1v0-81.20 dumps
now browsing by tag
VMware 1V0-81.20 Dumps Update [2022] Associate VMware Security Best Exam Materials

VMware 1V0-81.20 Dumps have been updated as 2022 Associate VMware Security Best Exam Materials to help you pass the target exam with ease.
1V0-81.20 is the Associate VMware Security exam code, 1V0-81.20 Dumps are reviewed by the Lead4Pass VMware expert team, for candidates’ knowledge of VMware security solutions, And the candidate’s ability to provide entry-level support for the security features of NSX-T Data Center, Workspace ONE, and Carbon Black Cloud ensures that you can successfully pass the Associate VMware Security certification exam on your first try.
Download 1V0-81.20 Dumps: https://www.leads4pass.com/1v0-81-20.html, complete all practice questions carefully, and then take the Associate VMware Security certification exam:
Vendor: VMware
Exam Code: 1V0-81.20
Exam Name: Associate VMware Security
Certification: VCTA-SEC 2021 / VCTA-SEC 2022
Language: English
Duration: 120 Minutes
Number of Questions: 55
Passing score: 300 (VMware exams are scaled on a range from 100-500, with the determined raw cut score scaled to a value of 300.)
Format: Multiple Choice, Multiple Choice Multiple Selection, Drag and Drop, Matching, Proctored
Pricing: $125 USD
You can also try the 1V0-81.20 online test first:
Verify answers at the end of the test
QUESTION 1:
In VMware Carbon Black Cloud, which reputations have the highest priority during analysis?
A. Known Priority
B. Trusted Allow List
C. Company Allow List
D. Ignore
QUESTION 2:
Which VMware application enrolls an endpoint into Workspace ONE?
A. Workspace ONE Web
B. CB Defense Sensor
C. VMware Horizon Client
D. Workspace ONE Intelligent Hub
QUESTION 3:
When filtering firewall rules after selecting an object to filter by, which four columns do the filter search? (Choose four.)
A. Services
B. Action
C. Protocol
D. Log
E. Applied To
F. Source
G. Destinations
QUESTION 4:
When using VMware Carbon Black Live Response, what command will show all active processes?
A. dir
B. list
C. ls
D. ps
QUESTION 5:
Which parameter ensures an endpoint will stay connected with the designated VMware Carbon Black Cloud tenant?
A. Company Code
B. Organization Group ID
C. Device Serial Number
D. User ID
QUESTION 6:
Refer to the exhibit.
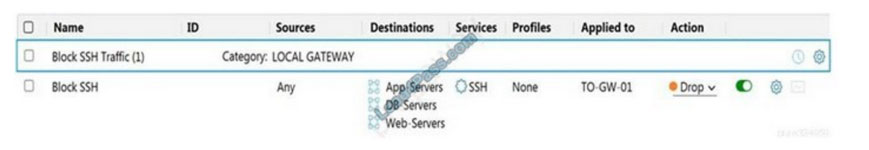
Which statement is true about the firewall rule?
A. It is a gateway firewall applied to a Tier-0 gateway that drops traffic on port 22
B. It is a distributed firewall applied to App-Services, DB-Servers, and Web-Servers that rejects traffic on port 22
C. It is a distributed firewall applied to App-Services, DB-Servers, and Web-Servers that drops traffic on port 22
D. It is a gateway firewall applied to a Tier-0 gateway that rejects traffic on port 22
QUESTION 7:
A technician has been asked to confirm a specific browser extension does not exist on any endpoint in their environment.
Which is the VMware Carbon Black tool to use for this task?
A. Enterprise EDR
B. EDR
C. Audit and Remediation
D. Endpoint Standard
QUESTION 8:
Which attack technique probes the environment for openings on devices or the firewall?
A. Port Scan
B. Denial of Service
C. Living off the Land
D. Phishing
QUESTION 9:
What is the safe course of action for a USB disk of unknown ownership and origin?
A. Do not connect the USB to any computer as it may be a USB Killer device
B. Connect the USB device to your computer and allow the DLP software to protect it
C. Connect the USB to a non-Windows device and examine it
D. Connect the USB to an air-gapped system and examine it
QUESTION 10:
In VMware Carbon Black Cloud Endpoint Standard, which items are available in the Event view?
A. Hashes, Reputations
B. Emails, Policies, OS, Locations
C. Connection, IP/Port
D. IDs, Indicators/TTPs
QUESTION 11:
Micro-segmentation is under which pillar of trust in VMware\’s 5 pillars of Zero Trust?
A. User
B. Session/Transport
C. Application
D. Device
QUESTION 12:
Which VMware product allows you to query an endpoint like a database?
A. VMware NSX-T Data Center
B. VMware Carbon Black Audit and Remediation
C. VMware Workspace ONE UEM
D. VMware Carbon Black Endpoint Standard
QUESTION 13:
What types of hosts are supported for hosting both NSX-T Data Center managers and host transport nodes?
A. vSphere ESXi 6.7U1 or higher, KVM on CentOS Linux
B. vSphere ESXi 6.7U1 or higher, KVM on RHEL 7.6, Ubuntu 18.04.2 LTS
C. vSphere ESXi 6.5, KVM on RHEL 7.6, Ubuntu 18.04.2 LTS
D. vSphere ESXi 6.7U1 or higher, CentOS KVM 7.6, RHEL KVM
……
Verify answer:
| Number: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| Answers: | B | D | A E F G | B | D | A | A | A | D | C | B | C | A |
Download the above 1V0-81.20 online test questions:https://drive.google.com/file/d/1uHz9-UXJMVB1FWcALS0q5dWLvdN0QCfQ/
Share some 1V0-81.20 online test questions for free to verify your current learning situation, click here to download 1V0-81.20 Dumps and complete the complete practice to help you easily pass the Associate VMware Security certification exam.