L A T E S T P O S T S
-
CompTIA CAS-004 CASP+ Exam Solutions | Latest CAS-004 Dumps
-
[Updated May 2023] Practice the latest CCNP Security 350-701 exam questions online
-
Practice for the 350-901 DEVCOR exam with newly updated 350-901 dumps
-
best plans for CCNA 200-301 certification exam in 2023
-
Lead4Pass CCDP 300-910 dumps are the best material for the 300-910 DEVOPS exam
-
Get Live update CCNP Enterprise 350-401 dumps with PDF and VCE
-
CCNP Collaboration exam dumps sharing from Lead4Pass
-
Latest updated CCNP Security 300-725 dumps from Lead4Pass
-
Latest Updated CCNP Security 300-710 Dumps Helps Candidates Pass 300-710 SNCF Exam
-
VMware 5v0-11.21 dumps: serves all 5v0-11.21 VMware Cloud on AWS Master Specialist exam candidates
CompTIA CAS-004 dumps: serves all CAS-004 CASP+ exam candidates
The newly updated CompTIA CAS-004 dumps contains 267 exam questions and answers that candidates can study using the CAS-004 dumps PDF and CAS-004 dumps VCE to help you successfully pass the CAS-004 CASP+ exam.
You are welcome to download the latest CompTIA CAS-004 dumps: https://www.leads4pass.com/cas-004.html, Lead4Pass CAS-004 dumps serve all candidates taking the CAS-004 CASP+ exam and guarantee you 100% Successfully passed the CAS-004 CASP+ exam.
Download the CompTIA CAS-004 PDF for free sharing online:
https://drive.google.com/file/d/1gPzIc5NxyzqTe5jbFzvmofpUGr5d4CUr/
https://drive.google.com/file/d/1IbvnTbTz7x2VbxDQ1GHCSEII5xMN55Pn/
Share the latest CompTIA CAS-004 dumps exam questions and answers for free
New Question 1:
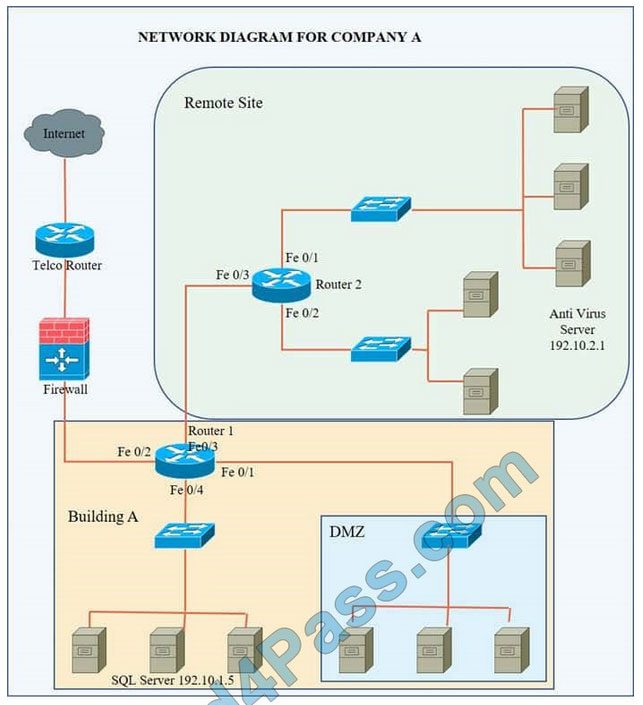
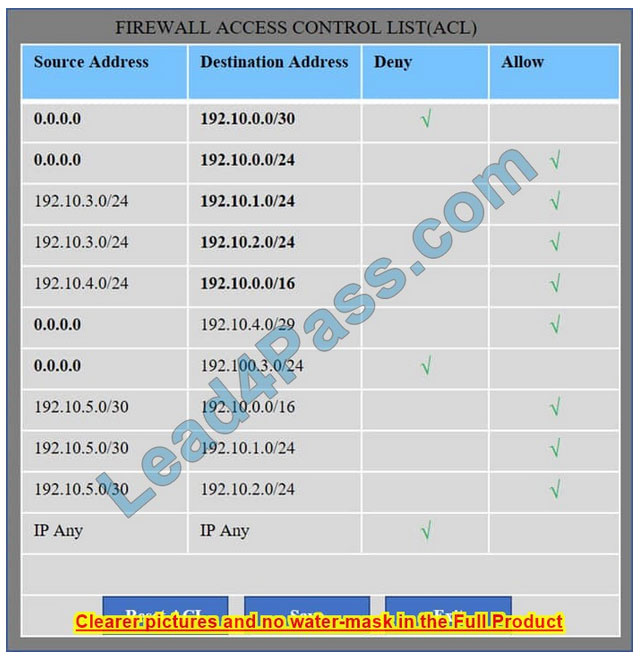
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address. The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and 192.10.2.0/24 for the remote
site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
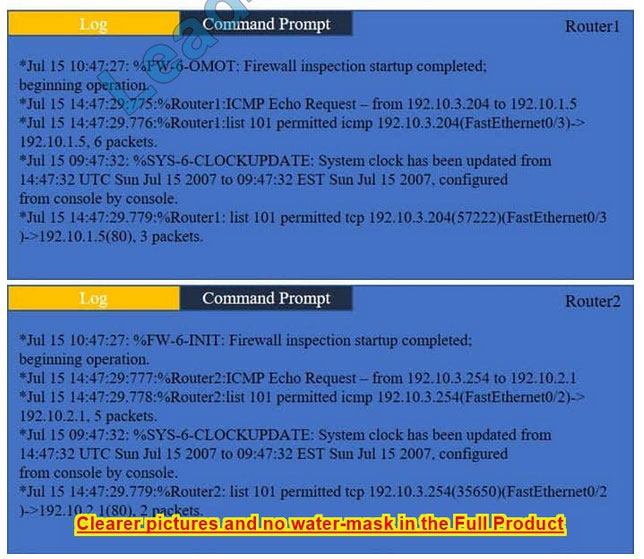
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
Hot Area:
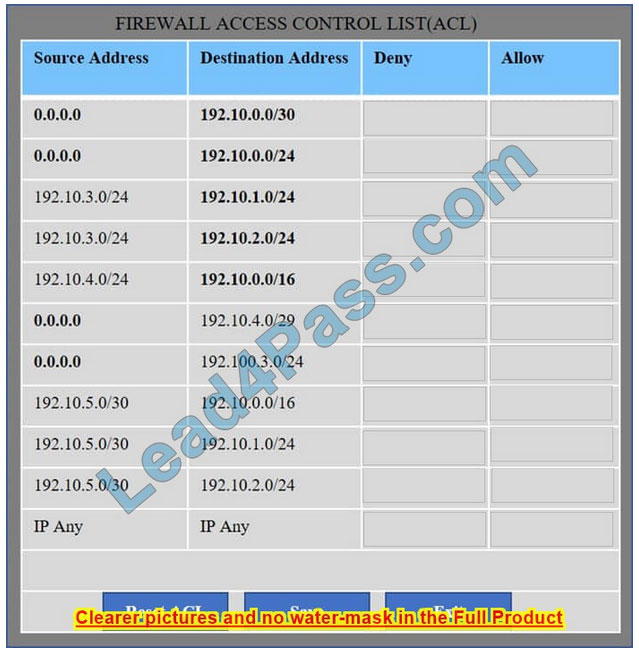
Correct Answer:
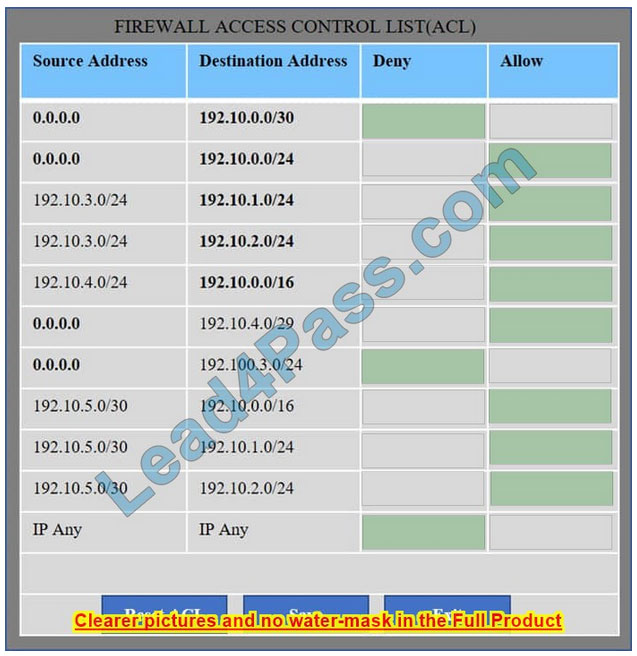
We have traffic coming from two rogue IP addresses: 192.10.3.204 and 192.10.3.254 (both in the 192.10.30.0/24 subnet) going to IPs in the corporate site subnet (192.10.1.0/24) and the remote site subnet (192.10.2.0/24). We need to Deny (block) this traffic at the firewall by ticking the following two checkboxes:
New Question 2:
IT staff within a company often conduct remote desktop sharing sessions with vendors to troubleshoot vendor product-related issues. Drag and drop the following security controls to match the associated security concern. Options may be used once or not at all.
Select and Place:
Correct Answer:
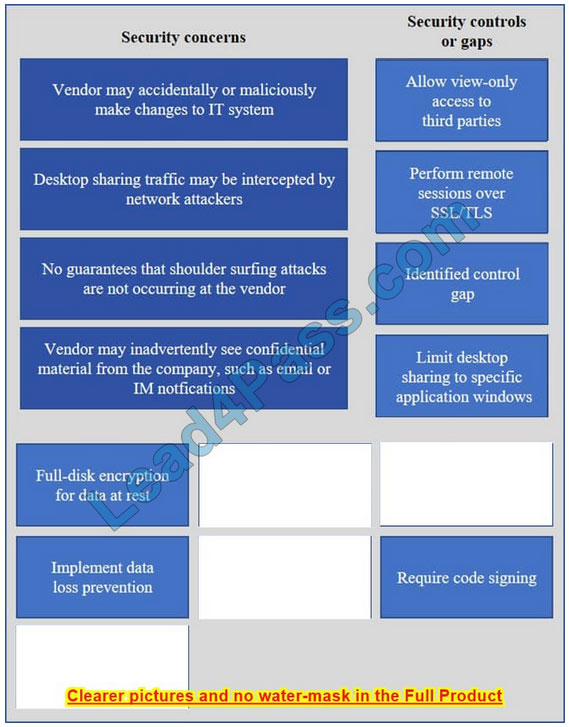
Vendor may accidentally or maliciously make changes to the IT system – Allow view-only access.
With view-only access, the third party can view the desktop but cannot interact with it. In other words, they cannot control the keyboard or mouse to make any changes.
Desktop sharing traffic may be intercepted by network attackers – Use SSL for remote sessions.
SSL (Secure Sockets Layer) encrypts data in transit between computers. If an attacker intercepted the traffic, the data would be encrypted and therefore unreadable to the attacker.
No guarantees that shoulder surfing attacks are not occurring at the vendor – Identified control gap.
Shoulder surfing is where someone else gains information by looking at your computer screen. This should be identified as a risk. A control gap occurs when there are either insufficient or no actions taken to avoid or mitigate a significant risk.
Vendor may inadvertently see confidential material from the company such as email and IMs – Limit desktop session to certain windows.
The easiest way to prevent a third party from viewing your emails and IMs is to close the email and IM application windows for the duration of the desktop sharing session.
New Question 3:
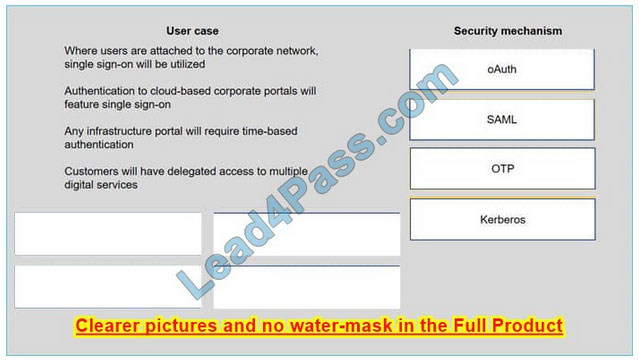
A security consultant is considering authentication options for a financial institution. The following authentication options are available security mechanism to the appropriate use case. Options may be used once.
Select and Place:
Correct Answer:
New Question 4:
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.
Select and Place:
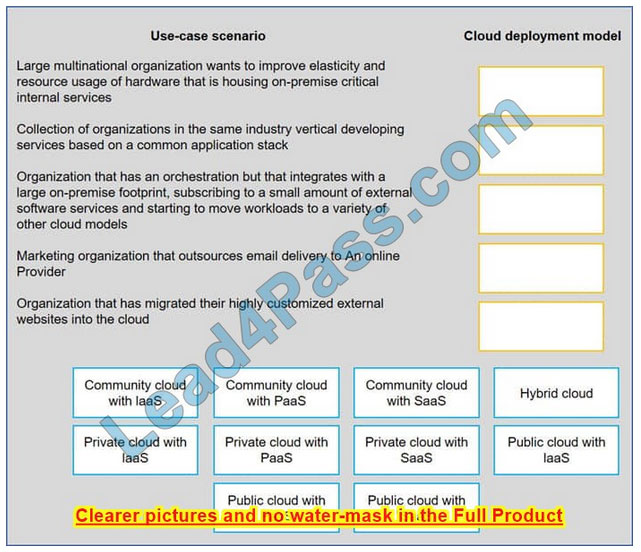
Correct Answer:
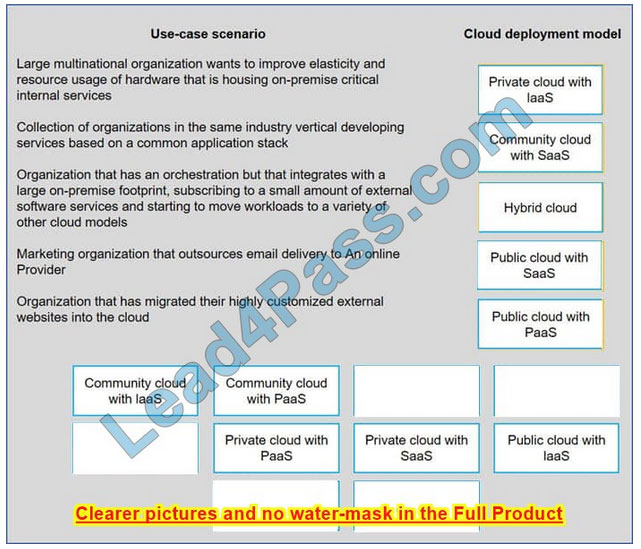
New Question 5:
A security administrator must configure the database server shown below the comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.

