latest 350-701 practice test
now browsing by tag
[Updated May 2023] Practice the latest CCNP Security 350-701 exam questions online

Lead4Pass updates CCNP Security 350-701 dumps throughout the year, and more importantly, provides some free exam questions each time to help candidates practice their tests online!
May 350-701 dumps have been updated, and verified by the CCNP Security team, as true and effective! Now! Take the newest 350-701 online practice test! also available for download
350-701 dumps with PDF and VCE format: https://www.leads4pass.com/350-701.html (contains 598 latest exam questions and answers!).

CCNP Security 350-701 Exam Questions Online Practice Test:
| From | Number of exam questions | Exam name | Exam code |
| Lead4pass 350-701 dumps | 13 | Implementing and Operating Cisco Security Core Technologies (SCOR) | 350-701 |
QUESTION 1:
DRAG DROP
Drag and drop the descriptions from the left onto the correct protocol versions on the right.
Select and Place:
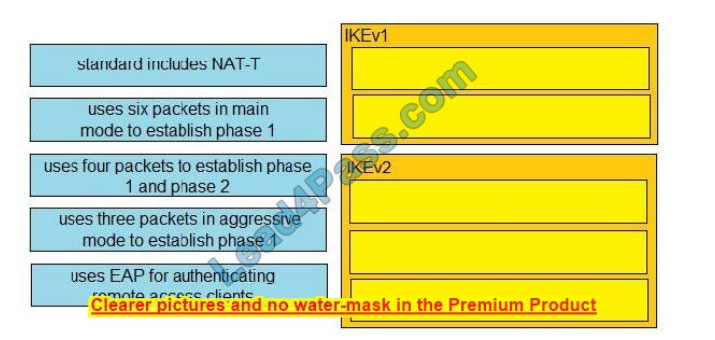
Correct Answer:
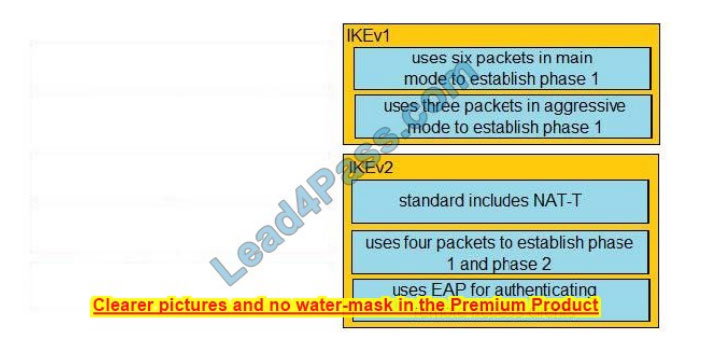
QUESTION 2:
Which two risks is a company vulnerable to if it does not have a well-established patching solution for endpoints? (Choose two)
A. exploits
B. ARP spoofing
C. denial-of-service attacks
D. malware
E. eavesdropping
Correct Answer: AD
Malware means “malicious software”, and is any software intentionally designed to cause damage to a computer, server, client, or computer network. The most popular types of malware include viruses, ransomware, and spyware.
Virus Possibly the most common type of malware, viruses attach their malicious code to clean code and wait to be run.
Ransomware is malicious software that infects your computer and displays messages demanding a fee to be paid in order for your system to work again. Spyware is spying software that can secretly record everything you enter, upload, download, and store on your computers or mobile devices. Spyware always tries to keep itself hidden.
An exploit is a code that takes advantage of a software vulnerability or security flaw. Exploits and malware are two risks for endpoints that are not up to date. ARP spoofing and eavesdropping are attacks against the network while denial-of-service attack is based on the flooding of IP packets.
QUESTION 3:
Which endpoint protection and detection feature performs correlation of telemetry, files, and intrusion events that are flagged as possible active breaches?
A. retrospective detection
B. indication of compromise
C. file trajectory
D. elastic search
Correct Answer: B
QUESTION 4:
An organization wants to improve its cybersecurity processes and add intelligence to its data The organization wants to utilize the most current intelligence data for URL filtering, reputations, and vulnerability information that can be integrated with the Cisco FTD and Cisco WSA What must be done to accomplish these objectives?
A. Create a Cisco pxGrid connection to NIST to import this information into the security products for policy use
B. Create an automated download of the Internet Storm Center intelligence feed into the Cisco FTD and Cisco WSA databases to tie to the dynamic access control policies.
C. Download the threat intelligence feed from the IETF and import it into the Cisco FTD and Cisco WSA databases
D. Configure the integrations with Talos Intelligence to take advantage of the threat intelligence that it provides.
Correct Answer: D
QUESTION 5:
Which two are valid suppression types on a Cisco Next-Generation Intrusion Prevention System? (Choose two)
A. Port
B. Rule
C. Source
D. Application
E. Protocol
Correct Answer: BC
QUESTION 6:
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the ASA be added on the Cisco UC Manager platform?
A. Certificate Trust List
B. Endpoint Trust List
C. Enterprise Proxy Service
D. Secured Collaboration Proxy
Correct Answer: A
QUESTION 7:
Which threat involves software being used to gain unauthorized access to a computer system?
A. virus
B. NTP amplification
C. ping of death
D. HTTP flood
Correct Answer: A
QUESTION 8:
Which type of protection encrypts RSA keys when they are exported and imported?
A. file
B. passphrase
C. NGE
D. nonexportable
Correct Answer: B
QUESTION 9:
Drag and drop the exploits from the left onto the type of security vulnerability on the right.
Select and Place:

