensitive data as an object in a CAD file. Which of the following BEST explains why it was not detected and blocked by the DLP solution? (Select TWO).
A. The product does not understand how to decode embedded objects.
B. The embedding of objects in other documents enables document encryption by default.
C. The process of embedding an object obfuscates the data.
D. The mail client used to send the email is not compatible with the DLP product.
E. The DLP product cannot scan multiple email attachments at the same time.
Correct Answer: AC
Best useful CompTIA CASP CAS-002 dumps exam practice materials in PDF format free download from lead4pass. The best and most updated CompTIA CASP https://www.leads4pass.com/cas-002.html dumps pdf training resources which are the best for clearing CAS-002 exam test, and to get certified by CompTIA CASP, download one of the many PDF readers that are available for free.
High quality CompTIA CASP CAS-002 dumps vce youtube: https://youtu.be/UHKlO1Y4xjY
[New CompTIA Exam Dumps] Useful CompTIA Network+ N10-006 Dumps Exam Training Materials And Youtube Update
New CompTIA Network+ N10-006 dumps exam training materials in PDF format free download from lead4pass. “CompTIA Network+ certification” is the name of CompTIA Network+ https://www.leads4pass.com/n10-006.html exam dumps which covers all the knowledge points of the real CompTIA exam. Latest CompTIA Network+ N10-006 dumps pdf resources and vce youtube demo update free shared.
High quality CompTIA Network+ N10-006 dumps exam questions and answers free download from lead4pass. The best useful CompTIA Network+ N10-006 dumps pdf practice files and study guides update free try, pass CompTIA N10-006 exam test quickly and easily at first attempt.
Latest CompTIA N10-006 dumps pdf training materials: https://drive.google.com/open?id=0B_7qiYkH83VRY2RQR25WLWc3RjA
Latest CompTIA N10-005 dumps pdf training materials: https://drive.google.com/open?id=0B_7qiYkH83VRMnVzQ3RYbFpjWUk

QUESTION 1
Which of the following 802.11g antennas broadcast an RF signal in a specific direction with a narrow path?
A. Omni-direction
B. Unidirectional
C. Patch
D. Yagi
Correct Answer: B
QUESTION 2
A network engineer needs to set up a topology that will not fail if there is an outage on a single piece of the topology.
However, the computers need to wait to talk on the network to avoid congestions. Which of the following topologies would the engineer implement?
A. Star
B. Bus
C. Ring
D. Mesh
Correct Answer: C
QUESTION 3
A network technician must allow use of HTTP from the internet to an internal resource running HTTP. This is an example of which of the following?
A. Dynamic DNS
B. Virtual Private networking (VPN)
C. Dynamic NAT
D. Port Forwarding
Correct Answer: D
QUESTION 4
Which of the following broadband WAN technologies would MOST likely be used to connect several remote branches that have no fiber or satellite connections? N10-006 dumps
A. OC12
B. POTS
C. WiMax
D. OC3
Correct Answer: B
QUESTION 5
Users connecting to an SSID appear to be unable to authenticate to the captive portal. Which of the following is the cause of this issue?
A. WPA2 security key
B. SSL certificates
C. CSMAjCA
D. RADIUS
Correct Answer: D
QUESTION 6
Which of the following is MOST likely to use an RJ-11 connector to connect a computer to an ISP using a POTS line?
A. Multilayer switch
B. Access point
C. Analog modem
D. DOCSIS modem
Correct Answer: C
QUESTION 7
A company is installing several APs for a new wireless system that requires users to authenticate to the domain. The network technician would like to authenticate to a central point. Which of the following would work BEST to achieve these results?
A. A TACACS+ device and a RADIUS server
B. A TACACS and a proxy server
C. A RADIUS server and an access point
D. A RADIUS server and a network controller
Correct Answer: C
QUESTION 8
Which of the following helps prevent routing loops?
A. Routing table
B. Default gateway
C. Routesummarization
D. Split horizon
Correct Answer: D
QUESTION 9
Which of the following would be used in an IP-based video conferencing deployment? N10-006 dumps (Select TWO).
A. RS-232
B. 56k modem
C. Bluetooth
D. Codec
E. SIP
Correct Answer: DE
QUESTION 10
A technician needs to set aside addresses in a DHCP pool so that certain servers always receive the same address.
Which of the following should be configured?
A. Leases
B. Helper addresses
C. Scopes
D. Reservations
Correct Answer: D
QUESTION 11
Which of the following ports is used to provide secure sessions over the web by default?
A. 22
B. 25
C. 80
D. 5004
Correct Answer: A
QUESTION 12
A company has implemented the capability to send all log files to a central location by utilizing an encrypted channel.
The log files are sent to this location in order to be reviewed. A recent exploit has caused the company\’s encryption to become unsecure. Which of the following would be required to resolve the exploit?
A. Utilize a FTP service
B. Install recommended updates
C. Send all log files through SMTP
D. Configure the firewall to block port 22
Correct Answer: B
QUESTION 13
A malicious student is blocking mobile devices from connecting to the internet when other students are in the classroom. N10-006 dumps
Which of the following is the malicious student implementing?
A. Removing the AP from the classroom
B. ACL
C. Jamming
D. Firewall
E. IPS
Correct Answer: C
QUESTION 14
While troubleshooting a network outage, a technician finds a 100-meter fiber cable with a small service loop and suspects it might be the cause of the outage. Which of the following is MOST likely the issue?
A. Maximum cable length exceeded
B. Dirty connectors
C. RF interference caused by impedance mismatch
D. Bend radius exceeded
Correct Answer: D
QUESTION 15
While implementing wireless access points into the network, one building is having connectivity issues due to light fixtures being replaced in the ceiling, while all other buildings\’ connectivity is performing as expected. Which of the following should be exchanged on the access points installed in the building with connectivity issues?
A. UTP patch cables
B. Antenna
C. Power adapter
D. Security standard
Correct Answer: B
The best and most updated useful CompTIA CompTIA Network+ https://www.leads4pass.com/n10-006.html dumps pdf training resources which are the best for clearing N10-006 exam test, and to get certified by CompTIA CompTIA Network+. 100% success and guarantee to pass.
High quality CompTIA Network+ N10-006 dumps vce youtube: https://youtu.be/wsV4zJ_KQgI