Select and Place:

Correct Answer:

New Question 6:
DRAG DROP
A vulnerability scan with the latest definitions was performed across Sites A and B.
INSTRUCTIONS
Match each relevant finding to the affected host.
After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:
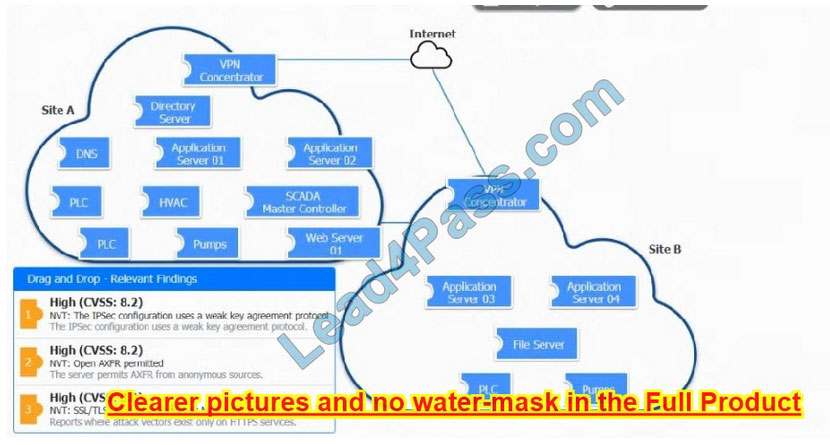
Correct Answer:
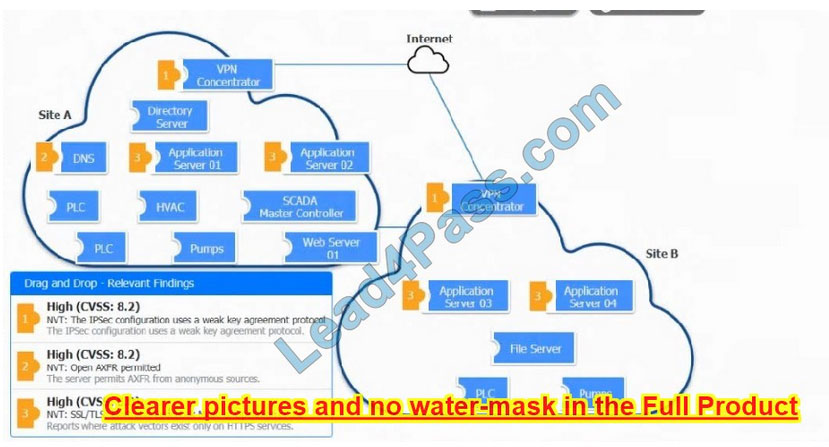
New Question 7:
DRAG DROP
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:
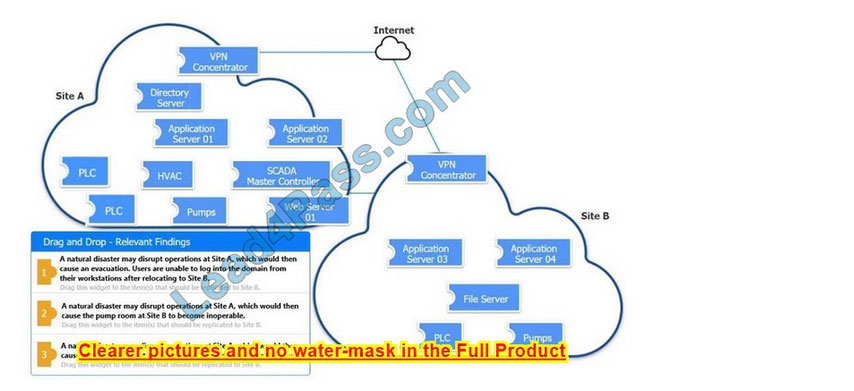
Correct Answer:
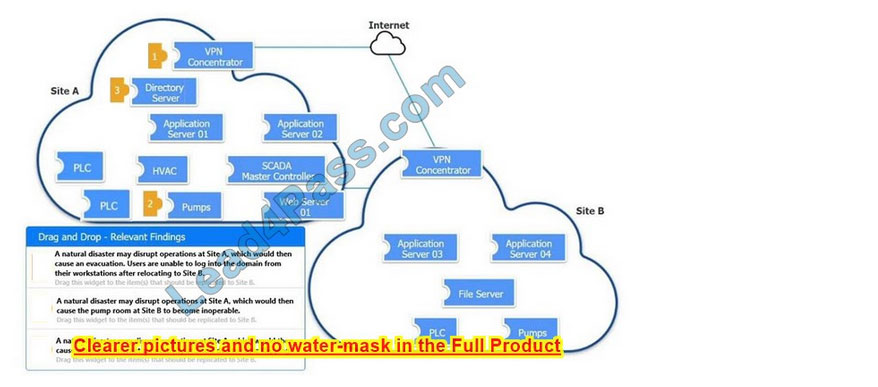
New Question 8:
SIMULATION
Compliance with company policy requires a quarterly review of firewall rules. A new administrator is asked to conduct this review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more
restrictive. Given the following information answer the questions below:
User Subnet: 192.168.1.0/24 Server Subnet: 192.168.2.0/24 Finance Subnet:192.168.3.0/24
Instructions: To perform the necessary tasks, please modify the DST port, Protocol, Action, and/or Rule Order columns. Firewall ACLs are read from the top down
Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.
Check the solution below.
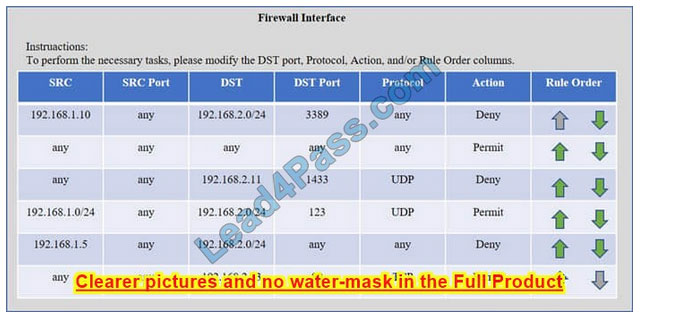
Check the answer below
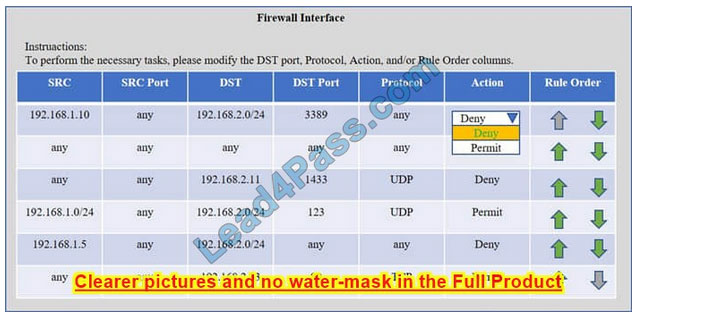
Correct Answer: Check the answer in explanation.
Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
The rule shown in the image below is the rule in question. It is not working because the action is set to Deny.
This needs to be set to Permit.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
The web servers rule is shown in the image below. Port 80 (HTTP) needs to be changed to port 443 for HTTPS (HTTP over SSL).
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
The SQL Server rule is shown in the image below. It is not working because the protocol is wrong. It should be TCP, not UDP.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.
The network time rule is shown in the image below.
However, this rule is not being used because the `any\’ rule shown below allows all traffic and the rule is placed above the network time rule. To block all other traffic, the `any\’ rule needs to be set to Deny, not Permit and the rule needs to be
placed below all the other rules (it needs to be placed at the bottom of the list to the rule is enumerated last).
New Question 9:
SIMULATION
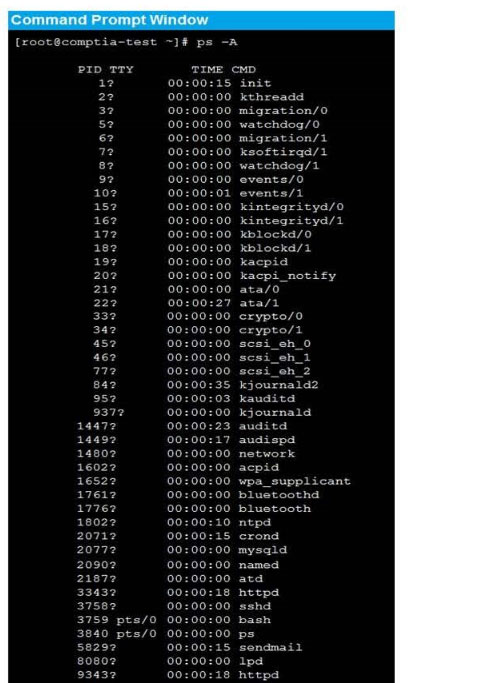
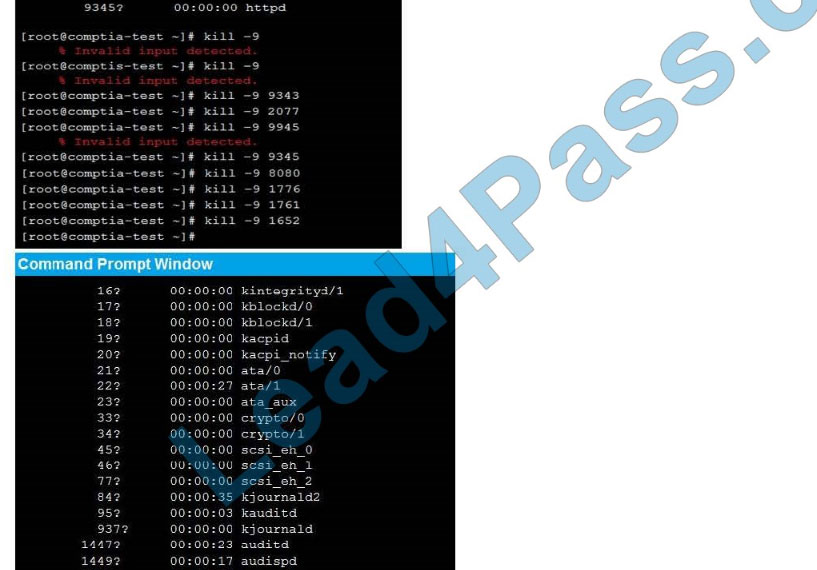
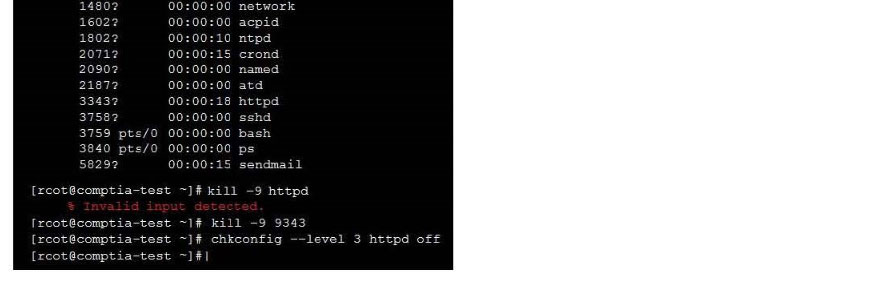
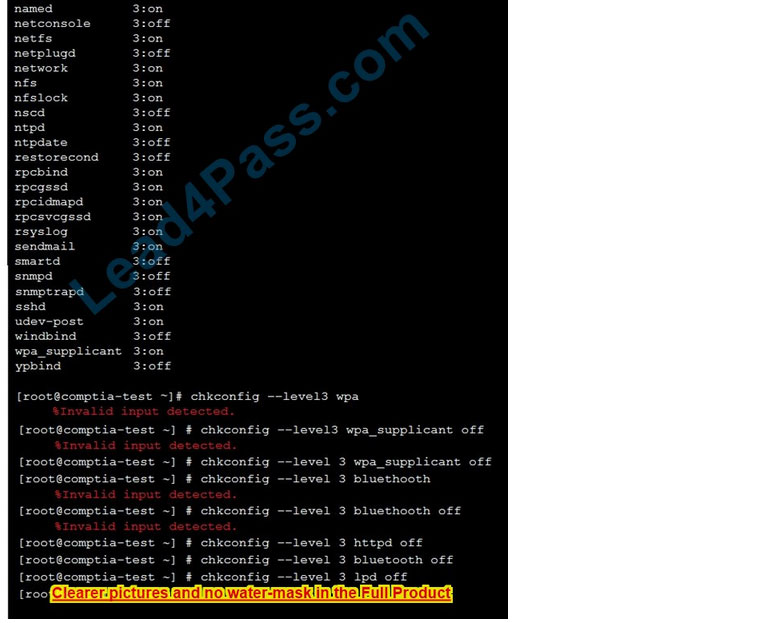
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
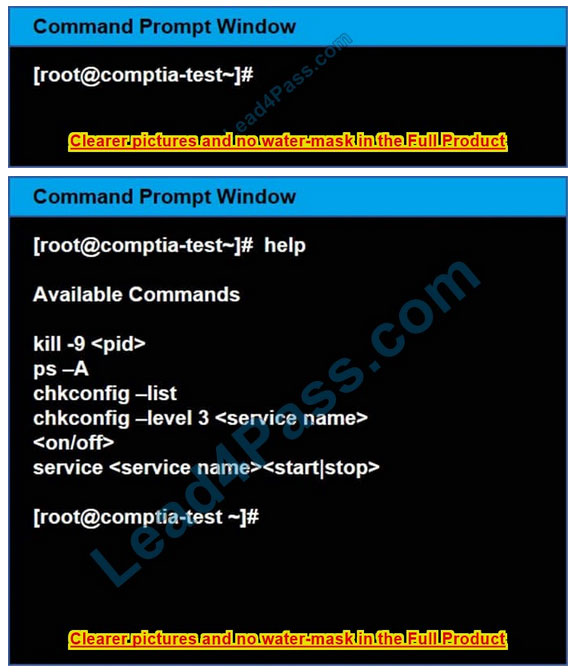
Correct Answer: Check the answer in explanation.
See the below In Order to deactivate web services, database services and print service, we can do following things 1) deactivate its services /etc/init.d/apache2 stop /etc/init.d/mysqld stop 2) close ports for these services Web Server
iptables -I INPUT -p tcp -m tcp –dport 443 -j REJECTservice iptables save Print Server iptables -I INPUT -p tcp -m tcp –dport 631 -j REJECTservice iptables save
Database Server iptables -I INPUT -p tcp -m tcp –dport <> -j REJECTservice iptables save 3) Kill the process any running for the same ps -aef|grep mysql kill -9 <>
New Question 10:
SIMULATION
Correct Answer: Check the answer in explanation.
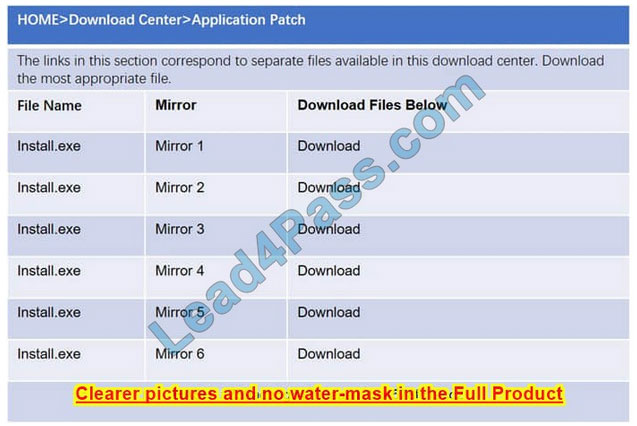
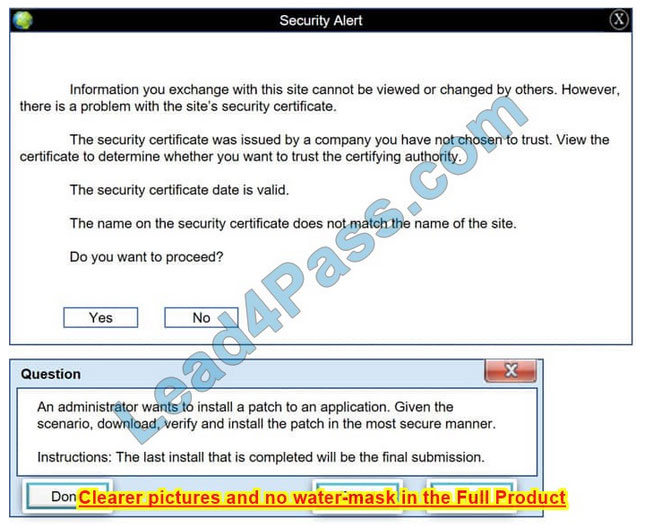
Please see the below
Step 1: Verify that the certificate is valid or not. In case of any warning message, cancel the download.
Step 2: If certificate issue is not there then, download the file in your system.
Step 3: Calculate the hash value of the downloaded file.
Step 4: Match the hash value of the downloaded file with the one which you selected on the website.
Step 5: Install the file if the hash value matches.
New Question 11:
SIMULATION
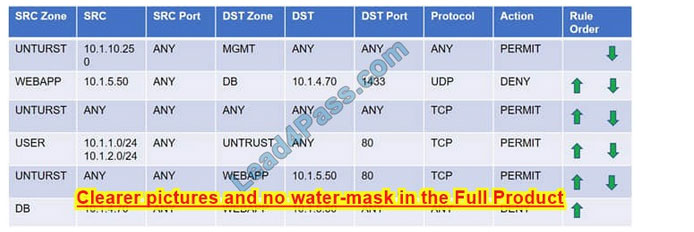
Compliance with company policy requires a quarterly review of firewall rules. You are asked to conduct a review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more secure. Given
the following information perform the tasks listed below:
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24 Web server: 10.1.5.50 MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250
Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation
requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Correct Answer: Check the answer in explanation.
Explanation:
Task 1: A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
In Rule no. 1 edit the Action to Deny to block internet access from the management platform.