Correct Answer:

QUESTION 10:
An administrator wants to ensure that all endpoints are compliant before users are allowed access to the corporate network.
The endpoints must have the corporate antivirus application installed and be running the latest build of Windows 10.
What must the administrator implement to ensure that all devices are compliant before they are allowed on the network?
A. Cisco Identity Services Engine and AnyConnect Posture module
B. Cisco Stealthwatch and Cisco Identity Services Engine integration
C. Cisco ASA firewall with Dynamic Access Policies configured
D. Cisco Identity Services Engine with PxGrid services enabled
Correct Answer: A
QUESTION 11:
Which IPS engine detects ARP spoofing?
A. Atomic ARP Engine
B. Service Generic Engine
C. ARP Inspection Engine
D. AIC Engine
Correct Answer: A
QUESTION 12:
What is the term for having information about threats and threat actors that helps mitigate harmful events that would otherwise compromise networks or systems?
A. trusted automated exchange
B. Indicators of Compromise
C. The Exploit Database
D. threat intelligence
Correct Answer: D
QUESTION 13:
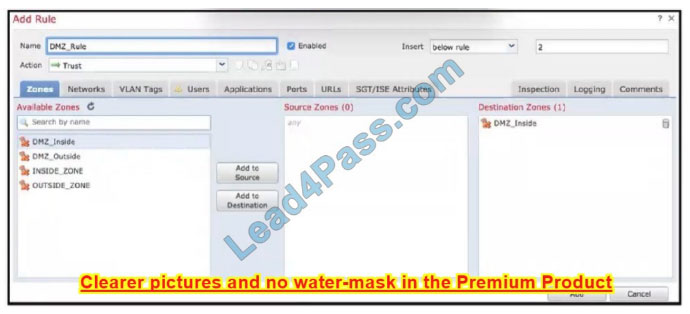
Refer to the exhibit When configuring this access control rule in Cisco FMC, what happens with the traffic destined to the DMZjnside zone once the configuration is deployed?
A. All traffic from any zone to the DMZ_inside zone will be permitted with no further inspection
B. No traffic will be allowed through to the DMZ_inside zone regardless of if it\’s trusted or not
C. All traffic from any zone will be allowed to the DMZ_inside zone only after inspection
D. No traffic will be allowed through to the DMZ_inside zone unless it\’s already trusted
Correct Answer: A
…

PS. Download the latest CCNP Security 350-701 exam practice questions online: https://drive.google.com/file/d/1CK6JCeH42AuFAKJ2TV5g8LRor8ATDFi8/
Every free sharing of CCNP Security 350-701 exam questions is the hard work of our CCNP Security team, and we hope to help you improve your strength!
Now, use 350-701 PDF dumps or 350-701 VCE dumps: https://www.leads4pass.com/350-701.html (both formats contain the latest exam questions and answers!)Also, get 15% off with code “Cisco”!