Task 2: The firewall must be configured so that the SQL server can only receive requests from the web server. In Rule no. 6 from top, edit the Action to be Permit.

Task 3: The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network. In rule no. 5 from top, change the DST port to Any from 80 to allow all unencrypted traffic.
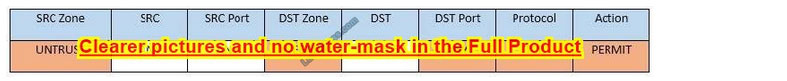
Task 4: Ensure the final rule is an explicit deny
Enter this at the bottom of the access list i.e. the line at the bottom of the rule:

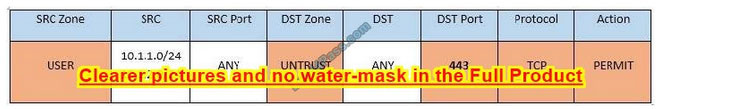
Task 5: Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only. In Rule number 4 from top, edit the DST port to 443 from 80
New Question 12:
SIMULATION
An administrator wants to install a patch to an application.
INSTRUCTIONS
Given the scenario, download, verify, and install the patch in the most secure manner.
The last install that is completed will be the final submission.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
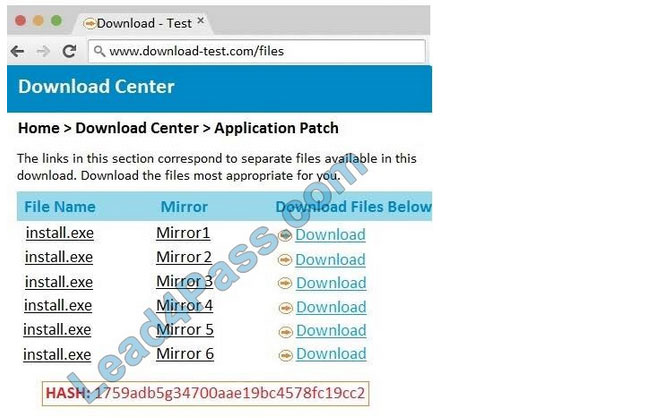
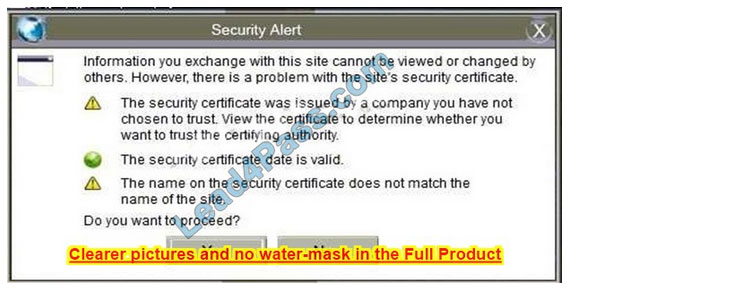
Correct Answer: See the below.
In this case the second link should be used (This may vary in actual exam). The first link showed the following error so it should not be used.
Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown:
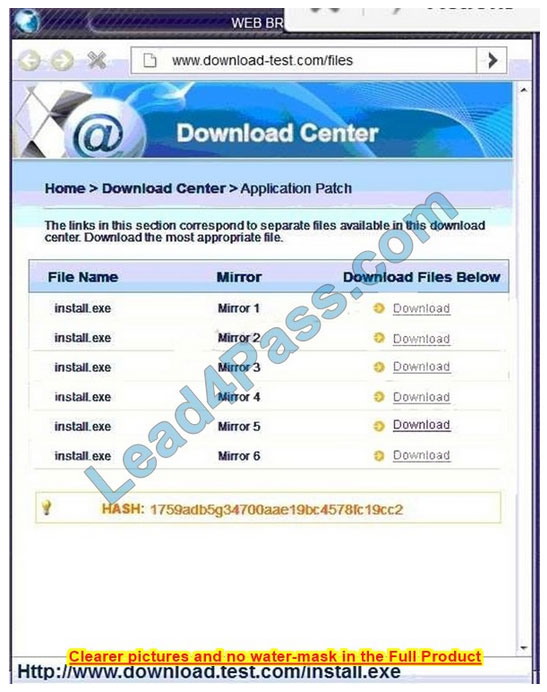
Since we need to do this in the most secure manner possible, they should not be used.
Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as shown. Make sure that the hash matches.
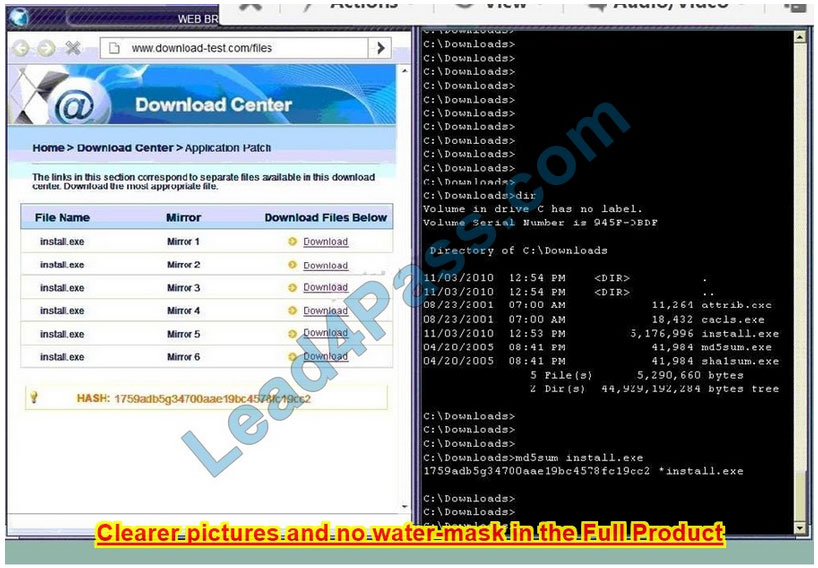
Finally, type in install.exe to install it and make sure there are no signature verification errors.
New Question 13:
SIMULATION
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Correct Answer: See the below.

New Question 14:
SIMULATION
You are a security analyst tasked with interpreting an Nmap scan output from Company A\’s privileged network.
The company\’s hardening guidelines indicate the following:
1.
There should be one primary server or service per device.
2.
Only default ports should be used.
3.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed. For each device found, add a device entry to the Devices Discovered list, with the following information:
1.
The IP address of the device
2.
The primary server or service of the device
3.
The protocol(s) that should be disabled based on the hardening guidelines
To select multiple protocols, use CTRL+CLICK.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
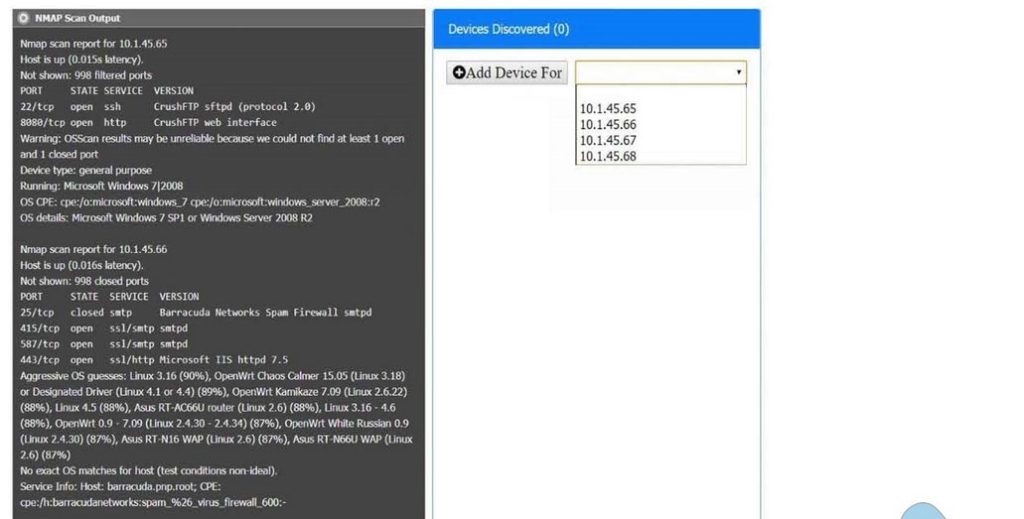
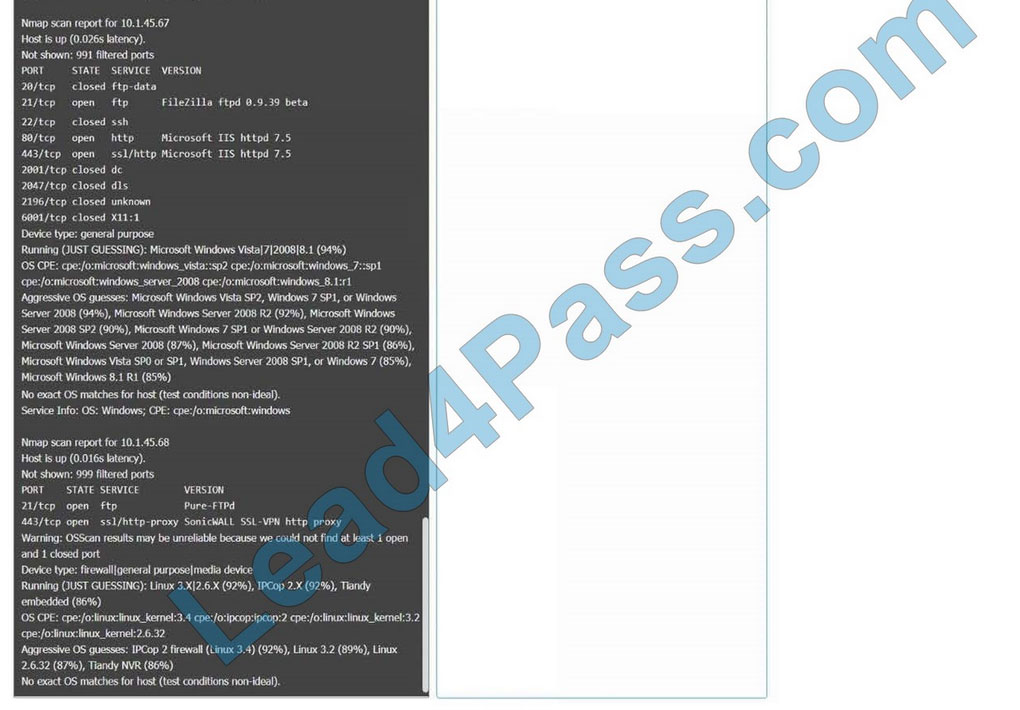
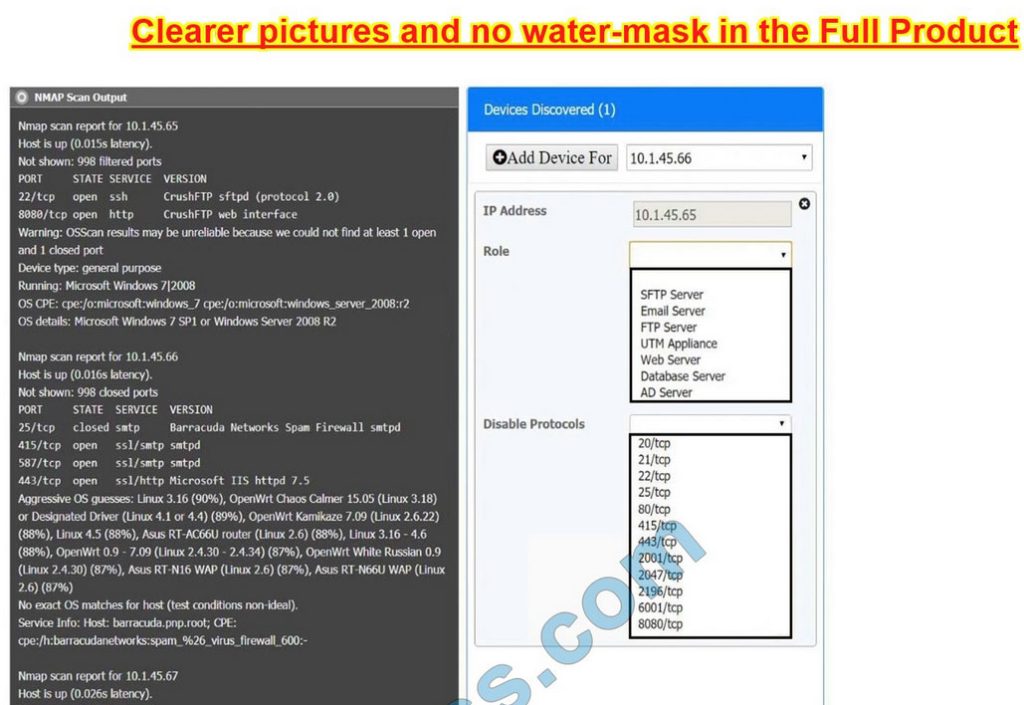
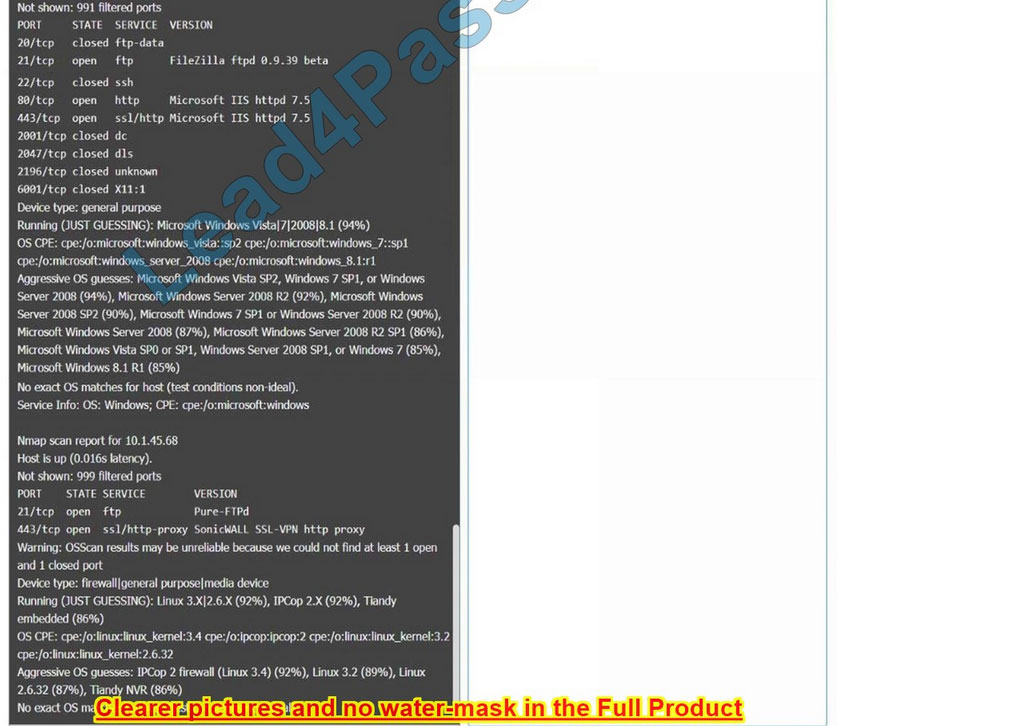
Correct Answer: Check the answer in explanation.
10.1.45.65 – FTP Server – Disable 8080
10.1.45.66 – Email Serve – Disable 25 and 415
10.1.45.67 – Web Server – Disable 21, 80
10.1.45.68 – UTM Appliance – Disable 21
New Question 15:
SIMULATION
A product development team has submitted code snippets for review pnor to release INSTRUCTIONS.
Analyze the code snippets and then select one vulnerability and one fix for each code snippet If at any time you would like to bang back the initial state of the simulation, please click the Reset All button.
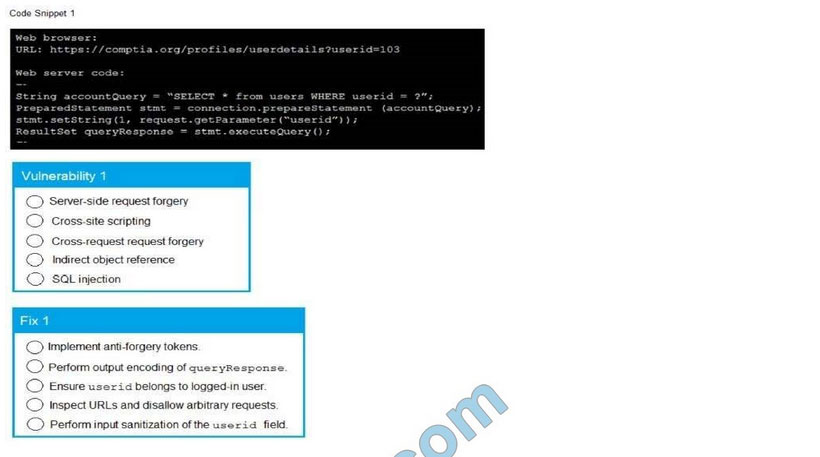
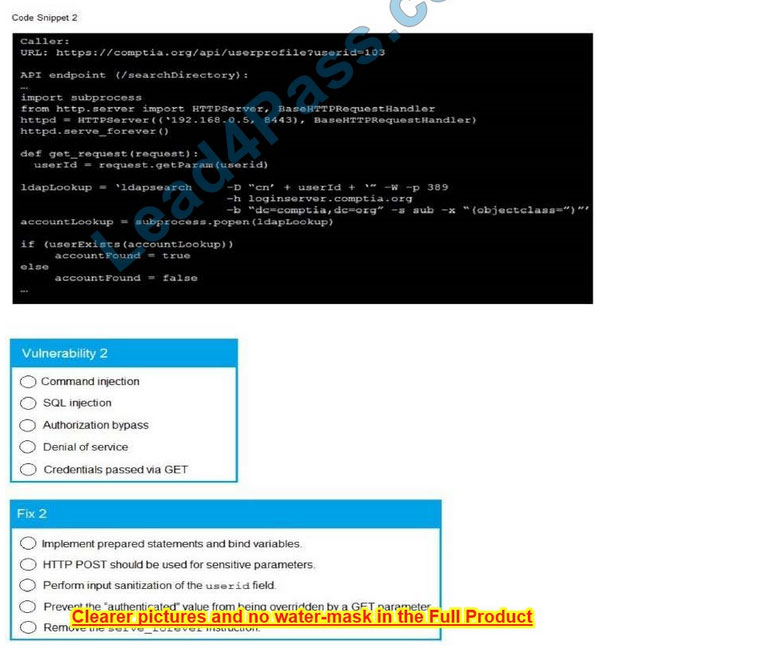
A. Check the answer in below.
Correct Answer: A
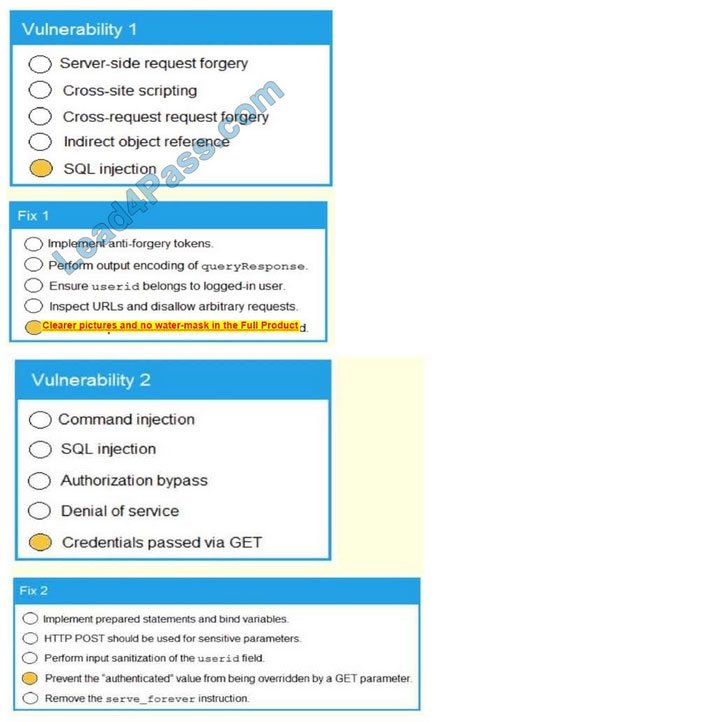
…
Download the CompTIA CAS-004 PDF for free sharing online:
https://drive.google.com/file/d/1gPzIc5NxyzqTe5jbFzvmofpUGr5d4CUr/
https://drive.google.com/file/d/1IbvnTbTz7x2VbxDQ1GHCSEII5xMN55Pn/
The above is only a part of CompTIA CAS-004 dumps exam questions and answers, you can use the above exam questions and answers to improve yourself, not only that, we welcome you to download the latest CompTIA CAS-004 dumps exam questions: https://www.leads4pass.com/cas-004.html (Total Questions: 267 Q&A), help you truly pass the CAS-004 CASP+ exam.
Cisco 300-435 ENAUTO Exam Plan: Using Cisco 300-435 Dumps
Use Cisco 300-435 Dumps for the best exam plan for you to successfully pass the Cisco 300-435 ENAUTO Exam.
Cisco 300-435 Dumps has PDF exam files, and VCE mock exam engine to help you complete the Cisco 300-435 ENAUTO exam plan.
Download Cisco 300-435 Dumps from Lead4Pass https://www.leads4pass.com/300-435.html, enjoy 365 days of free updates, help you save even more, and ultimately help you successfully pass the Cisco 300-435 ENAUTO Exam.
Try Cisco 300-435 Dumps exam questions for free:
Tips: The answer will be announced at the end of the article
Question 1:
What are two characteristics of RPC API calls? (Choose two.)
A. They can be used only on network devices.
B. They use only UDP for communications.
C. Parameters can be passed to the calls.
D. They must use SSL/TLS.
E. They call a single function or service.
Question 2:
Which two actions do Python virtual environments allow users to perform? (Choose two.)
A. Simplify the CI/CD pipeline when checking a project into a version control system, such as Git.
B. Efficiently port code between different languages, such as JavaScript and Python.
C. Run and simulate other operating systems within a development environment.
D. Quickly create any Python environment for testing and debugging purposes.
E. Quickly create an isolated Python environment with module dependencies.
Question 3:
What are two benefits of leveraging Ansible for automation of Cisco IOS XE Software? (Choose two.)
A. Ansible playbooks are packaged and installed on IOS XE devices for automatic execution when an IOS device reboots.
B. All IOS XE operating systems include Ansible playbooks for basic system administration tasks.
C. It is a device-independent method for automation and can be used with any type of device or operating system.
D. Ansible playbooks can be written from the IOS XE EXEC command line to configure the device itself.
E. It does not require any modules of the software except SSH to be loaded on the network device.
Question 4:
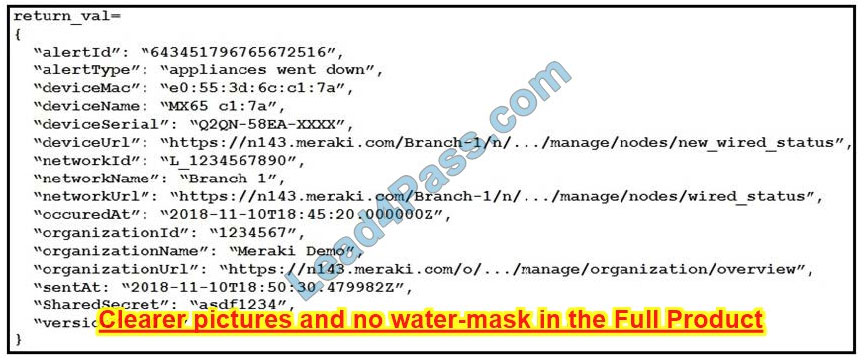
Refer to the exhibit. The task is to create a Python script to display an alert message when a Meraki MX Security Appliance goes down. The exhibit shows sample data that is received. Which Python snippet displays the device name and the time at which the switch went down?
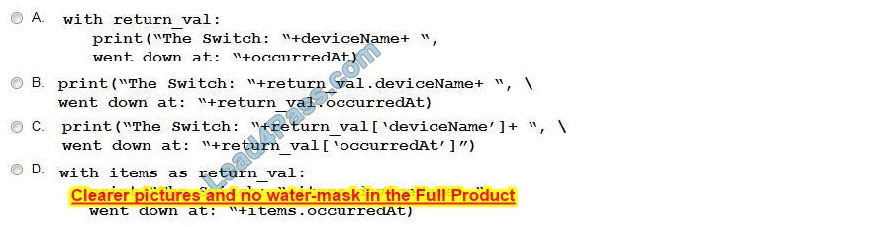
A. Option A
B. Option B
C. Option C
D. Option D
Question 5:

Refer to the exhibit. The goal is to write a Python script to automatically send a message to an external messaging application when a rogue AP is detected on the network.
The message should include the broadcast SSID that is in the alert.
A function called “send_to_application” is created, and this is the declaration:
send_to_application(message)
The exhibit also shows the data that is received by the application and stored in the variable return_val.
Which Python code completes the task?
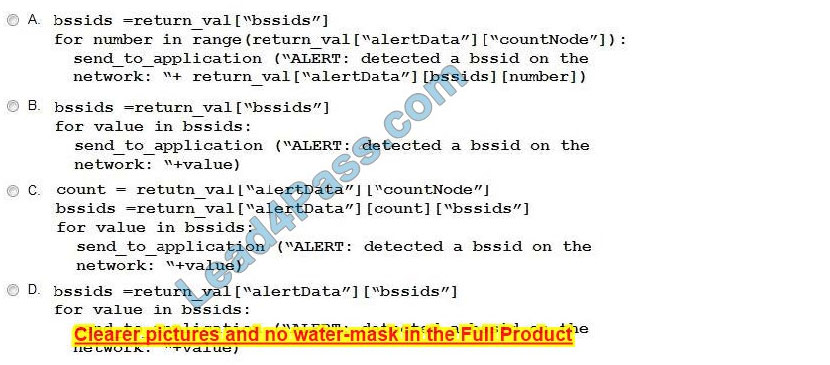
A. Option A
B. Option B
C. Option C
D. Option D
Question 6:
Which two features are foundations of a software-defined network instead of a traditional network? (Choose two.)
A. control plane and data plane are tightly coupled
B. build upon a robust software stack
C. requires device-by-device-level configurations
D. automated through expressed intent to a software controller
E. requires significant physical hardware resources
Question 7:
A new project called “device_status” must be stored in a central Git repository called “device_status” with the first file named “device_status.py”.
The Git repository is created using the account python_programmer. Which set of commands inserts the project into Git?

A. Option A
B. Option B
C. Option C
D. Option D
Question 8:
What are two characteristics of synchronous calls to APIs? (Choose two.)
A. They can be used only with certain programming languages.
B. They make your application less portable, so asynchronous calls are preferred.
C. They can add perceived latency to your application if data is not received.
D. They block until a response is returned from the servers.
E. They do not block while waiting for the API to be processed.
Question 9:

Refer to the exhibit. What is the result when running the Python scripts?
A. s1
B. s2
C. s1, s2, s3
D. s3
Question 10:
An engineer stores source code in a Git repository and is ready to develop a new feature. The production release is stored in the “master” branch.
Which commands create the new feature in a separate branch called “feature” and check out the new version?
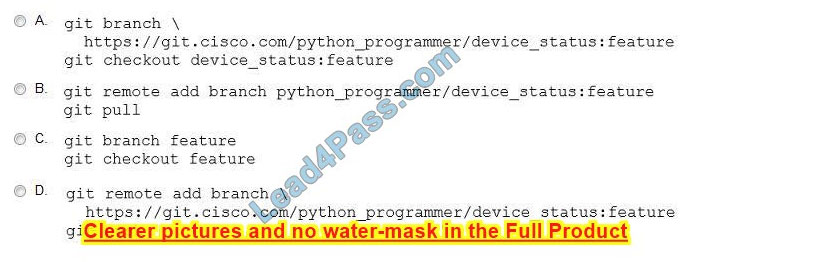
A. Option A
B. Option B
C. Option C
D. Option D
Question 11:

Refer to the exhibit. Which type of YANG container is described by the JSON instance provided?
A. interface-configurations
B. active
C. interface-name
D. description
Question 12:

Refer to the exhibit. Which NETCONF protocol operation is used to interact with the YANG model?
A.
B.
C.
D.
Question 13:

Refer to the exhibit. How many YANG models does the NETCONF operation interact with?
A. one
B. two
C. three
D. four
Question 14:
Which statement describe the difference between OpenConfig and native YANG data models?
A. Native models are designed to be independent of the underlying platform and are developed by vendors and standards bodies, such as the IETF.
B. Native models are developed by individual developers and designed to apply configurations on platforms.
C. OpenConfig models are developed by vendors and designed to integrate to features or configurations that are relevant only to that platform.
D. Native models are developed by vendors and designed to integrate to features or configurations that are relevant only to that platform.
Question 15:
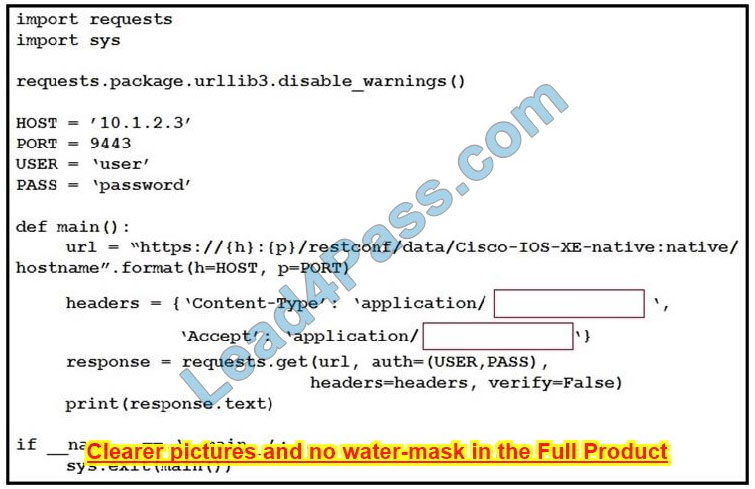
Refer to the exhibit. An engineer creates a Python script using RESTCONF to display hostname information. The code must be completed so that it can be tested. Which string completes the highlighted areas in the exhibit?
A. yang-data+json
B. yang +json
C. yang.data+json
D. JSON
Verify the answer:
| Numbers: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | AC | DE | AC | B | A | BD | A | CE | B | C | A | A | A | A | A |
Lead4Pass provides the perfect Cisco 300-435 ENAUTO exam plan, you just need to practice the complete Cisco 300-435 Exam Dumps https://www.leads4pass.com/300-435.html (122 Q&A), you are guaranteed 100% successful pass Cisco 300-435 ENAUTO exam.
Latest 2V0-71.21 dumps: Preparing for the Professional VMware Application Modernization exam
We confidently tell Exam Professional VMware Application Modernization candidates: that VMware 2V0-71.21 dumps have been updated to be the best material for you to take the Professional VMware Application Modernization exam and guarantee you 100% success in passing the exam.
Download the 2V0-71.21 dumps prepared by Lead4Pass for you https://www.leads4pass.com/2v0-71-21.html, then practice the 55 newly updated VMware 2V0-71.21 exam questions, then keep a good attitude to take the actual exam, Finally, you are sure to successfully pass the Professional VMware Application Modernization exam.
You can try the following VMware 2V0-71.21 exam questions online first:
Tips: The answer will be announced at the end of the article
QUESTION 1:
Which command is used to upgrade a Tanzu Kubernetes Grid Cluster (TKG) to a different kubernetes version?
A. tkg cluster upgrade –k8s-version
B. tkg upgrade cluster –kubernetes-version
C. tkg cluster upgrade –kubernetes-version
D. tkg upgrade cluster –version
QUESTION 2:
What is the command to find out the available node base operating system images?
A. kubectl get nodes
B. kubectl cluster-info
C. kubectl get virtualmachineclasses
D. kubectl get virtualmachineimages
QUESTION 3:
An architect is designing the infrastructure for multiple applications and needs to ensure isolation and control over resources and permissions assigned to each application team.
Which is the easiest and least expensive way to satisfy these requirements?
A. Use a dedicated Supervisor Cluster per application
B. Use dedicated vSphere Namespace per application
C. Use dedicated vSphere Pod per application
D. Use dedicated Kubernetes Deployments per each application
QUESTION 4:
Refer to the exhibit.
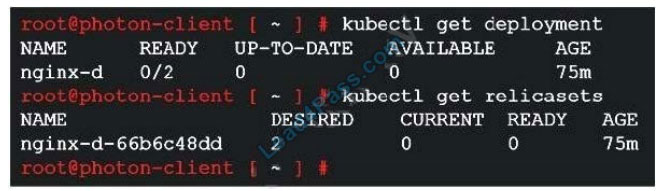
A developer deployed Nginx with 2 replicas on a new Tanzu Kubernetes Grid cluster, but the deployment did not move to a ready state.
What is the next step to troubleshoot?
A. kubectl describe pods
B. kubectl describe replicasets
C. kubectl get pods
D. kubectl get errors
QUESTION 5:
What are the pre-requisites for installing the Harbor registry in Tanzu Kubernetes Grid (TKG)?
A. Install Harbor helm from vCenter.
B. Deploy a management cluster, download and install the TKG extensions and Carvel tools.
C. Deploy a management cluster, launch the Harbor installation wizard.
D. Deploy a management cluster and install Tanzu Kubernetes Grid extensions.
QUESTION 6:
What is the MINIMUM required version of vSphere to install Tanzu Kubernetes Grid?
A. 6.0 Update 1
B. 6.5 Update 2
C. 6.7 Update 1
D. 6.7 Update 3
QUESTION 7:
Refer to the exhibit.
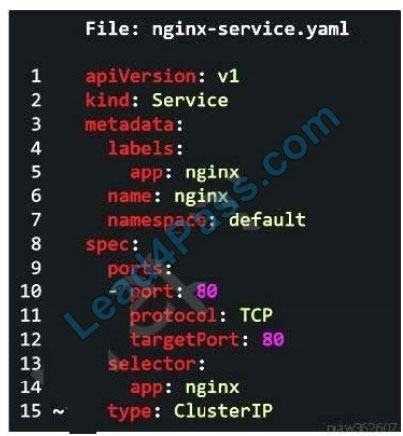
Which two options can be modified in order to expose Nginx app using Ingress Controller? (Choose two.)
A. Change type to IngressController
B. Change type to LoadBalancer
C. Change type to NodePort
D. Change type to HostPort
E. Change type to AntreaCni
QUESTION 8:
On VMware vSphere with Tanzu, which attribute identifies the etcd Leader node using the vSphere Client?
A. amount of memory resources
B. number of Networks
C. number of IP addresses
D. amount of compute resources
QUESTION 9:
What is the period of time to consider DISCONNECTED state for a cluster in Tanzu Mission Control?
A. 3 minutes
B. 1 minute
C. 2 minutes
D. 5 minutes
QUESTION 10:
Which upgrade method can be used for an ‘in-place’ Kubernetes update?
A. Run “kubectl patch” command against a Tanzu Kubernetes cluster
B. Change the VirtualMachineClass on a Tanzu Kubernetes cluster
C. Change the number of control plane nodes
D. Change the StorageClass on a Tanzu Kubernetes cluster
QUESTION 11:
How are Tanzu Kubernetes clusters upgraded?
A. Deploy a new cluster with upgraded Kubernetes release
B. Rolling upgrades
C. Clusters are only upgraded offline
D. In-place upgrade for each node
QUESTION 12:
Which two roles are required to attach clusters in Tanzu Mission Control? (Choose two.)
A. cluster.attach.admin
B. clustergroup.attach.admin
C. clustergroup.edit
D. clusters.admin
E. cluster.admin
QUESTION 13:
Which is the correct statement describing the characteristic of a pod?
A. Pod is the smallest entity managed by Docker.
B. Pod can contain only one container.
C. Containers in a pod start and stop together.
D. Pod is deployed directly on the virtual machine.
……
Verify the answer:
| Numbers: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| Answers: | B | A | B | A | B | D | AD | C | A | A | B | CE | C |
[Google Drive] You can also download VMware 2V0-71.21 exam questions and answers online: https://drive.google.com/file/d/1TNVykBrtbz0UysuhU3DRe6nN8LCQe1oa/
The above VMware 2V0-71.21 exam questions are only to help you warm up, then you should practice the latest and complete 2V0-71.21 exam questions: https://www.leads4pass.com/2v0-71-21.html (55 Q&A), guarantee you’re first trying Successfully passed the Professional VMware Application Modernization exam.
Latest Lead4Pass 2v0-51.21 Dumps for Professional VMware Horizon 8.X Exam Prep

Lead4Pass 2v0-51.21 Dumps has been updated to the latest version, including 60 exam questions and answers, you just need to practice each question carefully to ensure you successfully pass the Professional VMware Horizon 8.X Exam.
As the best preparation for the Professional VMware Horizon 8. X Exam, Lead4Pass not only provides the latest exam questions and answers but also gives you free 365-day updates to help you save even more.
You only need to visit: https://www.leads4pass.com/2v0-51-21.html (PDF+VCE), you can view the latest updated 2v0-51.21 Dumps, then candidates need to choose any mode and download 2v0-51.21 exam preparation.
Exam 2V0-51.21: Professional VMware Horizon 8.x
Vendor: VMware
Exam Code: 2V0-51.21
Exam Name: Professional VMware Horizon 8. X
Certification: VCP-DTM 2022
Language: English
Number of Questions: 60
Duration: 125 Minutes
Passing Score: 300
Format: Multiple Choice, Multiple Choice Multiple Selection, Drag and Drop, Matching, Hot Area
Pricing: $250 USD
Not only that, candidates can enjoy the VMware 2v0-51.21 online practice:
Tips: The answer will be announced at the end of the article
QUESTION 1:
End-users are complaining that they are frequently being asked for credentials when opening additional apps.
Which step should the administrator take to resolve the issue?
A. Configure SSO Timeout by modifying the Global Settings in Horizon Administrator.
B. Configure Session Timeout by modifying the Client Settings in Horizon Client.
C. Configure a time limit by modifying the Horizon GPO.
D. Configure Desktop Timeout by modifying the Pool Settings in Horizon Administrator.
QUESTION 2:
DRAG DROP
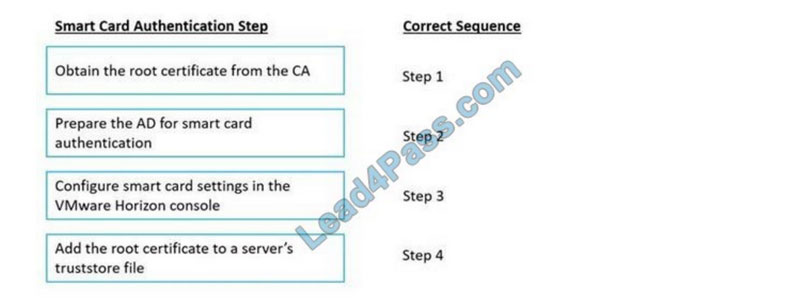
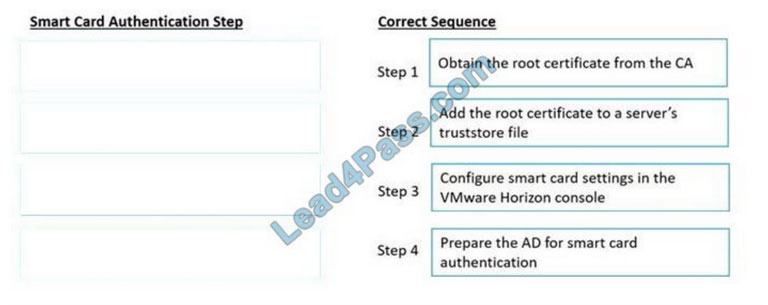
Drag and drop the high-level configuration steps for smart card authentication on the left into the correct sequential order on the right.
Select and Place:
Correct Answer:
QUESTION 3:
An administrator is tasked with allowing managers to request desktops and changes to desktops for their employees.
What VMware solution can be used to meet this requirement?
A. vRealize Operations
B. Horizon Automated Pools
C. vRealize Automation
D. Horizon Help Desk
QUESTION 4:
Which two steps must be completed in order to expand a writable volume? (Choose two.)
A. Select Volumes > Writables > Select Volume > Expand.
B. Modify the snapvol.cfg to reflect the new size.
C. Select Volumes > Writables > Select Volume > Update Writable.
D. Specify a size that is at least 1MB larger than the current size of the volume.
E. Specify a size that is at least 1GB larger than the current size of the volume.
QUESTION 5:
An administrator wants to ensure users can access an application that uses .NET 3.0 for desktops available on Horizon On-premises and on Horizon Cloud Service on Microsoft Azure.
Which two options would achieve this requirement? (Choose two.)
A. Create a ThinApp package and provision it with App Volumes.
B. Install the application on the primary image.
C. Copy the vmdk and .json file to the Azure storage.
D. Capture the application in App Volumes.
E. Copy the vhd and .json file to the Azure storage.
QUESTION 6:
After creating a new desktop pool that contains customization specifications, a Horizon administrator sees the following message in the VMware Horizon event database:
Provisioning error occurred for Machine Machine_Name: Customization failed for Machine
Which two could be the cause of the issue? (Choose two.)
A. The customization specification has been renamed or deleted.
B. Desktops can only be customized after the end user logs into the virtual machine.
C. The compute account of the template has been removed from the Active Directory.
D. The administrator does not have sufficient permissions to access the customization specification.
E. Desktop pool provisioning is disabled.
QUESTION 7:
Which can be used to make sure only certain Connection Servers are used for a Global Entitlement?
A. Category Folders
B. Home sites
C. Tags
D. Access Groups
QUESTION 8:
An administrator sees a lot of instant-clone template VM\’s that are not in use anymore in vCenter.
What tool needs to be used to clean up old templates?
A. iccleanup.cmd
B. icunprotect.cmd
C. vdmadmin.exe
D. icmaint.cmd
QUESTION 9:
Which of the following statements are true about Application Profiler?
A. VMware Dynamic Environment Manager Agent and the Application Profiler cannot be installed on the same machine.
B. Application Profiler is installed using VMware Dynamic Environment Manager Enterprise Setup Wizard and explicitly selecting local drive installation.
C. Application Profiler is installed automatically when installing VMware Dynamic Environment Manager FlexEngine.
D. Application Profiler is installed automatically when installing the Dynamic Environment Manager Management Console.
QUESTION 10:
An administrator configured a virtual machine to use an NVIDIA card but the virtual machine is not starting up.
What could be the cause of the issue? (Choose two.)
A. No suitable host could be found.
B. Not all memory has been reserved on the VM.
C. Not all CPUs have been reserved on the VM.
D. The Desktop Pool doesn\’t support 3D cards.
E. 3D graphics cannot be used with local storage.
QUESTION 11:
A new Horizon environment has gone into production. External sessions are disconnected after a
random period of time.
The following information has been documented by the administrator:
Internal and external users are able to connect to their desktops.
External sessions connect via a Unified Access Gateway.
Users are immediately able to reconnect but will be disconnected again in a few minutes.
Internal sessions, connected directly to the desktops, are not impacted.
While the session remains connected, all expected functionality works properly.
What could be the cause of this issue?
A. A misconfigured network load balancer is in front of the Unified Access Gateway appliances.
B. A misconfigured network load balancer is in front of the Connection Servers.
C. Required firewall ports are not open in front of the Connection Servers.
D. Required firewall ports are not open in front of the Unified Access Gateway appliances.
QUESTION 12:
Refer to the exhibit.
An administrator is creating an automated desktop pool of full clones. When prompted to select a template, the administrator sees the detail shown in the exhibit.
Which two combined actions should the administrator perform to be able to continue with the creation of a desktop pool? (Choose two.)
A. Open vSphere Client, select the golden image virtual machine and convert to template.
B. Open vSphere Client, select the golden image virtual machine and take a snapshot.
C. Enter the golden image virtual machine name in the Template Filter and select the template virtual machine.
D. Open vSphere Client, select the golden image virtual machine and remove all snapshots.
E. Refresh the Select template view and select the template virtual machine.
QUESTION 13:
Which two required distributions should be installed on a Linux machine that will be used as a multi-session host? (Choose two.)
A. Peppermint OS
B. RHEL Workstation
C. Solaris Linux
D. SUSE Enterprise Server
E. Ubuntu
Verify the answer:
| Numbers: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| Answers: | C | IMAGE | B | AE | DE | AD | D | D | B | AB | C | DE | BE |
Download Free VMware 2v0-51.21 Online Practice Questions: https://drive.google.com/file/d/1B0aQS4XNjPPbZkDk0IJvt_MUpKdsN5qu/
Lead4Pass 2v0-51.21 Dumps is the best solution for Professional VMware Horizon 8.X exam, because 2v0-51.21 Dumps has complete coverage of Professional VMware Horizon 8.X exam questions,
Click here to download the Latest Lead4Pass 2v0-51.21 Dumps now, you can be sure to pass the exam 100%.
Use the latest 300-910 dumps to help you pass the Cisco DEVOPS certification exam

Using 300-910 dumps can help you successfully pass the Cisco DEVOPS certification exam on your first attempt.
Because 300-910 dumps have many success advantages:
- Lightweight Learning Tool (PDF+VCE)
- More free usage time (365 days Free Update)
- Covers all Cisco DEVOPS practical exam questions and answers, with explanations of difficult problems
- Have a professional Cisco technical team service
So why not use 300-910 dumps to help you easily and successfully pass the exam? And Lead4Pass, as the provider of 300-910 dumps, has many years of industry reputation, is the industry leader, and is trustworthy, what else do you have to worry about?
Therefore, it is strongly recommended that you use the 300-910 dumps exam material https://www.leads4pass.com/300-910.html, which is up to date throughout the year, to prepare you for a career leap.
More detailed 300-910 DEVOPS certification information:
Vendor: Cisco
Exam Code: 300-910
Exam Name: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)
Certification: Cisco Certified DevNet Professional
Duration: 90 minutes
Languages: English
Price: $300 USD
Number of Questions: 55-65
300-910 dumps: https://www.leads4pass.com/300-910.html
Cisco 300-910 exam questions online practice test:
Tips: Verify the answer at the end of the article
Question 1:
Which two practices help make the security of an application a more integral part of the software development lifecycle? (Choose two.)
A. Add a step to the CI/CD pipeline that runs a dynamic code analysis tool during the pipeline execution.
B. Add a step to the CI/CD pipeline that runs a static code analysis tool during the pipeline execution.
C. Use only software modules that are written by the internal team.
D. Add a step to the CI/CD pipeline to modify the release plan so that updated versions of the software are made available more often.
E. Ensure that the code repository server has enabled drive encryption and stores the keys on a Trusted Platform Module or Hardware Security Module.
Question 2:
A CI/CD pipeline that builds infrastructure components using Terraform must be designed. A step in the pipeline is needed that checks for errors in any of the .tf files in the working directory. It also checks the existing state of the defined infrastructure.
Which command does the pipeline run to accomplish this goal?
A. terraform plan
B. terraform check
C. terraform fmt
D. terraform validate
Question 3:
Configuration changes to the production network devices are performed by a CI/CD pipeline. The code repository and the CI tool are running on separate servers. Some configuration changes are pushed to the code repository, but the pipeline did not start.
Why did the pipeline fail to start?
A. The CI server was not configured as a Git remote for the repository.
B. The webhook call from the code repository did not reach the CI server.
C. Configuration changes must be sent to the pipeline, which then updates the repository.
D. The pipeline must be started manually after the code repository is updated.
Question 4:
A new version of an application is being released by creating a separate instance of the application that is running the new code. Only a small portion of the user base will be directed to the new instance until that version has been proven stable.
Which deployment strategy is this example of?
A. recreate
B. blue/green
C. rolling
D. canary
Question 5:
Which description of a canary deployment is true?
A. deployment by accident
B. deployment that is rolled back automatically after a configurable amount of minutes
C. deployment relating to data mining development
D. deployment to a limited set of servers or users
Question 6:
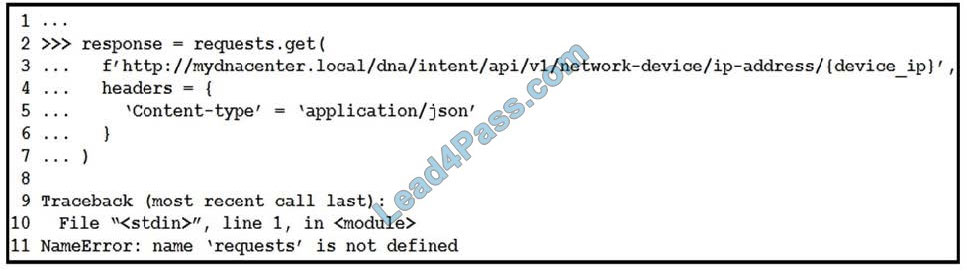
Refer to the exhibit. What is causing the request code to fail?
A. Rython3 is not compatible with requests.
B. The requests library is not imported.
C. The requests library is not installed.
D. The requests coming into stdin fail because device_ip cannot be parsed.
Question 7:
A DevOps engineer wants to build an application implementation based on the CI/CD pipeline model. Which service should be used to provide hosted continuous service for open and private projects?
A. Ansible
B. pyATS
C. Genie CLI
D. Travis CI
Question 8:
Which two actions help limit the attack surface of your Docker container? (Choose two.)
A. Run only a single service in each container.
B. Run all services in a single image.
C. Use version tags for base images and dependencies.
D. Use Kali Linux as a base image.
E. Download images over HTTPS supporting sites.
Question 9:
A DevOps engineer has built a container to host a web server and it must run as an executable. Which command must be configured in a Dockerfile to accomplish this goal?
A. ENTRYPOINT
B. ENTRYPOINT [“/usr/sbin/apache2ctl”, “-D”, “FOREGROUND”]
C. ENTRYPOINT [“BACKGROUND”, “-D”, “/usr/sbin/apache2ctl”]
D. ENTRYPOINT {usr/sbin/apache2ctl}
Question 10:
A Microservices architecture pattern has been applied and the system has been architected as a set of services. Each service is deployed as a set of instances for throughput and availability.
In which two ways are these services packaged and deployed? (Choose two.)
A. Service instances must be isolated from one another.
B. Service must be independently deployable and scalable.
C. Service is written using the same languages, frameworks, and framework versions.
D. Service must be dependent, deployable, and scalable.
E. Service instances do not need to be isolated from one another.
Question 11:

Refer to the exhibit. What is the reason for this error message?
A. The required dependencies for the urllib3 module are not installed.
B. The requests module is not installed.
C. The required dependencies for the requests module are not installed.
D. The site-packages directory has been corrupted.
Question 12:
ConfigMap keys have been mapped to different file names using the volumes.configMap.items field. What is the result if a wrong ConfigMap key is specified?
A. The default path is not used.
B. The volume is not created.
C. The volume is created.
D. The volume is created with errors.
Question 13:
What are the two benefits of Infrastructure as Code? (Choose two.)
A. It enables continuous integration.
B. It allows for management control.
C. It ensures consistency.
D. It improves application monitoring.
E. It reduces risk.
Question 14:
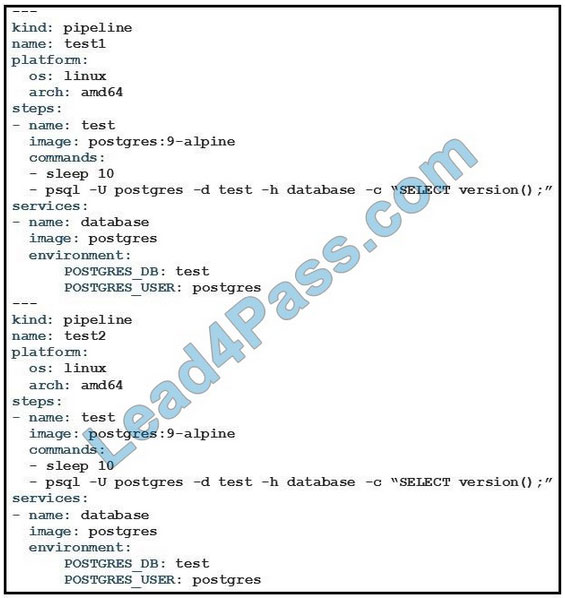
Refer to the exhibit. What is the user doing with Drone in this automated test?
A. testing Alpine Linux versus Ubuntu Linux
B. testing a PostgreSQL DB against multiple architectures
C. testing only the amd64 architecture
D. testing PostgreSQL deployment in an Alpine Linux VM
Question 15:
An interface on a router as a Layer 3 link has been configured to another device by updating an Ansible playbook that is executed via a CI/CD pipeline. The Ansible playbook was written to push the configuration change using the ios_config module.
Which automated test validates that the interface is functioning as it should?
A. Add a pipeline step that runs the playbook a second type. If it does not modify the device on the second run, then the interface is correctly configured.
B. Automated testing is already built in because the playbook execution is successful only after Ansible validates that it applied the change.
C. Add a pipeline step that captures and parses the packet flow for the interface.
D. Add a pipeline step that captures and parses the show IP interface output so that the operational state can be referenced.
……
Verify answer:
| Numbers: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | AE | D | C | D | D | B | D | CE | A | AB | B | A | CE | D | B |
DevNet Professional certification includes: Core exam and Concentration exams, Cisco DEVOPS certification exam is one of the Concentration exams certification exam,
Concentration exams can be chosen arbitrarily, the Core exam (350-901 DEVCOR) is the only one.
Select Lead4Pass 300-910 dumps https://www.leads4pass.com/300-910.html,
Helping you 100% pass the Cisco DEVOPS certification exam. All DevNet Professional certification programs are available in Lead4Pass and can ensure that you pass the exam with a high score.
VMware 1V0-81.20 Dumps Update [2022] Associate VMware Security Best Exam Materials

VMware 1V0-81.20 Dumps have been updated as 2022 Associate VMware Security Best Exam Materials to help you pass the target exam with ease.
1V0-81.20 is the Associate VMware Security exam code, 1V0-81.20 Dumps are reviewed by the Lead4Pass VMware expert team, for candidates’ knowledge of VMware security solutions, And the candidate’s ability to provide entry-level support for the security features of NSX-T Data Center, Workspace ONE, and Carbon Black Cloud ensures that you can successfully pass the Associate VMware Security certification exam on your first try.
Download 1V0-81.20 Dumps: https://www.leads4pass.com/1v0-81-20.html, complete all practice questions carefully, and then take the Associate VMware Security certification exam:
Vendor: VMware
Exam Code: 1V0-81.20
Exam Name: Associate VMware Security
Certification: VCTA-SEC 2021 / VCTA-SEC 2022
Language: English
Duration: 120 Minutes
Number of Questions: 55
Passing score: 300 (VMware exams are scaled on a range from 100-500, with the determined raw cut score scaled to a value of 300.)
Format: Multiple Choice, Multiple Choice Multiple Selection, Drag and Drop, Matching, Proctored
Pricing: $125 USD
You can also try the 1V0-81.20 online test first:
Verify answers at the end of the test
QUESTION 1:
In VMware Carbon Black Cloud, which reputations have the highest priority during analysis?
A. Known Priority
B. Trusted Allow List
C. Company Allow List
D. Ignore
QUESTION 2:
Which VMware application enrolls an endpoint into Workspace ONE?
A. Workspace ONE Web
B. CB Defense Sensor
C. VMware Horizon Client
D. Workspace ONE Intelligent Hub
QUESTION 3:
When filtering firewall rules after selecting an object to filter by, which four columns do the filter search? (Choose four.)
A. Services
B. Action
C. Protocol
D. Log
E. Applied To
F. Source
G. Destinations
QUESTION 4:
When using VMware Carbon Black Live Response, what command will show all active processes?
A. dir
B. list
C. ls
D. ps
QUESTION 5:
Which parameter ensures an endpoint will stay connected with the designated VMware Carbon Black Cloud tenant?
A. Company Code
B. Organization Group ID
C. Device Serial Number
D. User ID
QUESTION 6:
Refer to the exhibit.
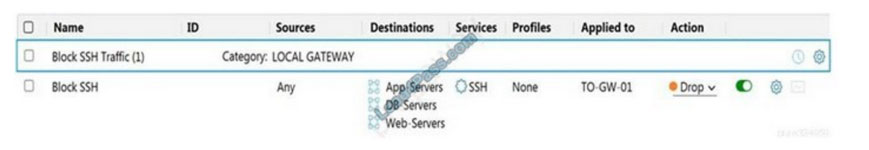
Which statement is true about the firewall rule?
A. It is a gateway firewall applied to a Tier-0 gateway that drops traffic on port 22
B. It is a distributed firewall applied to App-Services, DB-Servers, and Web-Servers that rejects traffic on port 22
C. It is a distributed firewall applied to App-Services, DB-Servers, and Web-Servers that drops traffic on port 22
D. It is a gateway firewall applied to a Tier-0 gateway that rejects traffic on port 22
QUESTION 7:
A technician has been asked to confirm a specific browser extension does not exist on any endpoint in their environment.
Which is the VMware Carbon Black tool to use for this task?
A. Enterprise EDR
B. EDR
C. Audit and Remediation
D. Endpoint Standard
QUESTION 8:
Which attack technique probes the environment for openings on devices or the firewall?
A. Port Scan
B. Denial of Service
C. Living off the Land
D. Phishing
QUESTION 9:
What is the safe course of action for a USB disk of unknown ownership and origin?
A. Do not connect the USB to any computer as it may be a USB Killer device
B. Connect the USB device to your computer and allow the DLP software to protect it
C. Connect the USB to a non-Windows device and examine it
D. Connect the USB to an air-gapped system and examine it
QUESTION 10:
In VMware Carbon Black Cloud Endpoint Standard, which items are available in the Event view?
A. Hashes, Reputations
B. Emails, Policies, OS, Locations
C. Connection, IP/Port
D. IDs, Indicators/TTPs
QUESTION 11:
Micro-segmentation is under which pillar of trust in VMware\’s 5 pillars of Zero Trust?
A. User
B. Session/Transport
C. Application
D. Device
QUESTION 12:
Which VMware product allows you to query an endpoint like a database?
A. VMware NSX-T Data Center
B. VMware Carbon Black Audit and Remediation
C. VMware Workspace ONE UEM
D. VMware Carbon Black Endpoint Standard
QUESTION 13:
What types of hosts are supported for hosting both NSX-T Data Center managers and host transport nodes?
A. vSphere ESXi 6.7U1 or higher, KVM on CentOS Linux
B. vSphere ESXi 6.7U1 or higher, KVM on RHEL 7.6, Ubuntu 18.04.2 LTS
C. vSphere ESXi 6.5, KVM on RHEL 7.6, Ubuntu 18.04.2 LTS
D. vSphere ESXi 6.7U1 or higher, CentOS KVM 7.6, RHEL KVM
……
Verify answer:
| Number: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| Answers: | B | D | A E F G | B | D | A | A | A | D | C | B | C | A |
Download the above 1V0-81.20 online test questions:https://drive.google.com/file/d/1uHz9-UXJMVB1FWcALS0q5dWLvdN0QCfQ/
Share some 1V0-81.20 online test questions for free to verify your current learning situation, click here to download 1V0-81.20 Dumps and complete the complete practice to help you easily pass the Associate VMware Security certification exam.
[Updated 2022] Cisco CCNA 200-301 exam exercise questions and the latest updates 200-301 dumps
Cisco 200-301 is the latest Cisco CCNA exam code for 2020.
The new Cisco CCNA exam is a brand new test! Itexamcourses offers the latest 200-301 exam tips, 200-301 pdf, and 200-301 free exams Questions to help you improve your skills! Improve the exam pass! Lea4pass is our partner and they have the most authoritative testing experts! Easily pass the exam, select the complete Cisco 200-301 exam dumps https://www.leads4pass.com/200-301.html (148 Q&As) [Updated 2022] Total Questions: 824 Q&A. The latest update exam dumps. Guaranteed to be effective and authentic! Lead4Pass updates throughout the year to ensure you successfully pass the target exam on your first attempt!
[Updated 2022] Cisco 200-301 Exam Video
Itexamcourses Exam Table of Contents:
- Latest Cisco 200-301 google drive
- Effective Cisco 200-301 exam practice questions
- Lead4Pass Year-round Discount Code
- What are the advantages of Lead4pass?
Latest Cisco 200-301 google drive
[PDF] Free Cisco 200-301 pdf dumps download from Google Drive: https://drive.google.com/open?id=1y3-4Ph-8p5cEUUA_2jEik2sifhfnqfx3
[Updated 2022] https://drive.google.com/file/d/1bEpMJLRNFn4w7PqhOXcF23dWnrUoLX35/
200-301 CCNA – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/ccna-200-301.html
[Updated 2022] Cisco Certified Network Associate 200-301 exam question and answers
QUESTION 1:
Refer to the exhibit.
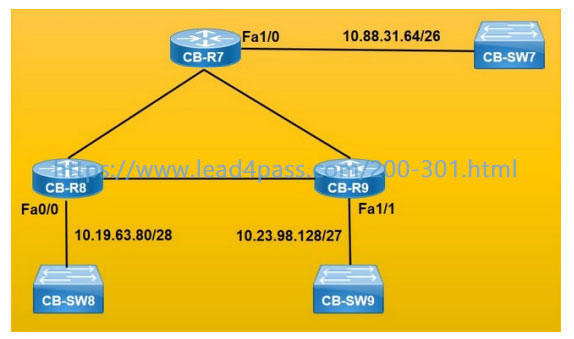
Each router must be configured with the last usable IP address in the subnet. Which configuration fulfills this requirement?
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: C
QUESTION 2:
Refer to the exhibit.
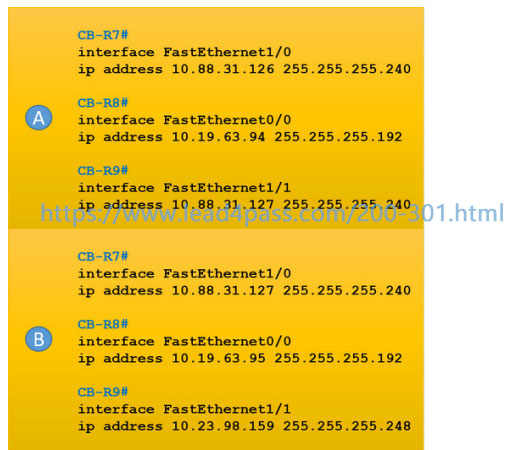
An engineer is asked to config-router CB-R1 so that it forms an OSPF single-area neighbor relationship with CB-R2.
Which command sequence must be implemented to configure the router?
A. router ospf 10
network 10.0.0.0 0.0.0.3 area 0
network 10.0.2.0 0.0.0.255 area 0
B. router ospf 10
network 10.0.0.0 0.0.0.3 area 0
network 10.0.1.0 0.0.0.255 area 0
C. router ospf 10
network 10.0.0.0 0.0.0.3 area 0
network 10.0.2.0 255.255.255.0 area 0
D. router ospf 10
network 10.0.0.0 0.0.0.252 area 0
network 10.0.1.0 0.0.0.255 area 0
Correct Answer: B
QUESTION 3:
Refer to the exhibit.
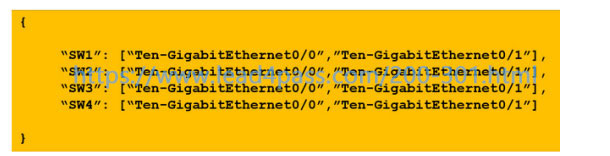
How many JSON objects are represented?
A. 1
B. 2
C. 3
D. 4
Correct Answer: D
QUESTION 4:
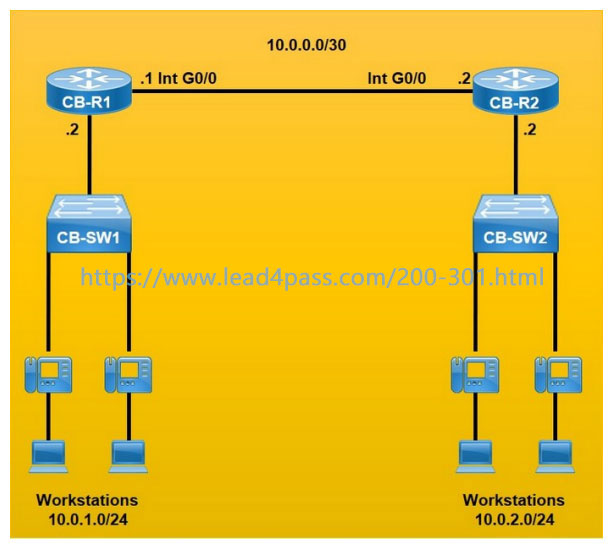
Refer to the exhibit.
Which two configurations would be used to create and apply a standard access list on R1, so that only the 10.0.70.0/25 network devices are allowed to access the internal database server? (Choose two)
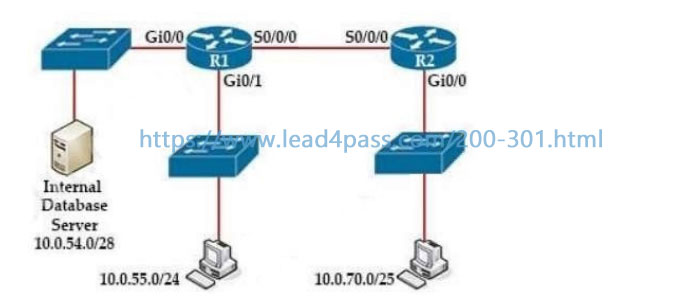
A. R1(config)# interface GigabitEthernet0/0
R1(config-if)# ip access-group 5 out
B. R1(config)# access-list 5 permit 10.0.54.0 0.0.1.255
C. R1(config)# interface Serial0/0/0
R1(config-if)# ip access-group 5 in
D. R1(config)# access-list 5 permit 10.0.70.0 0.0.0.127
E. R1(config)# access-list 5 permit any
Correct Answer: AD
QUESTION 5:
Refer to the exhibit. What is the next hop for traffic entering R1 with a destination of 10.1.2.126?
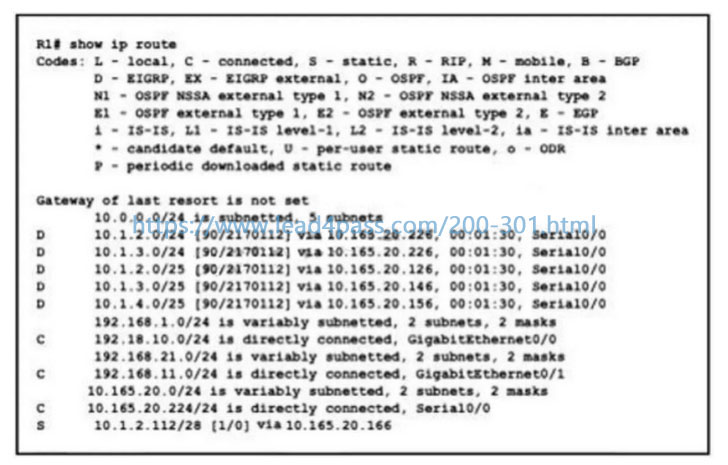
A. 10.165 20.126
B. 10.165.20.146
C. 10.165.20.166
D. 10.165 20.226
Correct Answer: D
……
[Updated 2022]: Get more free CCNA 200-301 dumps questions and labs
Latest updates Cisco CCNA 200-301 exam practice questions
QUESTION 1
What are two characteristics of a controller-based network? (Choose two.)
A. It uses Telnet to report system issues.
B. The administrator can make configuration updates from the CLI.
C. It uses northbound and southbound APIs to communicate between architectural layers.
D. It decentralizes the control plane, which allows each device to make its own forwarding decisions.
E. It moves the control plane to a central point.
Correct Answer: CE
QUESTION 2
Which two actions influence the EIGRP route selection process? (Choose two.)
A. The advertised distance is calculated by a downstream neighbor to inform the local router of the bandwidth on the
link.
B. The router calculates the feasible distance of all paths to the destination route.
C. The router must use the advertised distance as the metric for any given route.
D. The router calculates the best backup path to the destination route and assigns it as the feasible successor.
E. The router calculates the reported distance by multiplying the delay on the exiting interface by 256.
Correct Answer: BD
QUESTION 3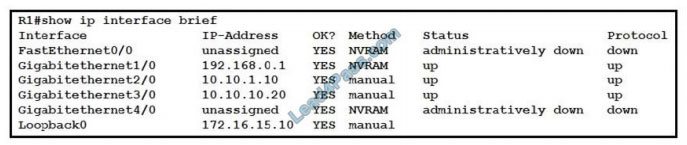
Refer to the exhibit. What does router R1 use as its OSPF router-ID?
A. 10.10.1.10
B. 10.10.10.20
C. 172.16.15.10
D. 192.168.0.1
Correct Answer: C
QUESTION 4
A frame that enters a switch fails the Frame Check Sequence. Which two interface counters are incremented? (Choose
two.)
A. input errors
B. frame
C. giants
D. CRC
E. runts
Correct Answer: AD
QUESTION 5
DRAG DROP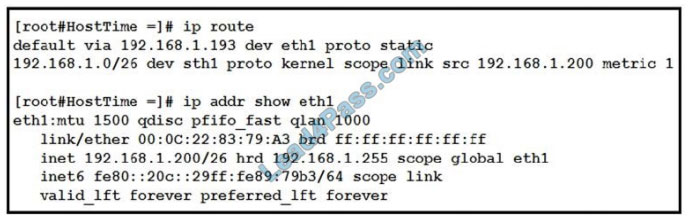
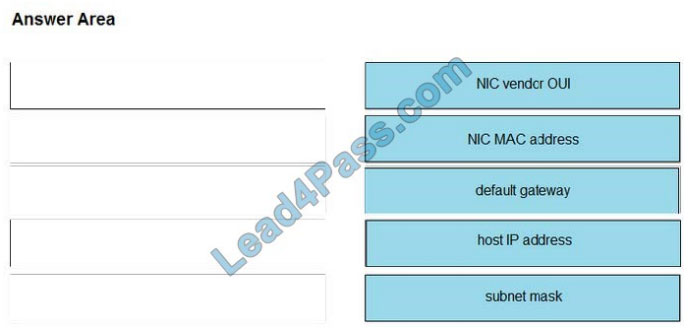
Refer to the exhibit. Drag and drop the networking parameters from the left onto the correct values on the right.
Select and Place:
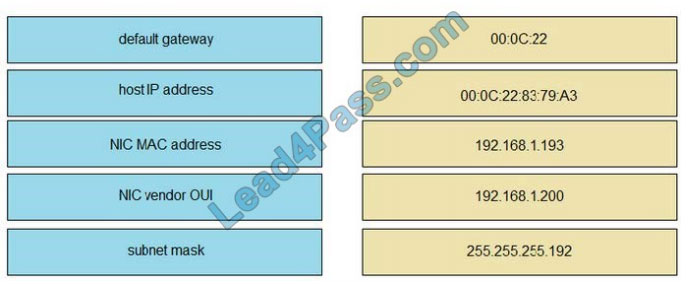
Correct Answer:
QUESTION 6
Refer to the exhibit.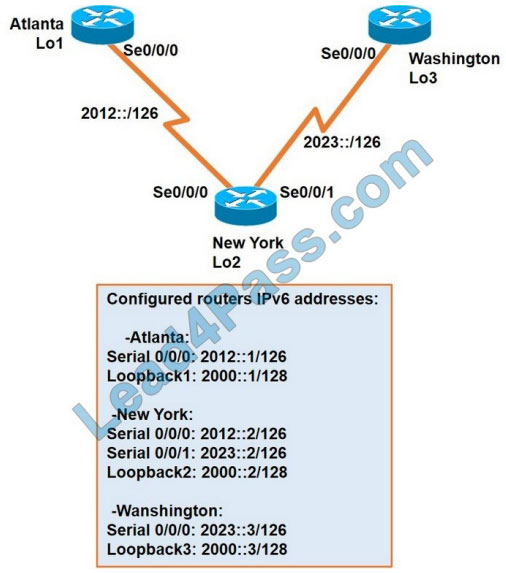
The New York router is configured with static routes pointing to the Atlanta and Washington sites.
Which two tasks must be performed so that the Serial0/0/0 interfaces on the Atlanta and Washington routers can reach
one another? (Choose two.)
A. Configure the ipv6 route 2023::/126 2012::1 command on the Atlanta router.
B. Configure the ipv6 route 2012::/126 2023::2 command on the Washington router.
C. Configure the ipv6 route 2012::/126 2023::1 command on the Washington router.
D. Configure the ipv6 route 2023::/126 2012::2 command on the Atlanta router.
E. Configure the ipv6 route 2012::/126 s0/0/0 command on the Atlanta router.
Correct Answer: BD
QUESTION 7
Which result occurs when PortFast is enabled on an interface that is connected to another switch?
A. Root port choice and spanning tree recalculation are accelerated when a switch link goes down.
B. After spanning tree converges, PortFast shuts down any port that receives BPDUs.
C. VTP is allowed to propagate VLAN configuration information from switch to switch automatically.
D. Spanning tree may fail to detect a switching loop in the network that causes broadcast storms.
Correct Answer: D
QUESTION 8
Which configuration is needed to generate an RSA key for SSH on a router?
A. Configure VTY access.
B. Configure the version of SSH.
C. Assign a DNS domain name.
D. Create a user with a password.
Correct Answer: C
QUESTION 9
Which design element is a best practice when deploying an 802.11b wireless infrastructure?
A. allocation nonoverlapping channels to access points that are in close physical proximity to one another
B. disabling TCP so that access points can negotiate signal levels with their attached wireless devices
C. configuring access points to provide clients with a maximum of 5 Mbps
D. setting the maximum data rate to 54 Mbps on the Cisco Wireless LAN Controller
Correct Answer: A
QUESTION 10
Which three are characteristics of an IPv6 anycast address? (Choose three.)
A. one-to-many communication model
B. one-to-nearest communication model
C. any-to-many communication model
D. a unique IPv6 address for each device in the group
E. the same address for multiple devices in the group
F. delivery of packets to the group interface that is closest to the sending device
Correct Answer: BEF
A new address type made specifically for IPv6 is called the Anycast Address. These IPv6 addresses are global
addresses, these addresses can be assigned to more than one interface unlike an IPv6 unicast address. Anycast is
designed to send a packet to the nearest interface that is a part of that anycast group. The sender creates a packet and
forwards the packet to the anycast address as the destination address which goes to the nearest router. The nearest
router or interface is found by using the metric of a routing protocol currently running on the network. However in a LAN
setting the nearest interface is found depending on the order the neighbors were learned. The anycast packet in a LAN
setting forwards the packet to the neighbor it learned about first.
QUESTION 11
Which IPv6 address type communication between subnets and cannot route on the Internet?
A. link-local
B. unique local
C. multicast D. global unicast
Correct Answer: B
QUESTION 12
How does STP prevent forwarding loops at OSI Layer 2?
A. TTL
B. MAC address forwarding
C. Collision avoidance
D. Port blocking
Correct Answer: D
QUESTION 13
Which command prevents passwords from being stored in the configuration as plain text on a router or switch?
A. enable secret
B. enable password
C. service password-encryption
D. username cisco password encrypt
Correct Answer: C
(2022-)Latest Lead4Pass Year-round Discount Code

Why Lead4Pass is the industry leader
Lead4Pass has many years of exam experience! Finishing school is your goal! Getting good employment conditions is your goal! Our goal is to help more people pass the Cisco exam! Exams are a part of life but important!
In the study, you need to make great efforts, to sum up, the study! Trust Lead4Pass if you can’t easily pass because of exam details! We have the most authoritative cisco exam experts! The most efficient pass rate! We are an industry leader!
Summarize:
- Latest Cisco 200-301 google drive
- Effective Cisco 200-301 exam practice questions
- Lead4Pass Year-round Discount Code
- What are the advantages of Lead4pass?
This blog shares the latest Cisco 200-301 exam tips, 200-301 exam questions, and answers! 200-301 pdf, 200-301 exam video! You can also practice the test online! Lead4pass is the industry leader! Select Lead4Pass 200-301 dumps Pass Cisco 200-301 exams “Cisco Certified Network Associate”. Help you successfully pass the 200-301 exam.
The latest update Lead4pass 200-301 exam dumps: https://www.leads4pass.com/200-301.html (148 Q&As) [Updated 2022] Total Questions: 824 Q&A
[Q1-Q13 PDF] Free Cisco 200-301 pdf dumps download from Google Drive: https://drive.google.com/open?id=1y3-4Ph-8p5cEUUA_2jEik2sifhfnqfx3
[Updated 2022] https://drive.google.com/file/d/1bEpMJLRNFn4w7PqhOXcF23dWnrUoLX35/
2V0-31.21 Dumps V12.02 Is the Latest Version For Professional VMware vRealize Automation 8.3 Exam
Are you preparing to take the 2V0-31.21 Professional VMware vRealize Automation 8.3 exam? You just need to have the latest version 2V0-31.21 Dumps prepared for the actual VMware 2V0-31.21 exam. Now, the 2V0-31.21 dumps V12.02 has been released via VMware subject matter experts.
As the latest version of the Professional VMware vRealize Automation 8.3 exam, Lead4Pass 2V0-31.21 dumps V12.02 real exam questions and accurate Answers ensure you can successfully pass the Professional VMware vRealize Automation 8.3 2V0-31.21 real-world exam.
Before getting the full 2V0-31.21 dumps V12.02 recommended by subject matter experts, read the 2V0-31.21 free dumps below:
QUESTION 1:
Which vRealize Automation service allows an administrator to import released cloud templates and Amazon Web Services CloudFormation templates that users can deploy? (Choose the best answer.)
A. Service Broker
B. Cloud Assembly
C. Orchestrator
D. Code Stream
Correct Answer: A
QUESTION 2:
An administrator creates a custom form for an RHEL cloud template. A user reports only being able to see the standard form when requesting the cloud template.
Which step should the administrator take to resolve this issue?
A. Enable the custom form feature in Cloud Assembly.
B. Enable the custom form feature in Service Broker.
C. Enable the custom form in the project for the RHEL cloud template.
D. Enable the custom form for the RHEL cloud template.
Correct Answer: D
QUESTION 3:
Refer to the exhibit.

An administrator configures a lease policy, (“1 Day Lease”), for the App-Dev project so that machines have a starting lease of one day and a maximum lease of five days.
The following week, the administrator is assigned a ticket to address an issue with machines being deleted without any notifications being received. The administrator requests a new machine deployment through the App-Dev project\’s service catalog.
Given the one-day lease period, the administrator expects to receive an automated “Lease Expiring” system immediately following a successful deployment; however, the email is not received.
The administrator checks the deployment that has just been created (as displayed in the exhibit) and confirms that the “1 Day Lease” policy has been correctly applied.
Which action should the administrator take to resolve this issue? (Choose the best answer.)
A. Add an email endpoint.
B. Configure the notification email Server.
C. Ensure the users have notifications enabled.
D. Run the Configure mail workflow.
Correct Answer: B
QUESTION 4:
What is the function of Action-Based Extensibility (ABX)? (Choose the best answer.)
A. It provides the capability to migrate content between instances of vRealize Automation.
B. It provides efficient capacity and cost management for managed virtual machines.
C. It provides intelligent remediation and integrated compliance for security patches.
D. It provides a way to execute stateless function, which contains reusable parameterized actions.
Correct Answer: D
QUESTION 5:
Which command should an administrator run to ensure data integrity before a snapshot or backup of a vRealize Automation appliance? (Choose the best answer.)
A. /opt/scripts/deploy.sh ––onlyClean
B. /opt/scripts/svc-stop.sh
C. vracli status deploy
D. kubectl logs –n prelude
Correct Answer: B
QUESTION 6:
Which deployment action is performed using the vRealize Easy Installer?
A. Register vRealize Automation with vCenter Single Sign-On
B. Install vRealize Operations
C. Install vCenter Server
D. Register vRealize Automation with VMware Identity Manager
Correct Answer: D
QUESTION 7:
The administrator has installed SaltStack Config using the “edu” tenant from vRealize Suite Lifecycle Manager.
How would the administrator access the SaltStack Config service?
A. Log in to https://
B. Log in to https://edu.
C. Log in to https://salt.
D. Log in to https://edu.
Correct Answer: B
QUESTION 8:
Which two actions can be performed against a Cloud Assembly machine-based deployment? (Choose two.)
A. Run machine-level actions including adding a USB controller.
B. Change lease for the deployment.
C. Resize the deployment.
D. Change machine IP address assignment to DHCP.
E. Power off the deployment.
Correct Answer: CE
QUESTION 9:
As part of a greenfield deployment, an administrator needs to set up an NSX-T Data Center cloud account.
Which user role is required to create an NSX-T Data Center cloud account in vRealize Automation? (Choose the best answer.)
A. Cloud Assembly Administrator
B. Cloud Assembly User
C. Orchestrator Administrator
D. NSX-T Data Center Enterprise Administrator
Correct Answer: A
QUESTION 10:
An administrator must restrict the number of memory resources available for a specific group of users.
On which component would the administrator configure this?
A. Flavor Mappings
B. Cloud Accounts
C. Projects
D. Cloud Zones
Correct Answer: C
Reference: https://blogs.vmware.com/management/2020/03/vra-resource-limits.html
QUESTION 11:
Which kubectl command should be run to find the Kubernetes authentication method? (Choose the best answer.)
A. kubectl describe pod
B. kubectl –n prelude describe pod
C. kubectl describe secrets
D. kubectl explain
Correct Answer: C
QUESTION 12:
Which type of cloud account is configured during the Quickstart process?
A. Google Cloud Platform
B. Microsoft Azure
C. VMware Cloud an AWS
D. VMware vCenter Server
Correct Answer: D
QUESTION 13:
Which command should an administrator run to check the status of vRealize Automation services? (Choose the best answer.)
A. vracli org-oauth-apps
B. kubectl –n prelude get pods
C. kubectl cluster-info –n prelude
D. vracli status
Correct Answer: B
……
2V0-31.21 free Dumps online download:https://drive.google.com/file/d/1TwfjbcO-Hz2Ryd1BSdfY7kudotx__oBb/view?usp=sharing
View 93 Q&A – 2V0-31.21 dumps: Latest Version For Professional VMware vRealize Automation 8.3 Exam
2V0-72.22 Dumps [2022] Take the Professional Develop VMware Spring exam
Let’s get started!

You need to know the 2V0-72.22 Professional Develop VMware Spring exam details and top recommendations:
Number of Questions: 60
Language: English
Time: 130 Minutes
Passing score: 300 (scaled)
Format: Single and Multiple Choice, Proctored
Pricing: $250.00 USD
2V0-72.22 dumps: https://www.leads4pass.com/2v0-72-22.html
VMware: https://www.vmware.com/learning/certification/vcp-am-dev-exam.html
You need to know why 2V0-72.22 Dumps are used:
2V0-72.22 Dumps has developed 60 core exam questions and answers based on expertise in the key features of Spring and Spring Boot, as well as candidates’ ability to quickly build and deliver production-ready applications using Spring features.
You can use a 2V0-72.22 PDF file or a 2V0-72.22 VCE learning engine to prepare for your Professional Develop VMware Spring exam and ensure that you exceed your expected grades to achieve professional Develop VMware Spring certification.
So let me show you some of the 2V0-72.22 Dumps questions:
QUESTION 1:
Which three statements are advantages of using Spring\’s Dependency Injection? (Choose three.)
A. Dependency injection can make code easier to trace because it couples behavior with construction.
B. Dependency injection reduces the start-up time of an application.
C. Dependencies between application components can be managed externally by the components.
D. Configuration can be externalized and centralized in a small set of files.
E. Dependency injection creates tight coupling between components.
F. Dependency injection facilitates loose coupling between components.
Correct Answer: BDE
Reference: https://raviroza.com/tight-coupling-and-loose-coupling-in-spring-framework/
QUESTION 2:
Which two options are valid optional attributes for Spring\’s @Transactional annotation? (Choose two.)
A. isolation
B. writeOnly
C. nestedTransaction
D. readWrite
E. propagation
Correct Answer: AE
Reference: https://learningviacode.blogspot.com/2012/10/attributes-in-springs-declarative.html
QUESTION 3:
Which statement is true? (Choose the best answer.)
A. @ActiveProfiles is a class-level annotation that is used to instruct the Spring TestContext Framework to record all application events that are published in the ApplicationContext during the execution of a single test.
B. @ActiveProfiles is a class-level annotation that you can use to configure how the Spring TestContext Framework is bootstrapped.
C. @ActiveProfiles is a class-level annotation that you can use to configure the locations of properties files and inlined properties to be added to the set of PropertySources in the Environment for an ApplicationContext loaded for an integration test.
D. @ActiveProfiles is a class-level annotation that is used to declare which bean definition profiles should be active when loading an ApplicationContext for an integration test.
Correct Answer: D
Reference: https://docs.spring.io/spring-framework/docs/4.2.x/spring-framework-reference/html/integrationtesting.html
QUESTION 4:
What is a Spring Boot starter dependency? (Choose the best answer.)
A. A setting for specifying which code you want Spring Boot to generate for you.
B. A specific POM which you must build to control Spring Boot\’s opinionated runtime.
C. A pre-existing model project you can download and use as the basis of your project.
D. An easy way to include multiple, coordinated dependencies related to a specific technology, like web or JDBC.
Correct Answer: D
Reference: https://developer.ibm.com/tutorials/j-spring-boot-basics-perry/
QUESTION 5:
Which three types of objects can be returned from a JdbcTemplate query? (Choose three.)
A. Generic MapS
B. Simple types (int, long, String, etc)
C. JSONObject
D. User-defined types
E. Properties
F. XMLObject
Correct Answer: BDE
QUESTION 6:
Which two options will inject the value of the daily. limit system property? (Choose two.)
A. @Value(“#{daily.limit}”)
B. @Value(“$(systemProperties.daily.limit)”)
C. @Value(“$(daily.limit)”)
D. @Value(“#{systemProperties[`daily.limit\’]}”)
E. @Value(“#{systemProperties.daily.limit}”)
Correct Answer: BD
QUESTION 7:
In which three ways are Security filters used in Spring Security? (Choose three.)
A. To provide risk governance.
B. To drive authentication.
C. To manage application users.
D. To provide a logout capability.
E. To enforce authorization (access control).
F. To encrypt data.
Correct Answer: BDE
Reference: https://www.javadevjournal.com/spring-security/spring-security-filters/
QUESTION 8:
Which two statements are true regarding Spring Boot Testing? (Choose two.)
A. @TestApplicationContext is used to define additional beans or customizations for a test.
B. Test methods in a @SpringBootTest class are transactional by default.
C. @SpringBootTest is typically used for integration testing.
D. Test methods annotated with @SpringBootTest will recreate the ApplicationContext.
E. @SpringBootTest without any configuration classes expects there is only one class annotated with
@SpringBootConfiguration in the application.
Correct Answer: CD
QUESTION 9:
Refer to the exhibit.

It is a Java code fragment from a Spring application. Which statement is true with regard to the above example? (Choose the best answer.)
A. This syntax is invalid because the result of the getBean() method call should be cast to ClientService.
B. It will return a bean called ClientService regardless of its id or name.
C. This syntax is invalid because the bean id must be specified as a method parameter.
D. It will return a bean of the type ClientService regardless of its id or name.
Correct Answer: D
QUESTION 10:
Refer to the exhibit.

Which statement is true? (Choose the best answer.)
A. CustomerRepository should be a class, not an interface.
B. JPA annotations are required on the Customer class to successfully use Spring Data JDBC.
C. An implementation of this repository can be automatically generated by Spring Data JPA.
D. A class that implements CustomerRepository must be implemented and declared as a Spring Bean.
Correct Answer: C
QUESTION 11:
Which two statements are true concerning constructor injection? (Choose two.)
A. If there is only one constructor the @Autowired annotation is not required.
B. Constructor injection only allows one value to be injected.
C. Constructor injection is preferred over field injection to support unit testing.
D. Construction injection can be used with multiple constructors without @Autowired annotation.
E. Field injection is preferred over constructor injection from a unit testing standpoint.
Correct Answer: CE
QUESTION 12:
Which two statements are correct regarding Spring Boot auto-configuration? (Choose two.)
A. Auto-configuration uses @Conditional annotations to constrain when it should apply.
B. Auto-configuration could apply when a bean is missing but not when a bean is present.
C. Auto-configuration is applied by processing candidates listed in META-INF/spring.factories.
D. Auto-configuration could apply when a bean is present but not when a bean is missing.
E. Auto-configuration is applied before user-defined beans have been registered.
Correct Answer: DE
QUESTION 13:
Refer to the exhibit.
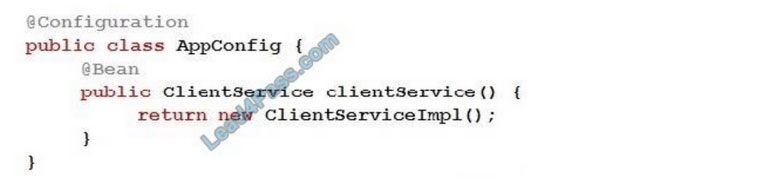
What is the id/name of the declared bean in this Java configuration class? (Choose the best answer.)
A. clientServiceImpl (starting with lowercase “c”)
B. clientServiceImpl (starting with uppercase “C”)
C. clientService (starting with lowercase “c”)
D. ClientService (starting with uppercase “C”)
Correct Answer: D
……
Download the above 2V0-72.22 Dumps questions online:https://drive.google.com/file/d/12An5-aHTf_DPNQt_sHg7fjW8UdF_bx20/view?usp=sharing
View 60 questions:
Finally, I wish you success with your first exam in advance!
New 5V0-22.21 Dumps Questions [2022] Best material for VMware vSAN 6.7 Expert Exam

The new 5V0-22.21 Dumps Questions are the best exam material to better prepare for the VMware vSAN 6.7 Specialist certification exam.
Our team of VMware experts has developed truly effective 5V0-22.21 Dumps exam questions and answers based on the exam details of the VMware vSAN 6.7 Specialist Certification Exam Designing, Implementing, and Managing VMware vSAN Environments.
Verified and reviewed 5V0-22.21 Dumps exam questions can help you successfully pass the VMware vSAN 6.7 Specialist exams on the first try. Lead4Pass offers a 100% guarantee on the newly updated 5V0-22.21 Dumps questions.
This will help you get VMware vSAN 6.7 Specialist Certificate (5V0-22.21) certification.
Check 5V0-22.21 Free Dumps To Verify The New 5V0-22.21 Dumps Questions
QUESTION 1
An administrator has discovered that space utilized by VMs does not decrease after deleting files and folders within the VMs. The administrator needs to be able to reclaim this space.
Which action could the administrator take to accomplish this task?
A. Disable Storage I/O Control for the vSAN cluster.
B. Reboot the VM to recreate the swap file.
C. Set the Object Space Reservation rule to 100%.
D. Enable TRIM/UNMAP for the vSAN cluster.
Correct Answer: D
QUESTION 2
After a server power failure, the administrator noticed the scheduled resyncing in the cluster monitor displays objects to be resynchronized under the pending category.
What are these objects in this category?
A. These objects belong to virtual machines, which are powered off.
B. Object resynchronization must be started manually.
C. There is too many objects to be synchronized.
D. The delay timer has not expired.
Correct Answer: B
QUESTION 3
A site administrator has determined that the site needs to upgrade all vSAN clusters to 7.0 U1. The vSAN administrator wishes to complete the update in the shortest amount of time possible. All virtual machines are assigned a storage policy where the “Failures to tolerate” is set to one or higher.
Which strategy should be used to achieve this goal?
A. Disable de-duplication and compression prior to the upgrade.
B. Perform a complete update, omitting the on-disk format update.
C. Select the “No data migration” maintenance mode option.
D. Update only select, mission-critical clusters.
Correct Answer: D
QUESTION 4
During yesterday\’s business hours, a cache drive failed on one of the vSAN nodes. The administrator reached out to the manufacturer and received a replacement drive the following day. When the drive failed, vSAN started a resync to ensure the health of data, and all objects are showing a healthy and compliant state. The vSAN administrator needs to replace the failed cache drive.
Which set of steps should the vSAN administrator take?
A. Remove the existing vSAN disk group, and physically replace the device. Then, check to verify that the ESXi host automatically detects the new device. Afterward, manually recreate the Disk Group.
B. Physically replace the failed cache device, and vSAN will automatically create a new disk group. Then, remove the disk group with the failed device.
C. Physically replace the failed cache device, and vSAN will automatically allocate the storage. Then, rebalance the cache layer.
D. Place the disk group into maintenance mode, and select Full Data Migration. Then, physically replace the failed cache device. Afterward, vSAN will rebuild the disk group automatically.
Correct Answer: B
QUESTION 5
After a recent data loss event, the IT department plans to deploy a DR site using vSphere Replication with vSAN providing the storage backend.
The architect would like to know how many components will be created based on the following configuration:
2x 100 GB VMDK RAID 1 vSAN Storage Policy 4x Point in Time snapshots
How many components will be created?
A. 32
B. 24
C. 16
D. 8
Correct Answer: B
QUESTION 6
What are two purposes of a vSAN storage policy (Choose two.)
A. To determine the vSAN encryption level
B. To enable TRIM/UNMAP
C. To define how the VM storage objects are provisioned
D. To guarantee the required level of service
E. To enable deduplication and compression
Correct Answer: CD
QUESTION 7
A single capacity disk fails within a vSAN 7.0 U1 cluster running with a “compression-only” configuration enabled. The vSAN administrator must recognize the platform impact that has occurred and take steps to correct it.
Which action should the vSAN administrator take?
A. The hardware failure will impact the entire disk group, so the vSAN administrator will need to remove and recreate the disk group following the replacement of the failed storage device.
B. The hardware failure will stop the running workloads, so the vSAN administrator will need to disable the compression-only configuration, replace the failed capacity device, and then re-create the disk group.
C. The hardware failure will impact all disk groups within the ESXi host, so the vSAN administrator will need to manually remove the ESXi node from the vSAN Cluster, replace the failed capacity device, and then re-create the disk group.
D. The hardware failure will only impact the specific capacity disk, so the vSAN administrator will need to remove and replace the failed capacity device.
Correct Answer: D
QUESTION 8
A 100GB virtual disk object has this storage policy assigned to it:
Site disaster tolerance: None – standard cluster Failures to Tolerate: 1 failure – RAID-1 (Mirroring) Number of disk stripes per object: 3
What is the maximum amount of raw vSAN storage capacity consumed by this virtual disk?
A. 200GB
B. 100GB
C. 300GB
D. 600GB
Correct Answer: B
QUESTION 9
Which option, if any, is the default option to Enable Maintenance Mode on a vSAN host?
A. Ensure accessibility.
B. No data migration.
C. Full data migration.
D. There is no default option. The administrator must select an option.
Correct Answer: D
QUESTION 10
Which two prerequisites are required before a vSAN administrator is able to use the vSAN Performance Diagnostics feature? (Choose two.)
A. The vSAN Performance Service must be enabled.
B. The vSAN Health Service must be turned on.
C. vSAN File Services must be disabled before running vSAN Performance Diagnostics.
D. Participation in the Customer Experience Improvement Program (CEIP) must be enabled.
E. Verbose Mode must be enabled when configuring vSAN monitoring.
Correct Answer: AB
QUESTION 11
An organization is facing vSAN storage capacity challenges on one of their vSAN enabled clusters, while other vSAN enabled clusters are underutilized. The current vSAN version is 7.0 U1.
Which vSAN feature should be used to resolve this challenge in the quickest way?
A. vSAN HCI Mesh
B. vSAN Replication
C. vSAN Stretched Clusters
D. vSAN Datastore(s)
Correct Answer: A
QUESTION 12
An administrator wants to check the vSAN cluster health during the maintenance window while the vCenter Server is offline.
What are two ways to complete this task? (Choose two.)
A. HCIBench
B. ESXi system logs on vSAN datastore
C. esxcli
D. vSphere Host Client
E. esxtop
Correct Answer: CD
……
5V0-22.21 Free Dumps Online Download:https://drive.google.com/file/d/15YWkqdIMSodSz9RdahWzabztZLX5CqwQ/view?usp=sharing
Lead4Pass 5V0-22.21 Dumps Questions Specifically designed to correspond to the exam details of the VMware vSAN 6.7 Specialist Certification Exam Designing, Implementing, and Administering VMware vSAN Environments Formulated with really valid 5V0-22.21 Dumps exam questions and answers.
Use the new 5V0-22.21 Dumps: https://www.leads4pass.com/5v0-22-21.html. Helping you pass the VMware vSAN 6.7 Specialist certification exam with ease.